📢 Overview of the Flickr Account Takeover Vulnerability
A major security flaw in Flickr’s authentication system exposed Flickr Account Takeover Vulnerability. Security researcher Lauritz Holtmann discovered that Flickr’s integration with Amazon Cognito API had serious misconfigurations that allowed attackers to hijack accounts without needing a password.
In this blog, we’ll break down the vulnerability, how it was exploited, and what Flickr did to fix it.
🔍 How the Vulnerability Worked
The issue originated from Flickr’s OAuth-based login system, which relied on Amazon Cognito for authentication. The misconfiguration allowed attackers to bypass security checks and gain access to user accounts.
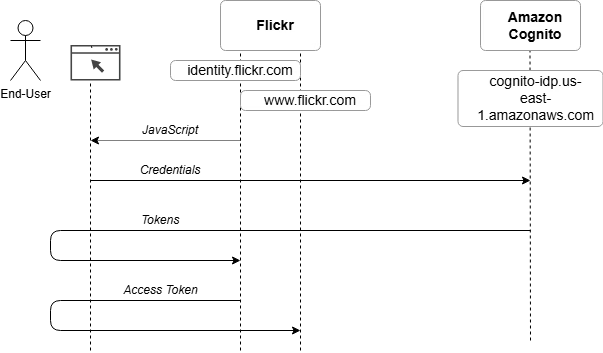
Here’s what went wrong:
1️⃣ Improperly Configured Identity Pools: Cognito was set up incorrectly, allowing unauthorized access to session tokens.
2️⃣ ID Token Manipulation: Attackers could obtain a valid identity token for one account and use it to access another user’s account.
3️⃣ Lack of Proper Validation: Flickr failed to verify that the Cognito-issued tokens actually belonged to the requesting user.
As a result, an attacker could generate a valid session token for any Flickr account, effectively bypassing the password login process.
⚠️ How Hackers Could Exploit This Flaw
An attacker could take over any Flickr account in three simple steps:
1️⃣ Obtain a valid Cognito ID token (either from their own account or by intercepting one).
2️⃣ Modify the token to impersonate another user’s account.
3️⃣ Use the modified token to log in as the victim—without needing their password.
Once inside, the hacker had full control. They could:
–> Steal private photos and messages
✔️ Lock out the real user by changing login credentials
✔️ Use the account for phishing or spam attacks
This type of vulnerability is critical because it completely bypasses traditional security measures like passwords and multi-factor authentication (MFA).
🛡️ How Flickr Fixed Flickr Account Takeover Vulnerability
After the vulnerability was reported, Flickr worked with Amazon to patch the flaw and secure its authentication system.
–> Fixed Identity Pool Permissions: Restricted token usage to only the intended accounts.
✔️ Implemented Strict Token Validation: Ensured that Cognito ID tokens match the logged-in user.
✔️ Enhanced OAuth Security: Added extra checks to prevent unauthorized account access.
These updates closed the loophole and prevented attackers from exploiting Cognito’s authentication tokens.
🚀 Lessons for Users and Developers
💡 For Users:
- Monitor your account activity regularly for unusual logins.
- Use unique passwords and enable 2FA where possible.
- Be cautious of phishing emails that may exploit authentication vulnerabilities.
💡 For Developers:
- Always validate authentication tokens to prevent impersonation attacks.
- Configure Amazon Cognito identity pools securely to avoid unauthorized access.
- Use server-side validation instead of relying solely on client-side authentication.
🔥 Final Thoughts
This vulnerability highlights the critical importance of proper authentication security. Even large platforms like Flickr can fall victim to misconfigurations that expose user accounts to takeovers.
You can read about it from the Author himself here…
With more services relying on third-party authentication, it’s crucial to audit security settings regularly to prevent similar flaws.
You can read my previous blog on “ Next.JS 9.1 CVSS Vulnerability “
💡 What are your thoughts on this vulnerability? Have you ever encountered authentication issues like this? Drop your comments below! 🚀


ev4d9f
Trattare l’artrosi per viaggiatori con Come usare Hondrolife per articolazioni è comodo.
