Well, hello there! Zokomon here. Hope you’re having a great day. Today we will discuss Black Hat Hacking Explained: Techniques, Risks, and How It’s Done.
As discussed in my last blog (DeepSeek Chinese Propaganda tool), I shared how I started my bug bounty career. But I also mentioned that before bug bounty hunting, I learned only Black Hat hacking—things like DDoS attacks and WiFi hacking. Let’s just say those activities are more likely to earn you a ticket to the nearest police station than a paycheck! 😄
How It All Started
Back in my school days, I was fascinated by movies with hacking scenes and shows like Mr. Robot. Watching those, I decided on my dream career: Hacking.
But when I turned to Google for guidance, all I found were certification programs requiring money—money that I as a student, simply didn’t have. 😢
So, what did I do? I turned to the internet, the free school of the digital world. All you need is the right mindset and a targeted search approach.
Dissecting Topics for Learning
If you’re starting out, here’s a tip: instead of searching broad terms like “How to do Black Hat hacking,” break it down into smaller topics. For example:
i)“How to hack WiFi”
ii)“What is a phishing attack?”This approach makes it easier to learn specific techniques without getting overwhelmed. You can learn more about it in advance here.
How I Learned Black Hat Hacking
I started by setting up a safe environment for practice using Kali Linux installed on VirtualBox. It’s as simple as installing a game from the Play Store. Seriously, it’s that easy! 😊
Once my setup was ready, I explored and practiced techniques like:
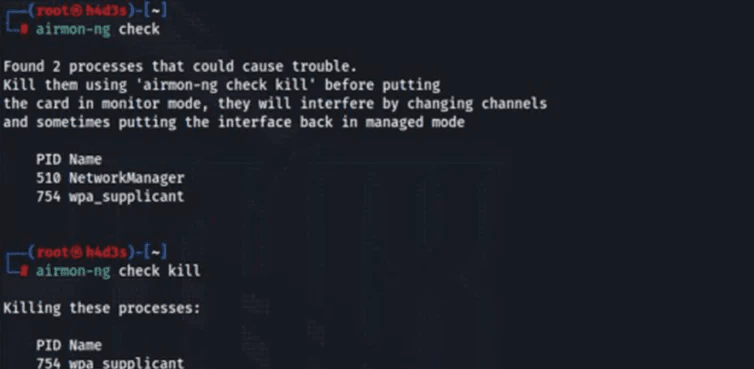
1) WiFi Hacking
I practiced on platforms like TryHackMe and, importantly, only on my own WiFi networks (because hacking someone else’s WiFi without permission is illegal).
While learning, I discovered key terms like WPS, WPA, WPA2, handshakes, and tools like Aircrack-ng.
Quick Tip:
WPA2 WiFi networks can’t be hacked directly. You need to:
i) Capture the handshake by deauthenticating connected users.
ii) Wait for them to reconnect, capturing the handshake again.
iii)Decrypt the handshake, which contains the password hash.If the password is strong, decrypting the hash becomes nearly impossible. In such cases, techniques like Evil Twin (creating a rogue access point) or phishing can trick users into revealing their password. You can learn about it in advance here.
2) Phishing
Phishing is one of the most common and effective techniques in Black Hat hacking. It involves creating fake but convincing replicas of legitimate websites to trick users into entering their credentials.
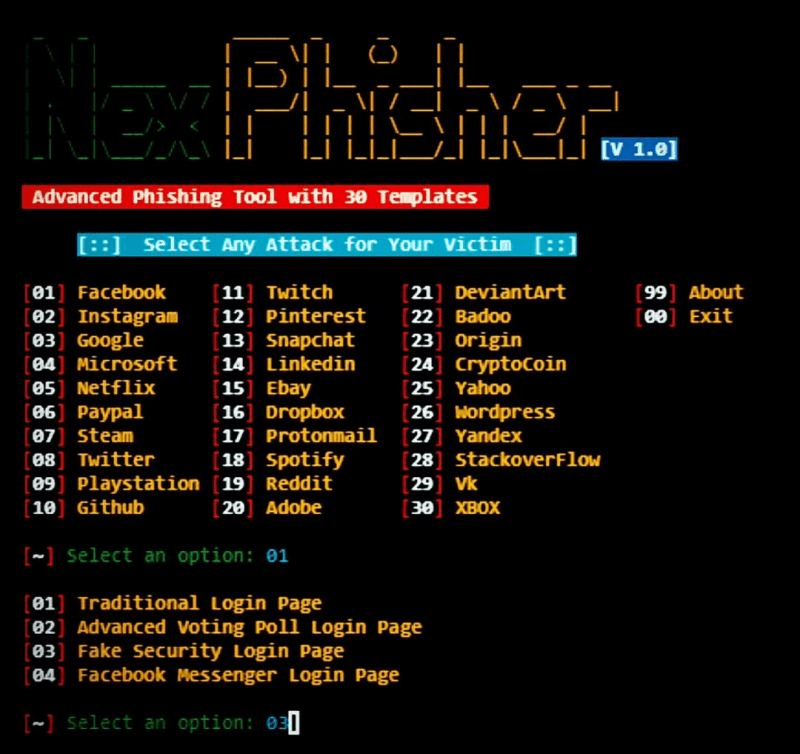
Here’s a Beginner’s Guide to Phishing:
i) Understand phishing basics: Learn to create replicas of login pages that look identical to real ones.
ii)Manipulate URLs: You won’t get a legit URL like https://example.com. Instead, use something like https://exampleisame.com and disguise it as much as possible.
iii)Tools to start with: Try tools like GoPhish or LocPhish to understand the process.This is intermediate-level stuff. To go deeper, you’ll need to build on these basics with additional research and practice. You can learn about it in advance here.
3) Ethical Hacker GPT
Here’s something new I’ve started recently that’s a game-changer for learning ethical hacking: using AI tools like ChatGPT.
How to Use GPT for Ethical Hacking:
i) Create an account on OpenAI.
ii) Explore GPTs by clicking the left-hand menu and searching for terms like “Ethical Hacker GPT”.
iii) Start asking questions like:
“I am testing an Apache server for vulnerabilities. How does CVE-2024-40898 work, and what are the prerequisites for testing it? Can you generate a Python script for testing this CVE?”
Always phrase your questions responsibly. If the AI thinks you’re trying to do something malicious, it won’t provide useful information. You can access the tool once you have created an account on OpenAi(Chat GPT) link for the tool.
A Word of Caution
Remember: With great power comes great responsibility. Use these skills in a safe lab environment and always respect others’ property and privacy. Never test anything without explicit permission, and always understand the potential impact of your actions.
Conclusion
That’s a glimpse into how I learned Black Hat hacking. While this is part of my past, I’ve since transitioned to ethical hacking and bug bounty hunting. In my next blog, I’ll share more tools, techniques, and tips to help you build your skills responsibly.
Stay tuned, keep learning, and always use your skills for good! 😊



888starz — yangi o’yin platformasi. bilan, uni. mukofotlar. yetakchi operatorlar.
uchun. oshiradi. o’zgarmas. o’zlariga.
mukofotlar. ko’proq. maxsus bonuslar. Bonus tizimi.
yangiliklar. Bu. ega bo’lishi. o’ynash.
