Hello there! Your guy Zokomon is back. Since it’s the beginning of 2025—a year full of new aspirations and goals—let’s dive into the Most Important Tools for Bug Bounty in 2025.
The last tool on this list is a game-changer for answering your questions and can even assist in finding big bugs like RCEs and SQL injections!
Remember: These tools are here to assist you in finding bugs—they won’t find the bugs for you. It’s your talent, skill, and determination that uncover vulnerabilities. Think of these tools as your followers. You pave the way, and they’ll help you reach the bug! 😊
1) Sublist3r
The first step in bug bounty hunting is reconnaissance. The better your reconnaissance, the better your chances of finding bugs that others might have missed.
Sublist3r is a fantastic tool for subdomain enumeration. It’s not as powerful as Amass, but it’s much faster and offers accurate and precise results. Sublist3r works in a wordlist-style format, gathering a bunch of subdomains quickly.
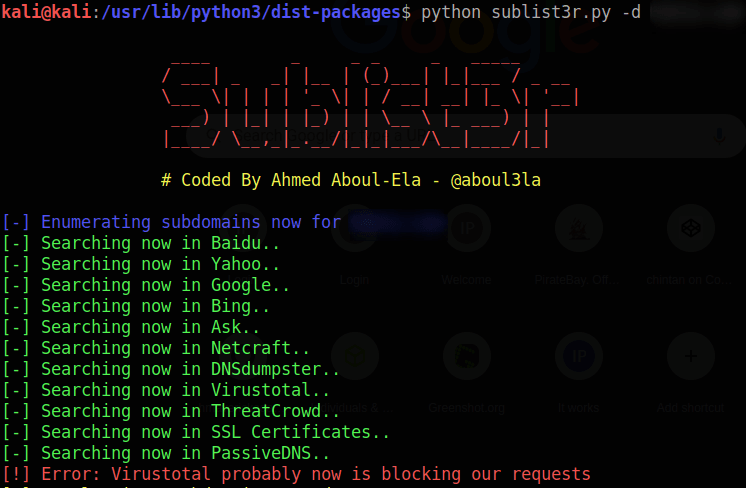
If speed isn’t an issue, you can also try Amass. While it’s slower, it’s one of the most powerful enumeration tools available.
You can download it from here…
2) httpx
Now that you’ve gathered a list of subdomains, the next challenge is visiting each one. Manually checking them all is time-consuming, especially when most will return 404 errors (though it’s worth testing some 404s with suspicious URLs like /login or /admin).
Here’s where httpx comes in handy.
httpx -sc -l urls.txt
i) -sc: Displays the status codes (e.g., 200, 404, 502, 301, etc.).
ii) -l: Refers to the list of URLs saved in a file (e.g., urls.txt)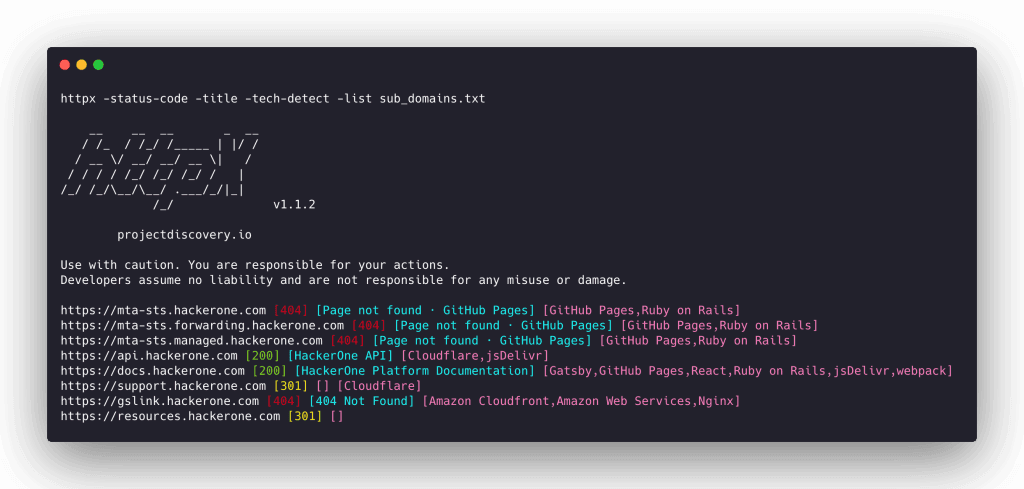
Focus on URLs returning 200 (OK) status codes. Only check 404s if something about the URL seems suspicious.
Tip: httpx can also take screenshots of the front end of websites, but I recommend visiting valid pages manually for more accuracy.
You can download it from here…
3) Dirsearch or Dirbuster
Sometimes, you’ll need more detailed reconnaissance to uncover the directory structure of a web application. This helps you find hidden endpoints that might lead to vulnerabilities.
Both Dirsearch and Dirbuster are great for this.