Tubetto piccolo, facile da portare. Ordinato online
Community at 200 users brews ideas that ripple out unchecked.
EVM Networks
Вывел 120к на крипту — анонимно.
игровой клуб Лев
Вывел 35к ночью — пришло сразу.
игорный клуб Лев
Играю с планшета в кровати.
Удобно.
игровой клуб Лев
Бонус код MELBONUS — ещё 30% к депозиту
https://perang168.co/melbet-bonusy-pri-registracii-2025/
Реферальная программа — привёл друга,
получил 5к на счёт
https://cathelp.co.uk/promo-melbet-segodnya-registraciya-2025/
Джекпот в Hall of Gods — 5 млн, скрин в чате
https://removemagics.com/gamemelbet-obzor-melbet-2025/
Техподдержка помогла восстановить пароль
за 2 минуты
https://lacteosypastas.com/2025/10/20/promokod-melbet-besplatnaya-stavka-2025/
kraken darknet market
кракен онион
Thị trường nhà cái uy tín đổi thưởng ngày càng bùng nổ với vô số lựa chọn, nhưng liệu đâu là nền tảng thực sự đáng tin cậy? Nhiều người chơi đã phải học bài học đắt giá khi tham gia các nhà cái thiếu minh bạch: tiền thắng không thể rút, tài khoản bị khóa vô cớ, hay tỷ lệ trả thưởng không công bằng. Hãy cùng khám phá nhà cái 66b – một lựa chọn đang được đánh giá cao bởi cộng đồng người chơi nhờ tính minh bạch, bảo mật và đa dạng trò chơi.
kraken darknet
kraken официальный
Thực tế cho thấy, các vấn đề về giao dịch tại 188v com rất hiếm khi xảy ra. Theo thống kê, tỷ lệ giao dịch có vấn đề chỉ chiếm chưa đầy 0.5%, thấp hơn đáng kể so với mức trung bình ngành là 2-3%.
Бонусы Вулкан предлагаются в виде дополнительных баллов, денежных средств, фриспинов и ценных презентов.
адрес меги без тор
мега вывод
Thực tế cho thấy, các vấn đề về giao dịch tại asia slot365 rất hiếm khi xảy ra. Theo thống kê, tỷ lệ giao dịch có vấn đề chỉ chiếm chưa đầy 0.5%, thấp hơn đáng kể so với mức trung bình ngành là 2-3%.
Осознанность — мой главный урок за последний год
https://storeprofit.ru/
добавьте реальный маршрут доставки
https://777cargo.ru/
Всё про автополив из бочек с таймером — руки свободны
https://agro-zaschita.ru/
нравится, что не привязывается к компаниям
https://988cargo.ru/
ретейл и логистика — отличная связка
https://доставка-карго-из-китая.рф/
I get genuinely sad when a good puzzle ends
puzzle piece
Мой адвокат гооформление внж в испанииорит, что через год поднимут минимальный доход
кракен онлайн
vk1
Я подавал документы через ReloHelper — всё прошло гладко.
Они действительно помогают на каждом этапе, особенно
с переводами и справками. Рекомендую!
испания цифровой кочевник
Sảnh chơi bắn cá tại 188v battery tuy ra mắt đã lâu nhưng sức hút mang lại trong cộng đồng cược thủ chưa từng hạ nhiệt. Thành viên tham gia được hóa thân thành những ngư thủ thực thụ, chinh phục đa dạng loài sinh vật biển với nhiều mức độ khác nhau. Anh em cần chuẩn bị các dụng cụ hỗ trợ tương ứng, vũ khí hiện đại để có thể săn về cho mình những boss khủng, cơ hội kiếm số tiền lớn nhé.
Заходил через зеркало — работает идеально, без тормозов.
Темная тема спасает глаза ночью,
а меню слева очень удобное.
Уже поднял 15к на Dice, вывод одобрили за 20 минут!
drgn
Спасибо за советы по сварке тонкого металла —
теперь варю кузов машины без прожогов, всё ровно.