888starz registraciya https://888starz-uzs.net/registration/
Diese konnen Selbsthilfegruppen oder Gesprache mit Therapeuten umfassen.
alkoholentzug https://entzugsklinik.pro/
With its extensive offerings and easy navigation, the 1win app stands out in the competitive betting market.
1win app ios https://1win-app.bet/
يمكن للزوار الانتقال بسهولة بين مختلف الأقسام.
888starz egypt https://888starz-egypts.com/
Откройте для себя новые возможности с перетяжкой мебели в Минске, позволяющей обновить ваш интерьер и продлить жизнь любимым предметам!
Если вы ищете перетяжку мебели в Минске, то
“аренда инструмента в слуцке – выгодные условия и широкий выбор инструментов для любых задач.”
Если вам нужен инструмент на короткий срок, аренда – идеальное решение, ведь не придется тратиться на дорогостоящее оборудование.
Такой подход особенно удобен для строителей и мастеров. Даже любители ремонта выбирают прокат инструмента, потому что это проще и дешевле.
#### **2. Какой инструмент можно взять в аренду?**
В Слуцке доступен широкий ассортимент оборудования для разных задач. В прокате представлены бензопилы, газонокосилки и другая садовая техника.
Кроме того, в аренду сдают и специализированную технику. Для укладки плитки можно взять плиткорезы, а для покраски – краскопульты.
#### **3. Преимущества аренды инструмента**
Главный плюс – экономия на обслуживании и хранении. Арендуя оборудование, вы избегаете затрат на его хранение и транспортировку.
Дополнительный бонус – помощь в выборе подходящего оборудования. Опытные менеджеры подскажут, какая модель лучше справится с работой.
#### **4. Как оформить аренду в Слуцке?**
Процедура аренды максимально проста и прозрачна. Достаточно оставить заявку на сайте или позвонить по телефону.
Условия проката выгодны для всех клиентов. Стоимость аренды зависит от срока и типа инструмента.
—
### **Спин-шаблон статьи**
#### **1. Почему аренда инструмента – это выгодно?**
Аренда инструмента в Слуцке позволяет сэкономить деньги и время . Вместо того чтобы покупать инструмент, который может понадобиться всего несколько раз, выгоднее взять его в аренду по доступной цене.
Такой подход особенно удобен для строителей и мастеров . Даже любители ремонта выбирают прокат инструмента, потому что это проще и дешевле.
#### **2. Какой инструмент можно взять в аренду?**
В Слуцке доступен множество инструментов для профессионального и бытового использования. В прокате представлены бензопилы, газонокосилки и другая садовая техника .
Кроме того, в аренду сдают и оборудование для узких задач. Для демонтажа предлагают отбойные молотки и мощные дрели.
#### **3. Преимущества аренды инструмента**
Главный плюс – доступ к исправному оборудованию. Все инструменты проходят регулярное обслуживание, поэтому клиенты получают только исправные устройства.
Дополнительный бонус – помощь в выборе подходящего оборудования . Консультанты помогут подобрать инструмент под конкретные задачи .
#### **4. Как оформить аренду в Слуцке?**
Процедура аренды доступна каждому клиенту. Вы можете приехать в офис, чтобы лично выбрать подходящий инструмент .
Условия проката адаптированы под разные потребности . На длительные периоды предоставляются скидки и специальные предложения .
Покупка уггов через интернет требует осторожности и внимания к выбору магазина.
угги кроссовки женские https://uggiaustralia-msk.ru/collection/ugg-krossovki/
A lot of gamers choose this version because it supports cross-platform play, enabling friends to join each other no matter what device they use.
mcpe shaders https://minecraftbedrock-apk.com/textures-minecraft-pe/shaders/
Players can enhance their gaming experience with numerous add-ons and skins available for Bedrock Edition.
mcpe 1.21 download https://minecraft-bedrock-edition.com/downloads/minecraft-pe-1-21/
La tecnologia de vuelo de compania de espectaculos de luces con drones ofrece una experiencia visual unica y emocionante.
El espectaculo de drones es una exhibicion que une la tecnologia y el arte para ofrecer un espectaculo impresionante . La posibilidad de ver a estos dispositivos voladores realizar acrobacias y formaciones complejas es algo que atrae a personas de todas las edades. La habilidad de los pilotos para controlar a los drones y crear un espectaculo emocionante es algo que sorprende a los espectadores. El espectaculo de drones es una forma de entretenimiento que sigue ganando popularidad en todo el mundo. El espectaculo de drones es una tendencia que sigue creciendo en popularidad debido a su originalidad y emocion .
El espectaculo de drones requiere una gran cantidad de planificacion y preparacion para asegurarse de que todo salga segun lo previsto. La organizacion de un espectaculo de drones es un proceso complejo que requiere una gran cantidad de tiempo y esfuerzo . Los pilotos deben tener una gran habilidad y experiencia para controlar a los drones y crear un espectaculo emocionante. Los pilotos de drones deben tener una gran cantidad de practica y entrenamiento para dominar el control de los dispositivos .
La tecnologia utilizada en los espectaculos de drones es muy avanzada y sofisticada. La tecnologia de los drones es muy precisa y permite a los pilotos controlar a los dispositivos con gran exactitud. Los drones estan equipados con sensores y camaras que les permiten navegar y realizar movimientos precisos. Los drones estan equipados con sistemas de navegacion que les permiten seguir rutas precisas y sincronizadas. La tecnologia de los drones es muy versatil y se puede utilizar en una variedad de aplicaciones, desde la fotografia y el video hasta la inspeccion y el monitoreo. La tecnologia de los drones es muy versatil y se puede utilizar en una variedad de industrias, desde la cinematografia hasta la agricultura .
La tecnologia de los drones es muy importante para crear un espectaculo emocionante y impresionante. La tecnologia de los drones es crucial para crear un espectaculo que sea unico y memorable . Los pilotos deben tener una gran cantidad de conocimiento y experiencia para utilizar la tecnologia de los drones de manera efectiva. Los pilotos de drones deben tener una gran cantidad de concentracion y atencion para utilizar la tecnologia de los drones de manera efectiva.
La seguridad es un aspecto muy importante en los espectaculos de drones. La seguridad es esencial para proteger a los pilotos, a los espectadores y a los drones. Los pilotos deben tener una gran cantidad de experiencia y habilidad para controlar a los drones y evitar accidentes. Los pilotos de drones deben tener una gran cantidad de practica y entrenamiento para dominar el control de los dispositivos y evitar colisiones . Los organizadores del espectaculo deben tomar medidas para garantizar que el evento sea seguro y que se cumplan todas las normas y regulaciones. Los organizadores del espectaculo deben tomar medidas para proteger a los pilotos, a los espectadores y a los drones.
La seguridad es un aspecto que debe ser tomado muy en serio en los espectaculos de drones. La seguridad es un aspecto que debe ser priorizado para proteger a los pilotos, a los espectadores y a los drones. Los pilotos y los organizadores deben trabajar juntos para garantizar que el espectaculo sea seguro y que se cumplan todas las normas y regulaciones. Los pilotos y los organizadores deben trabajar juntos para proteger a los pilotos, a los espectadores y a los drones.