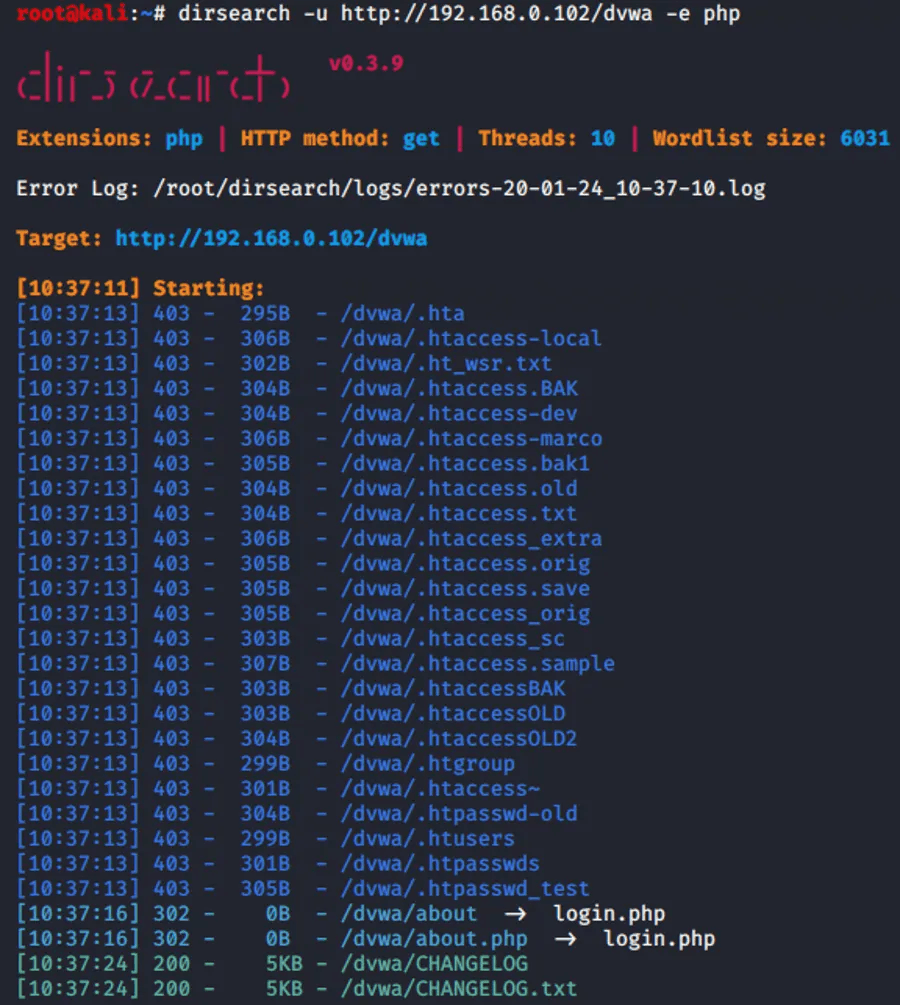
python3 dirsearch.py -u
#You can also specify certain file types to focus your search and narrow down results.Pro Tip: Keep Dirsearch or Dirbuster in your bug bounty toolkit at all times—you’ll need them more often than you think.
You can download it from here…
4) Ethical Hacker GPT
And now, for the tool I’ve been most excited to share: Ethical Hacker GPT.
This tool has revolutionized my approach to bug bounty hunting. Instead of spending hours searching blogs and forums for specific answers, you can get instant, detailed explanations by asking the right questions.
What You Can Do with Ethical Hacker GPT:
Paste complex web application data and ask for explanations.
Use prompts like:
i) “Step-by-step explanation of this request.”
ii) “Explain this like I’m 10 years old.”
Ask it to generate scripts or test cases for specific CVEs (Common Vulnerabilities and Exposures).
Example Prompt:
“I am testing an Apache server for vulnerabilities and need to know how CVE-2024-40898 works. What are the prerequisites for testing it? Can you also generate a Python script for testing this CVE?”Tip:
Ethical Hacker GPT can even assist in hacking—but only in a lab environment or with permission. Always ensure your prompts are ethical and within the scope of your testing! 😉
You can know how to use it by reading my previous article third point here…
A Final Word
These are the tools you’ll use daily as a bug bounty hunter. While there are advanced tools out there, mastering these basics will take you far. Bug bounty hunting in 2025 is all about staying relevant with evolving technology, and tools like Ethical Hacker GPT ensure you don’t fall behind.
Remember: With great power comes great responsibility. Always test in a lab environment and respect others’ property. Unauthorized testing can have serious consequences.
Conclusion
That’s it for now! These tools are essential for bug bounty hunting, but if you know of any other must-have tools, feel free to comment below. Let’s grow and learn together as a community.
Stay curious, keep learning, and may the bugs be ever in your favor! 😊