My page https://pakstore.ru/
Темпурный ролл с креветкой и тобикой
— отличный выбор для тех, кто любит яркие вкусы
Суши самовывоз
Thanks for finally writing about > How I made 2000$ using Flickr Account Takeover Bug!
→ Bug Bounty Blogs Spinmama Bonusy
Играю с работы через зеркало,
всё летает
Feel free to visit my blog – меллстрой казино
Популярный кракен маркетплейс обрабатывает более десяти тысяч ежедневных транзакций с криптовалютными платежами в Bitcoin, Monero и Ethereum валютах.
Драгон мани зеркало рабочее нашёл в их официальном канале
Feel free to visit my website; dragon money тактика
Кэшбэк каждую неделю реально спасает после неудачных серий
https://switchenergy.com.au/melbet-zerkalo-staraya-versiya-2025/
Uwielbiasz hazard? https://online-nv-casino.com: rzetelne oceny kasyn, weryfikacja licencji oraz wybor bonusow i promocji dla nowych i powracajacych graczy. Szczegolowe recenzje, porownanie warunkow i rekomendacje dotyczace odpowiedzialnej gry.
Никаких глюков в приложении за
месяц использования
https://www.rovertime.it/melbet-obzor-2025/
Вывод на крипту тоже есть, для тех кто в теме
https://www.instruingenieria.com/melbet-na-pk-obzor-2025/
Выводил вчера на карту, деньги пришли за 40 минут
https://www.versurft.com/2025/10/24/melbet-bk-obzor-2025-stavki-prognozy-bonusy/
Package efficiency when you buy tiktok views and likes saves resources. Bundled services offer better value than separate purchases while ensuring proportional engagement ratios.
Новинний портал Ужгорода https://88000.com.ua головні події міста, політика, економіка, культура, спорт та життя городян. Оперативні новини, репортажі, інтерв’ю та аналітика. Все важливе про Ужгород в одному місці, зручно з телефону та комп’ютера.
PlayJonny, häufig auch bekannt als playjonny bezeichnet, ist in den vergangenen Jahren als eine eine
von wichtigsten Seiten im Bereich Online-Casinos etabliert.
Die Plattform vereint aktuelle Technologie sowie
der einfachen UI, die sowohl für Neueinsteiger als auch Fortgeschrittene komfortabel navigierbar bleibt.
Besonders hervorzuheben bleibt das Angebot der
angebotenen Spiele, die von klassischen Spielautomaten inklusive Tischspiele bis hin zu Live-Erfahrungen reichen. Die
große Bandbreite gestaltet playjonny als einer guten Wahl für Nutzer, diejenigen Spaß als auch die Chance auf Gewinne erwarten. Zusätzlich setzt das Casino play jonny hohe Priorität auf Schutz
und Datenschutz, wodurch Gamer ihre Daten Zahlungen sicher durchführen können. Ein weiterer Vorteil von play
jonny casino ist die fortlaufende Erweiterung
der Spiele, sodass Nutzer immer neue Optionen ausprobieren können. Zusätzlich zur Auswahl
der Optionen überzeugt PlayJonny ebenfalls durch
besondere Funktionen, inklusive Boni, Loyalitätspunkten sowie
Aktionen, die den Spielspaß attraktiver gestalten. Summa summarum zeigt sich
klar, dass auch play jonny nicht lediglich ein normales Online-Casino darstellt,
sondern vielmehr ein Anbieter, welche auf die Bedürfnisse moderner Nutzer
zugeschnitten ist während Freude und Fairness bietet. Die Verbindung aus Nutzerfreundlichkeit, Vielfalt sowie Schutz gestaltet playjonny casino zu einem herausragenden Akteur im Online-Casino-Markt.
Свежая кракен тор ссылка публикуется в проверенных источниках с датой последнего обновления для информирования пользователей об актуальности адреса.
Криптографические технологии обеспечивают защищенный кракен через end-to-end шифрование всех коммуникаций, PGP защиту конфиденциальных данных и мультиподписные кошельки для средств.
Thanks for sharing. I read many of your blog posts, cool, your blog is very good. https://www.binance.info/ru-UA/register?ref=JVDCDCK4