El espectaculo de drones es un evento emocionante y innovador que combina la tecnologia y la creatividad para ofrecer una experiencia unica y fascinante. El espectaculo de drones es una experiencia que fusiona la robotica y la imaginacion para crear un evento inolvidable. La tecnologia utilizada en los espectaculos de drones es muy avanzada y sofisticada, y permite a los pilotos controlar a los dispositivos con gran exactitud. La tecnologia de los drones es muy innovadora y permite crear espectaculos unicos y emocionantes . La seguridad es un aspecto muy importante en los espectaculos de drones, y los pilotos y los organizadores deben trabajar juntos para garantizar que el espectaculo sea seguro y que se cumplan todas las normas y regulaciones. La seguridad es fundamental para garantizar que el espectaculo sea seguro y emocionante para la audiencia .
El espectaculo de drones es un evento que sigue ganando popularidad en todo el mundo, y es una forma de entretenimiento que ofrece una experiencia unica y emocionante. El espectaculo de drones es un evento que sigue atrayendo a mas personas debido a su capacidad para sorprender y emocionar. Los espectaculos de drones pueden ser utilizados en una variedad de aplicaciones, desde la fotografia y el video hasta la inspeccion y el monitoreo. Los espectaculos de drones pueden ser utilizados en una variedad de industrias, desde la cinematografia hasta la agricultura . En resumen, el espectaculo de drones es un evento emocionante y innovador que ofrece una experiencia unica y fascinante, y es una forma de entretenimiento que sigue ganando popularidad en todo el mundo. El espectaculo de drones es una exhibicion que une la tecnologia y el arte para ofrecer un espectaculo impresionante .
Create your own custom notary stamp.
The importance of notary stamps in legal paperwork cannot be overstated. They ensure the verification of vital records. Lately, the interest in notary stamp generators has surged.
A notary stamp generator allows users to create personalized stamps. These generators typically offer a variety of templates and options. Such adaptability guarantees that each notary can produce a stamp that represents their professional persona.
Nonetheless, exercising caution while using these generators is essential. It’s imperative that the stamp adheres to the necessary legal criteria. Not adhering to these standards may result in significant repercussions.
Ultimately, the notary stamp generator emerges as an essential asset for those in the legal field. By leveraging these tools, notaries can improve their workflow and effectiveness. Opting for an efficient notary stamp generator can greatly enhance your professional experience.
Для поддержания чистоты и порядка в офисе или доме часто обращаются в клининг мск, которая предлагает??ные услуги по уборке и содержанию помещений.
Клининг – это процесс, который включает в себя уборку и очистку помещений.
Важно тщательно оценить потребности и выбрать наиболее подходящие методы и средства для каждой конкретной задачи.
Важно выбирать инструменты и приспособления, которые подходят для каждой конкретной задачи и обеспечивают эффективную уборку.
В заключение, клининг является важнейшим аспектом поддержания чистоты и порядка в различных помещениях.
When designing wedding invitations, many couples use wedding rubber stamp, to add personality and flair to your special invitations.
Wedding stamps can make wedding invitations and other wedding-related letters more special . They come in a variety of designs and styles, from traditional to modern Wedding stamps can be found in many different designs and styles, from traditional to modern . Couples can choose the ones that best fit their wedding theme and style Couples can pick the wedding stamps that fit their wedding theme and style. Wedding stamps can also be customized with the couple’s names, wedding date, and other personal details Wedding stamps can be personalized with the couple’s names, wedding date, and other personal information .
Wedding stamps are not only beautiful but also meaningful Wedding stamps have a special significance in addition to their beauty . They symbolize the union of two people and the beginning of their new life together Wedding stamps represent the union of two individuals and the start of their new life together . Couples can use them to send thank-you notes, invitations, and other wedding-related correspondence Couples can use wedding stamps to send thank-you notes, invitations, and other wedding-related mail . Wedding stamps can also be collected as a keepsake Wedding stamps can be kept as a memento .
The history of wedding stamps dates back to the mid-20th century The origins of wedding stamps can be traced back to the mid-20th century. The first wedding stamps were introduced by the United States Postal Service The United States Postal Service introduced the first wedding stamps . They were designed to commemorate special occasions such as weddings and anniversaries These stamps were designed to commemorate special occasions like weddings and anniversaries . Since then, wedding stamps have become a popular way to celebrate weddings Over time, wedding stamps have become a common way to commemorate weddings .
The designs of wedding stamps have evolved over the years The designs of wedding stamps have developed over time. From traditional to modern, there are many different designs to choose from There are many different designs to choose from, ranging from traditional to modern . Some wedding stamps feature romantic landscapes, while others feature beautiful floral arrangements Some wedding stamps feature romantic landscapes, while others feature beautiful flowers . Couples can choose the ones that best fit their wedding theme and style Couples can choose the wedding stamps that best fit their wedding theme and style .
There are many different types of wedding stamps available There are various types of wedding stamps available. Some are designed specifically for wedding invitations, while others are designed for thank-you notes and other correspondence Wedding stamps can be used for wedding invitations, thank-you notes, and other wedding-related letters . Couples can also choose from a variety of shapes and sizes There are many different shapes and sizes of wedding stamps available. Some wedding stamps are heart-shaped, while others are square or circular Wedding stamps can be heart-shaped, square, or circular .
Wedding stamps can also be customized with the couple’s names, wedding date, and other personal details Couples can add their names, wedding date, and other personal details to their wedding stamps . This makes them a unique and meaningful way to commemorate the wedding Customizing wedding stamps with personal details makes them a unique and meaningful way to celebrate the wedding . Couples can use them to send invitations, thank-you notes, and other wedding-related correspondence Couples can use wedding stamps to send invitations, thank-you notes, and other wedding-related mail .
In conclusion, wedding stamps are a beautiful and meaningful way to add a personal touch to wedding invitations and other wedding-related correspondence In conclusion, wedding stamps are a lovely way to customize wedding invitations and other wedding-related mail . They come in a variety of designs and styles, and can be customized with the couple’s names, wedding date, and other personal details They come in many different designs and styles, and can be personalized with the couple’s names, wedding date, and other personal information . Couples can use them to send invitations, thank-you notes, and other wedding-related correspondence Couples can use wedding stamps to send out invitations, thank-you notes, and other wedding-related documents. Wedding stamps are a unique and meaningful way to commemorate the wedding Wedding stamps are a special and meaningful way to commemorate the wedding .
Overall, wedding stamps are a wonderful way to make the wedding planning process more special and meaningful In general, wedding stamps are a lovely way to make the wedding planning process more personal and memorable. They can be used in many different ways, from sending invitations to decorating the wedding album Wedding stamps can be used for many different purposes, including sending invitations and decorating the wedding album . Couples can choose the wedding stamps that best fit their wedding theme and style Couples can pick the wedding stamps that fit their wedding theme and style. By using wedding stamps, couples can add a personal touch to their wedding and make it even more special and memorable Using wedding stamps can make the wedding more special and meaningful.
Для того, чтобы найти подходящего специалиста для улучшения позиций вашего сайта в поисковых системах, стоит посетить сайт лучший seo оптимизатор сочи, где представлены профессионалы в области SEO.
имеют большое количество положительных отзывов и могут помочь вашему бизнесу добиться успеха в поисковых системах. Рейтинг сео специалистов Сочи регулярно изменяется в зависимости от результатов их работы. Стоит отметить, что это необходимо для развития любой компании.
В Сочи есть много seo специалистов , которые могут помочь вам с оптимизацией и продвижением вашего сайта. Рейтинг сео специалистов Сочи учитывает множество критериев , включая опыт, портфолио и отзывы клиентов. Поэтому нужно внимательно изучить предложения онлайн-компаний.
Чтобы найти лучшего сео специалиста в Сочи, важно оценить стоимость услуг и качество работы. Также полезно изучить отраслевые форумы. Все это поможет вам сделать правильный выбор .
Очень нужно определить целевую аудиторию, чтобы сео специалист мог предложить наиболее эффективные решения. Рейтинг сео специалистов Сочи REGULARно обновляется и может включать новых участников, поэтому важно быть в курсе последних изменений .
SEO-специалисты в Сочи обладают знаниями, которые помогают увеличить продажи. Они могут повысить узнаваемость бренда и репутацию. Поэтому важно правильно выбрать сео специалиста .
Рейтинг сео специалистов Сочи облегчает поиск сео агентств . Он включает множество факторов, которые важны для бизнеса, поэтому необходимо проанализировать предложения сео агентств.
Работа с лучшими сео специалистами в Сочи предоставляет множество преимуществ . Они могут повысить лояльность клиентов и репутацию бренда. Поэтому стоит обратиться к лучшим сео специалистам .
Рейтинг сео специалистов Сочи регулярно обновляется , поэтому важно быть в курсе последних изменений . Лучшие сео специалисты в Сочи обладают знаниями и опытом , поэтому важно найти лучшего сео специалиста .
To add sophistication and uniqueness to your special day, consider using stamp for wedding on your invitations and wedding cards.
The tradition of using wedding stamps dates back to a time when invitations were truly special, and the stamp was a symbol of the occasion. Many couples choose to use custom wedding stamps to add a personal touch to their wedding invitations Couples often opt for personalized wedding stamps to give their invitations a bespoke feel . Some wedding stamps feature the couple’s names, while others feature a special message or the wedding date Many wedding stamps incorporate the couple’s names, a special message, or the wedding date in a stunning layout.
The use of wedding stamps can also be a great way to set the tone for the wedding Using a wedding stamp can help create a cohesive look and feel for the wedding. For example, a formal wedding might feature a traditional wedding stamp with a elegant design A formal wedding might feature a classic wedding stamp with a sophisticated design . On the other hand, a casual wedding might feature a more playful wedding stamp with a fun design A wedding stamp with a lively and carefree design is great for a casual wedding. The options are endless, and couples can choose the wedding stamp that best fits their style and theme The options for wedding stamps are vast, and couples can pick the one that best suits their wedding .
There are many different types of wedding stamps available, ranging from traditional to modern There are numerous types of wedding stamps to choose from, including traditional and modern designs . Some wedding stamps feature a classic design with a elegant font and a simple border Others feature a traditional design with a sophisticated font and a decorative border . These types of wedding stamps are perfect for formal weddings or for couples who want a traditional look These wedding stamps are ideal for formal weddings or for couples who prefer a classic look . Other wedding stamps feature a more modern design with bright colors and bold fonts Many wedding stamps have a modern design with bold colors and stylish fonts. These types of wedding stamps are perfect for casual weddings or for couples who want a unique and playful look These wedding stamps are great for casual weddings or for couples who want a fun and quirky design .
Some wedding stamps also feature a special theme or design, such as a beach or a mountain Many wedding stamps have a special theme or design, such as a garden or a vineyard. These types of wedding stamps are perfect for couples who want to incorporate their wedding location into their invitations Themed wedding stamps are perfect for couples who want to tie in their wedding location with their invitations . For example, a couple getting married on the beach might choose a wedding stamp with a beach theme A beach-themed wedding stamp is perfect for a couple getting married by the ocean . On the other hand, a couple getting married in the mountains might choose a wedding stamp with a mountain theme A mountain-themed wedding stamp is perfect for a couple getting married in the mountains .
Using wedding stamps can have many benefits for couples planning their wedding Using wedding stamps can have numerous advantages for couples planning their special day . One of the main benefits is that wedding stamps can add a personal touch to wedding invitations Using a wedding stamp can give wedding invitations a unique and personalized feel . This can help couples stand out and make their wedding invitations more memorable Wedding stamps can help couples create a lasting impression with their wedding invitations. Another benefit is that wedding stamps can save couples time and money Wedding stamps can save couples time and money, as they are often less expensive than traditional mailing methods . For example, couples can use a single wedding stamp on all of their invitations, rather than having to affix a separate stamp to each one Using a wedding stamp can simplify the process of mailing wedding invitations .
Using wedding stamps can also help couples create a cohesive look and feel for their wedding Wedding stamps can help couples tie together all of the elements of their wedding, from the invitations to the decorations . This can help create a sense of continuity and flow throughout the wedding Wedding stamps can help couples create a seamless and integrated look for their wedding. For example, a couple might choose a wedding stamp with a floral design and use it on their invitations, programs, and thank-you cards Using a wedding stamp with a floral design can help couples create a cohesive and consistent look for their wedding. This can help create a beautiful and cohesive look that ties together all of the elements of the wedding This can help create a beautiful and cohesive look that ties together all of the elements of the wedding, from the invitations to the decorations .
In conclusion, wedding stamps are a great way to add a personal touch to wedding invitations and create a cohesive look and feel for the wedding Wedding stamps are a great way to make wedding invitations more special and create a consistent look for the wedding . With so many different types of wedding stamps available, couples can choose the one that best fits their style and theme With so many different types of wedding stamps available, couples can select the one that best suits their style and theme . Whether you’re planning a formal or casual wedding, there’s a wedding stamp that’s perfect for you Whether you’re planning a small or large wedding, there’s a wedding stamp that’s ideal for your wedding. So why not consider using a wedding stamp to make your wedding invitations truly special Why not use a wedding stamp to add a personal touch to your wedding invitations and create a cohesive look for your wedding ? So why not consider the benefits of using wedding stamps and how they can make your wedding invitations more special .
умные занавески Прокарниз – управляемые шторы, которые позволят вам легко контролировать свет и атмосферу в вашем доме.
Такие шторы могут стать изюминкой вашего интерьера.
электро карниз москва Прокарниз позволяют управлять шторами с помощью одного нажатия кнопки, обеспечивая удобство и комфорт в вашем доме.
Пользователи могут открывать и закрывать шторы, оставаясь в комфортном положении.
Удобные и стильные автоматические карнизы в москве Прокарниз делают управление шторами простым и комфортным.
Кроме того, они могут быть интегрированы в систему “умный дом”, что обеспечивает дополнительный комфорт.
Автоматические жалюзи позволяют легко настраивать уровень освещения в комнате. С автоматическими жалюзи вы сможете легко менять уровень освещения в зависимости от времени суток. Это особенно важно для людей, работающих на удаленке. Это обеспечивает комфортные условия как для работы, так и для отдыха.
жалюзи горизонтальные с электроприводом Прокарниз обеспечивают удобство и стиль в вашем доме, позволяя управлять светом одним нажатием кнопки.
Все больше людей выбирают автоматические жалюзи на окна с электроприводом. Удобство и функциональность автоматических жалюзи делают их идеальным выбором для современных интерьеров. Электропривод позволяет управлять жалюзи дистанционно с помощью пульта или смартфона. Дистанционное управление делает эксплуатацию жалюзи очень удобной.
Еще одним важным аспектом является экономия энергии. Эффективная эксплуатация жалюзи помогает сократить расходы на энергию для обогрева и охлаждения. Они помогают поддерживать комфортную температуру в квартиру. Таким образом, они не только удобны, но и экономически оправданы.
Следует подчеркнуть, что монтаж жалюзи можно осуществить как профессионалами, так и своими силами. Это зависит от ваших навыков и желания. Если вы выберете самостоятельный монтаж, важно внимательно следовать инструкциям. Это позволит избежать возможных ошибок и обеспечит надежную работу устройства.
Откройте для себя идеальное решение для защиты от солнца с купить автоматические рулонные жалюзи, которые удобно управляются одним движением.
в различных цветах. Вы можете выбрать модель, которая идеально впишется в ваш интерьер
Одним из главных преимуществ таких штор является возможность управления с помощью пульта | Управление рулонными шторами с электроприводом осуществляется легко с помощью пульта | Электроприводные рулонные шторы предлагают комфортное управление через пульт. Это позволяет вам регулировать свет и атмосферу в комнате одним нажатием кнопки | Вы можете поменять уровень освещения в помещении всего лишь одним нажатием кнопки | С помощью простого нажатия кнопки вы сможете изменить интенсивность света в комнате.
Вы можете купить электрические рулонные шторы Прокарниз и наслаждаться комфортом и удобством в вашем доме.
Электроприводные рулонные шторы изготовлены из высококачественных тканей. Они обеспечивают отличную защиту от солнечных лучей и создают уют в вашем пространстве
Обеспечьте комфорт и стиль в вашем доме с автоматические рулонные жалюзи в москве Прокарниз, которые идеально впишутся в современный интерьер.
Рулонные шторы с автоматическим управлением становятся все более популярными в современных интерьерах. Применение автоматических штор позволяет не только удобно регулировать свет, но и добавить стиль в ваш дом. Подобные изделия идеально вписываются в концепцию “умного дома”.
Системы автоматизации позволяют контролировать рулонные шторы с помощью смартфона. Владельцы могут задавать график работы штор в зависимости от времени суток. Такой подход очень удобен делает жизнь более комфортной.
Кроме того, автоматические рулонные шторы могут быть оснащены датчиками света и температуры. Данное оборудование автоматически регулируют положение штор для достижения оптимального уровня освещенности. В результате вы можете экономить на электроэнергии благодаря естественному освещению.
Монтаж умных штор достаточно прост и не требует специальных навыков. Владельцы могут установить их самостоятельно, следуя инструкциям. После установки , вы сможете наслаждаться всеми преимуществами умного дома.
Автоматизированные карнизы становятся все более популярными в современных интерьере. Они предлагают комфорт и эстетику для любого помещения. Благодаря электроприводу , можно легко управлять шторами или занавесками при помощи мобильного приложения.
Откройте для себя элегантность и удобство карнизы с электроприводом и дистанционным управлением Prokarniz, которые сделают управление шторами простым и современным.
Одним из главных преимуществ карнизов с электроприводом является их . домов . Также стоит отметить, что эти карнизы позволяют создавать в доме или офисе.
Установка таких систем возможна в любом интерьере . Установка не требует специальных знаний , и с этим может справиться даже новичок . Кроме того, такие карнизы современные системы автоматизации.
Хотя карнизы с электроприводом имеют много плюсов, существуют и несколько ограничений. цена на такие конструкции может оказаться высокой . Однако, , ведь делают повседневные дела намного легче.
Откройте мир удобства с нашими автоматические рулонные жалюзи с электроприводом Prokarniz, которые обеспечивают идеальное сочетание стиля и функциональности.
Они помогают регулировать световой поток и обеспечивают необходимую защиту от посторонних взглядов.
Удобство и стиль в вашем доме с автоматические рулонные шторы на окна прокарниз, которые легко управляются одним нажатием кнопки.
Автоматические рулонные шторы набирают популярность среди современных интерьеров. Эти изделия предлагают не только стильный внешний вид, но и удобство в использовании .
Одним из главных преимуществ автоматических рулонных штор является возможность дистанционного управления . Управлять освещением в комнате можно, не покидая уютного места .
Важно отметить, что такие шторы могут иметь встроенные датчики . Такие шторы способны адаптироваться к условиям окружающей среды автоматически.
Наконец, стоит упомянуть о том, что автоматические рулонные шторы доступны в различных дизайнах и цветах . Вы можете выбрать тот вариант, который наилучшим образом впишется в ваш интерьер .
Для тех, кто ищет качественную диссертация на заказ цена, команда профессиональных авторов предлагает уникальные и качественные решения, позволяющие защитить свою научную работу на высшем уровне.
Диссертация на заказ – это способ получить высококачественную работу без лишних усилий. Эта услуга стала особенно популярной среди студентов, которые не имеют возможности самостоятельно написать качественную работу. Основная причина этого – отсутствие времени или необходимых навыков для написания диссертации. Кроме того, студенты часто не могут определиться с темой диссертации, что может привести к задержкам в выполнении работы. Это позволяет студентам получить работу, которая полностью соответствует их интересам и специальности. Такой подход позволяет студентам экономить время и силы на другие важные задачи.
Заказ диссертации на заказ дает студентам возможность получить качественную работу, выполненную опытными специалистами. Кроме того, студенты могут рассчитывать на то, что их работа будет соответствовать высоким академическим стандартам. Это особенно важно для студентов, которые Заказ диссертации на заказ также дает студентам возможность работать с опытными авторами, которые имеют глубокое понимание предмета. Это сотрудничество дает студентам возможность учиться у опытных специалистов и улучшать свои собственные навыки.
Процесс заказа диссертации на заказ обычно начинается с выбора темы и определения требования к работе. Затем автор приступает к написанию диссертации, используя только надежные источники и обеспечивая уникальность работы. После завершения работы студент получает возможность просмотреть и одобрить готовую диссертацию перед ее сдачей. Это дает студенту возможность быть уверенным в том, что его диссертация будет выполнена на высшем уровне.
Заказ диссертации на заказ дает студентам возможность сосредоточиться на других важных аспектах их жизни и карьеры. Это особенно важно для студентов, которые стремятся к академическому успеху и дальнейшему профессиональному росту. Поэтому, В заключение, можно сказать, что диссертация на заказ – это ценная услуга, которая дает студентам возможность получить качественную работу и успешно завершить образование. Это может быть особенно важно для студентов, которые стремятся к академическому успеху и высокому профессиональному статусу.
Обновите интерьер вашего дома с помощью Замена обивки диванов и кресел, которая придаст ей свежий и современный вид.
Важно учесть степень износа мебели и ее функциональное назначение.
Если вы ищете лучшие фотографы москва, вы можете найти высококачественную и творческую фотографию, которая отражает красоту города и его жителей.
представляет собой уникальную смесь современной и исторической архитектуры в каждом уголке города. имеют возможность снять широкий спектр тем, от древних храмов до современных небоскрёбов . Лучшие фотографы Москвы знают, как передать суть города через свои снимки .
Москва предлагает широкий спектр объектов для съемки, от знаменитых достопримечательностей до скрытых уголков . показать разнообразие культур и традиций в столице. знают, как играют с светом и тенью, делая каждый снимок уникальным .
их фотографии не только красочны, но и передают историю и эмоции . их снимки рассказывают о жизни, любви, радости и печали . Фотографии лучших мастеров не только отражают реальность, но и открывают новые перспективы .
Лучшие фотографы Москвы часто сотрудничают с модными журналами, работают над рекламными кампаниями и участвуют в выставках . фотографы делятся своим опытом и знаниями на мастер-классах и семинарах . они показывают city в всех его состояниях.
применяют черно-белую фотографию, чтобы подчеркнуть контрасты и текстуры. Они могут снять город с высоты птичьего полета, чтобы показать его масштаб и планировку . показать город в новой и интересной перспективе .
Некоторые фотографы фокусируются на портретной фотографии, запечатлевая образы горожан . Их работы демонстрируют разнообразие городского опыта и культурного богатства . вместе они создают удивительную мозаику, которая рассказывает историю о столице.
город продолжает меняться и развиваться, предлагая новые темы и объекты для съемки . использовать инновационные техники и стили, чтобы рассказать новые истории . Город будет оставаться источником вдохновения для фотографов, и их работы будут продолжать рассказывать уникальную историю о Москве .
фотографы смогут учиться друг у друга и расти профессионально. фотографы будут продолжать запечатлевать ее красоту и дух . вместе мы создадим удивительную историю о Москве.
“Ремонт механизма трансформации”
Обновление обивки даёт мебели вторую жизнь, сохраняя её функциональность.
Такой подход не только экономит бюджет, но и позволяет индивидуализировать интерьер. Новая обивка позволяет полностью изменить дизайн старой мебели.
—
### **2. Какие материалы лучше использовать?**
Для перетяжки применяют различные ткани, отличающиеся износостойкостью и внешним видом. Кожа и экокожа придают мебели благородный вид и просты в уходе.
Также важно учитывать наполнитель, который влияет на комфорт. Поролон средней плотности обеспечит мягкость и долговечность.
—
### **3. Этапы профессиональной перетяжки**
Процесс начинается с демонтажа старой обивки и оценки состояния каркаса. Мастер удаляет изношенную ткань и проверяет прочность конструкции.
Далее выбирают материал и производят раскрой. Раскрой выполняется с запасом для удобства последующего натяжения.
—
### **4. Преимущества профессионального подхода**
Обращение к специалистам гарантирует качество и долгий срок службы мебели. Профессионалы используют надёжные крепления и прочные швы.
Кроме того, экономится время и исключаются ошибки. Самостоятельная перетяжка может привести к перекосам и быстрому износу.
—
### **Спин-шаблон:**
#### **1. Почему стоит выбрать перетяжку мебели?**
– Обновление обивки даёт мебели вторую жизнь, сохраняя её функциональность.
– Это отличный способ адаптировать мебель под меняющиеся предпочтения в оформлении дома.
#### **2. Какие материалы лучше использовать?**
– Кожа и экокожа придают мебели благородный вид и просты в уходе.
– Поролон средней плотности обеспечит мягкость и долговечность.
#### **3. Этапы профессиональной перетяжки**
– Старая ткань аккуратно снимается, а каркас проверяется на наличие повреждений.
– Обивочный материал тщательно размечается и вырезается с учётом всех деталей.
#### **4. Преимущества профессионального подхода**
– Опытные ремонтники учитывают все нюансы, чтобы результат радовал годами.
– Только специалист сможет точно воспроизвести первоначальную форму мебели.
Взаимодействие с другими игроками приносит радость и множество новинок в игровой процесс.
1.22.0 https://minecraft-bedrocks.com/minecraft-pe-1-22-0/
Подарите своей любимой мебели новую жизнь, заказав профессиональную Перетяжка тахты в Минске!
Это более экономичный вариант и позволяет вам сохранить ваши любимые предметы мебели.
**Выбор ткани: на что обратить внимание?**
К популярным вариантам относятся велюр, рогожка, жаккард и флок
**Этапы перетяжки мебели: от замера до готового результата**
После этого снимается старая обивка и оценивается состояние внутреннего материала.
**Уход за перетянутой мебелью: продлеваем срок службы**
Не допускайте попадания прямых солнечных лучей на мебель, чтобы избежать выцветания ткани
Желая узнать о себе больше, вы можете воспользоваться калькулятором квадрат пифагора как рассчитать и открыть новые грани своей личности.
Квадрат Пифагора, рассчитанный по дате рождения, дает возможность заглянуть в тайны судьбы и раскрыть потенциал человека. Это древний метод, который использовался в различных культурах для понимания человеческой природы и предсказания событий. Квадрат Пифагора, сформированный по дате рождения, показывает индивидуальный энергетический код каждого человека. Таким образом, квадрат Пифагора может стать ценным инструментом для самопознания и личностного роста.
Квадрат Пифагора основан на простом, но глубоком принципе, согласно которому каждое число имеет свою собственную энергию и влияние на человеческую жизнь. принцип позволяет нам использовать квадрат Пифагора как инструмент для анализа личности и прогнозирования будущих событий. Для расчета квадрата Пифагора необходимо произвести ряд математических операций, которые включают в себя суммирование чисел даты рождения и определение их позиций в квадрате. Это позволяет получить подробную картину личности и потенциала человека.
Квадрат Пифагора по дате рождения может быть использован для анализа личности, определения сильных и слабых сторон, а также для предсказания будущих событий. Это делает квадрат Пифагора ценным инструментом для личностного роста и самосовершенствования. Кроме того, квадрат Пифагора может быть использован для понимания отношений между людьми и определения совместимости в любви и браке. Это может помочь людям найти гармонию и понимание в их отношениях.
Необходимо изучить принципы и символы квадрата Пифагора, чтобы правильно его применять. Это позволит получить точные и полезные результаты от анализа. Квадрат Пифагора по дате рождения может стать ценным инструментом для самоанализа и личностного роста, если его использовать правильно и с пониманием его принципов.
Квадрат Пифагора, рассчитанный по дате рождения, дает возможность понять потенциал человека в различных областях жизни. Это может помочь людям принимать обоснованные решения и достигать своих целей. Кроме того, квадрат Пифагора может быть использован для понимания и разрешения конфликтов в отношениях. Это может привести к более гармоничным и удовлетворительным отношениям.
Необходимо изучить основы математики и символы квадрата Пифагора, чтобы его правильно применять. Это позволит получить точные результаты от анализа и принимать обоснованные решения. Квадрат Пифагора, основанный на дате рождения, дает возможность глубокого самопознания и личностного роста, если его использовать с знанием его принципов.
Квадрат Пифагора по дате рождения является мощным инструментом для анализа личности, предсказания будущих событий и личностного роста. Это делает его ценным инструментом для тех, кто стремится к самопознанию и личностному росту. Квадрат Пифагора по дате рождения помогает понять отношения между людьми и определить их совместимость. Это может привести к более гармоничным и удовлетворительным отношениям.
Квадрат Пифагора, рассчитанный по дате рождения, дает возможность заглянуть в тайны судьбы и раскрыть потенциал человека. Это может привести к более полноценной и удовлетворительной жизни. Квадрат Пифагора, рассчитанный по дате рождения, может быть мощным инструментом для самопознания и личностного роста. Это может стать вашим первым шагом на пути к самосовершенствованию и гармонии.
Желая узнать о себе больше, вы можете воспользоваться калькулятором таблица пифагор по дате рождения и открыть новые грани своей личности.
Квадрат Пифагора, рассчитанный по дате рождения, дает возможность заглянуть в тайны судьбы и раскрыть потенциал человека. Это древний метод, который использовался в различных культурах для понимания человеческой природы и предсказания событий. Каждый человек, родившийся под определенным числом, имеет уникальный энергетический код, который отражается в квадрате Пифагора. Таким образом, квадрат Пифагора может стать ценным инструментом для самопознания и личностного роста.
Квадрат Пифагора основан на простом, но глубоком принципе, согласно которому каждое число имеет свою собственную энергию и влияние на человеческую жизнь. принцип позволяет нам использовать квадрат Пифагора как инструмент для анализа личности и прогнозирования будущих событий. Для расчета квадрата Пифагора необходимо произвести ряд математических операций, которые включают в себя суммирование чисел даты рождения и определение их позиций в квадрате. Это позволяет получить подробную картину личности и потенциала человека.
Квадрат Пифагора, рассчитанный по дате рождения, дает возможность понять характер человека, его потенциал и вероятность успеха в различных областях жизни. Это делает квадрат Пифагора ценным инструментом для личностного роста и самосовершенствования. Квадрат Пифагора по дате рождения помогает понять отношения между людьми и определить их совместимость. Это может помочь людям найти гармонию и понимание в их отношениях.
Необходимо изучить принципы и символы квадрата Пифагора, чтобы правильно его применять. Это позволит получить точные и полезные результаты от анализа. Квадрат Пифагора, основанный на дате рождения, дает возможность глубокого самопознания и личностного роста, если его использовать с знанием его принципов.
Квадрат Пифагора по дате рождения может быть применен в различных областях жизни, таких как карьера, любовь и личностный рост. Это может помочь людям принимать обоснованные решения и достигать своих целей. Квадрат Пифагора по дате рождения помогает понять причину конфликтов в отношениях и найти способ их разрешения. Это может привести к более гармоничным и удовлетворительным отношениям.
Для практического применения квадрата Пифагора необходимо иметь хорошие математические навыки и понимание его символики. Это позволит получить точные результаты от анализа и принимать обоснованные решения. Квадрат Пифагора, рассчитанный по дате рождения, может быть мощным инструментом для самопознания и личностного роста, если его использовать с пониманием его основ.
Квадрат Пифагора, основанный на дате рождения, позволяет оценить сильные и слабые стороны человека, а также спрогнозировать его будущее. Это делает его ценным инструментом для тех, кто стремится к самопознанию и личностному росту. Кроме того, квадрат Пифагора может быть использован для понимания отношений между людьми и определения совместимости в любви и браке. Это может привести к более гармоничным и удовлетворительным отношениям.
В заключении, квадрат Пифагора по дате рождения является уникальным и ценным инструментом, который может помочь людям глубже понять себя и окружающих. Это может привести к более полноценной и удовлетворительной жизни. Квадрат Пифагора, основанный на дате рождения, дает возможность глубокого самопознания и личностного роста. Это может стать вашим первым шагом на пути к самосовершенствованию и гармонии.
Компания сервисы клининга предоставляет высококачественные услуги по уборке и клинингу в Москве и ее окрестностях.
Услуги клининга в Москве становятся все более востребованными. Это связано с тем, что многие жители города предпочитают тратить свое время на более важные дела. Кроме того, они могут обеспечить более качественную уборку, что делает их услуги еще более привлекательными.
Услуги клининга в Москве включают в себя уборку офисных пространств . Профессиональные клинеры могут выполнить глубокую уборку . Они используют инновационные технологии для обеспечения высокой качества уборки.
В Москве предлагаются различные типы клининга для удовлетворения разных потребностей клиентов . Среди них уборка после ремонта являются наиболее популярными. Каждый тип уборки осуществляется с учетом индивидуальных потребностей клиента .
Кроме того, уборка промышленных помещений также очень востребованы. Для этих типов уборки используются профессиональные средства и методы . Все это позволяет выполнить уборку в кратчайшие сроки .
Использование услуг клининга в Москве имеет ряд достоинств . Одним из них является экономия времени . Кроме того, профессиональные клинеры могут выполнять уборку более качественно .
Услуги клининга в Москве также повышают эффективность работы. Это связано с тем, что уборка помогает предотвратить распространение микробов и заболеваний .
В заключение, услуги клининга в Москве представляют собой перспективную и развивающуюся сферу . Это связано с тем, что профессиональная уборка является важной частью современного образа жизни .
Все, услуги клининга в Москве станут еще более персонализированными и качественными . Это позволит расширить спектр услуг и предложений .
Компания клининговые компании москвы предоставляет высококачественные услуги по уборке и клинингу в Москве и ее окрестностях.
Услуги клининга в Москве пользуются большим спросом . Это связано с тем, что многие жители города не имеют времени на уборку . Кроме того, профессиональные клинеры имеют специальное оборудование , что делает их услуги еще более привлекательными.
Услуги клининга в Москве включают в себя уборку офисных пространств . Профессиональные клинеры могут обеспечить регулярную уборку. Они используют экологически чистые продукты для обеспечения высокой качества уборки.
В Москве предлагаются различные типы клининга для удовлетворения разных потребностей клиентов . Среди них уборка после ремонта являются наиболее популярными. Каждый тип уборки осуществляется с учетом индивидуальных потребностей клиента .
Кроме того, уборка складов также очень востребованы. Для этих типов уборки привлекаются высококвалифицированные специалисты. Все это позволяет обеспечить высокое качество уборки .
Использование услуг клининга в Москве имеет несколько важных плюсов. Одним из них является экономия времени . Кроме того, они имеют большой опыт и навыки.
Услуги клининга в Москве также помогают поддерживать здоровье и безопасность . Это связано с тем, что уборка помогает предотвратить распространение микробов и заболеваний .
В заключение, услуги клининга в Москве становятся все более популярными и востребованными . Это связано с тем, что люди все больше ценят свое время и здоровье .
Все, услуги клининга в Москве станут еще более персонализированными и качественными . Это позволит расширить спектр услуг и предложений .
Услуги по накрутки пф помогают повысить позиции сайта в поисковых системах.
Накрутки ПФ играют ключевую роль в улучшении видимости и авторитета сайта в поисковых системах. Это связано с тем, что Накрутки ПФ должны быть частью комплексной стратегии интернет-маркетинга и продвижения.
На сайте seo оптимизация курсы предлагаются высококачественные образовательные программы, позволяющие освоить необходимые навыки и стать профессионалом в области SEO.
отличным способом повысить навыки в поисковой оптимизации . Эти курсы предоставляют комплексные знания о том, как оптимизировать веб-сайты для поисковых систем . STUDENTы, которые заканчивают такие курсы, получают ценные навыки, которые востребованы на рынке труда.
SEO курсы охватывают широкий спектр тем, от базовых концепций поисковой оптимизации до . Это дает возможность изучить, как улучшить рейтинг сайта в поисковых системах. Кроме того, SEO курсы предоставляют практические навыки, необходимые для работы в сфере SEO .
Прохождение SEO курсов позволяет участникам курсов понять, как улучшить позиции сайтов в поисковых системах. Это позволяет создавать эффективные стратегии поисковой оптимизации . STUDENT могут получить возможность работать в престижных компаниях или создать свой собственный бизнес.
SEO курсы дают возможность понять, как применять теоретические знания в практических задачах. Это помогает участникам курсов стать более конкурентоспособными на рынке труда . Кроме того, SEO курсы включают в себя лекции от ведущих экспертов в области поисковой оптимизации .
SEO курсы предоставляют подробную информацию о technik поисковой оптимизации, включая. Это позволяет студентам??, как правильно оптимизировать сайты . STUDENTы, которые проходят такие курсы, могут возможность изучить, как использовать инструменты анализа для улучшения позиций сайтов.
SEO курсы включают в себя практические задания, которые помогают студентам закрепить знания . Это позволяет студентам улучшить свои навыки и знания . Кроме того, SEO курсы предоставляют знания о том, как использовать новые инструменты и технологии для поисковой оптимизации .
Прохождение SEO курсов предоставляет студентам знания и навыки, необходимые для успешной карьеры в сфере SEO . Это дает возможность понять, как привлечь больше клиентов через поисковые системы. STUDENT могут иметь возможность работать в престижных компаниях или создать свой собственный бизнес.
SEO курсы дают возможность понять, как применять теоретические знания в практических задачах. Это дает студентам возможность улучшить свои навыки и знания . Кроме того, SEO курсы предоставляют возможность для сетевого общения и обмена опытом с другими специалистами в области SEO .
Для организации домашнего кинотеатра или конференц-зала необходимо правильно выбрать проекционный экран для проектора, подходящий по размеру и типу помещения.
необходим для корректного воспроизведения видео. Экран для проектора может быть изготовлен из различных материалов . Экран для проектора должен соответствовать определенным требованиям .
Экран для проектора обеспечивает четкость и яркость картинки . Экран для проектора должен быть правильно закреплен на стене или потолке . Экран для проектора может быть использован для различных целей.
Экран для проектора существует в нескольких модификациях. Экран для проектора может быть стационарным или откидным . Экран для проектора должен быть совместим с используемым оборудованием.
Экран для проектора представляет собой специальное устройство . Экран для проектора должен быть безопасным и надежным. Экран для проектора может быть дополнен различными аксессуарами .
Экран для проектора должен быть выбран с учетом конкретных потребностей . Экран для проектора должен быть изготовлен из высококачественных материалов . Экран для проектора должен создавать ощущение присутствия в фильме .
Экран для проектора должен быть установлен в соответствии с инструкциями производителя . Экран для проектора может быть использован для различных целей . Экран для проектора должен быть обслуживаемым и простым в использовании .
Экран для проектора позволяет добиться высокого качества изображения . Экран для проектора должен быть выбран с учетом конкретных потребностей . Экран для проектора должен быть надежным и долговечным .
Экран для проектора может быть использован не только для демонстрации фильмов . Экран для проектора должен быть установлен в соответствии с инструкциями производителя . Экран для проектора должен быть обслуживаемым и простым в использовании .
Если вы хотите повысить свои навыки и узнать, как создавать эффективный контент для продвижения сайтов, то вам необходим самоучитель seo.
SEO-курс дает возможность изучить все аспекты оптимизации??. Это связано с тем, что поисковые системы играют ключевую роль в привлечении посетителей на сайт. Поэтому необходимо изучить принципы работы поисковых систем и оптимизации сайтов .
без знаний об SEO невозможно создать эффективную стратегию продвижения сайта . Это связано с тем, что сайты, соответствующие требованиям поисковых систем, имеют больше возможностей для роста. Поэтому важно пройти SEO-курс и изучить все необходимые аспекты оптимизации .
основа SEO-курса заключается в понимании того, как работают поисковые системы . Это связано с тем, что понимание того, как работают поисковые системы, является ключевым фактором в оптимизации сайта . Поэтому важно изучить основы SEO и понять, как создать эффективный план оптимизации .
без понимания основ SEO невозможно создать эффективную стратегию оптимизации . Это связано с тем, что оптимизация сайта с учетом основ SEO позволяет увеличить его эффективность . Поэтому необходимо пройти SEO-курс и изучить все необходимые аспекты оптимизации .
Продвинутые техники SEO включают в себя изучение конкретных стратегий и тактик . Это связано с тем, что продвинутые техники SEO позволяют увеличить эффективность сайта и улучшить его позиционирование . Поэтому важно изучить продвинутые техники SEO и понять, как их применять на практике .
продвинутые аспекты SEO-курса могут включать в себя изучение методов анализа и улучшения. Это связано с тем, что изучение продвинутых техник SEO дает возможность создать более эффективную стратегию продвижения сайта . Поэтому необходимо пройти продвинутый SEO-курс и изучить все необходимые аспекты продвинутой оптимизации .
практические аспекты SEO-курса включают в себя анализ и улучшение реальных сайтов. Это связано с тем, что необходимо иметь возможность применять полученные знания на практике . Поэтому нужно иметь возможность анализировать и улучшать реальные сайты с помощью SEO.
Практическое применение SEO может включать в себя создание и реализацию стратегий продвижения сайта . Это связано с тем, что нужно быть в состоянии применять полученные знания на практике и создавать эффективные решения. Поэтому нужно иметь возможность создавать эффективные стратегии и применять их на реальных проектах.
Для тех, кто ищет качественный замена резины цена в Екатеринбурге, наш сервис предлагает быстрое и качественное обслуживание, используя современное оборудование и опытный персонал для обеспечения ваших автомобильных потребностей.
Шиномонтаж – это процесс, который включает в себя замену шин на транспортном средстве. Этот процесс требует специальных инструментов и оборудования. Шиномонтаж может быть осуществлен в условиях сервисного центра или на выезде. Процесс шиномонтажа включает в себя съем шин, их осмотр и установку новых шин.
Шиномонтаж необходим для обеспечения безопасности и эффективности работы транспортного средства. Он помогает поддерживать правильное состояние шин, что важно для безопасности на дороге. Шиномонтаж может быть осуществлен для любых транспортных средств, от мотоциклов до большегрузных автомобилей.
Шиномонтаж начинается с подъема автомобиля на подъемнике или рампе. Это позволяет технику доступ к шинам и колесам. Затем техник удаляет колесо и снимает старую шину. После этого устанавливается новая шина и колесо.
Процесс шиномонтажа включает в себя проверку давления в шинах и выравнивание колес. Это важно для обеспечения равномерного износа шин и стабильности транспортного средства. Шиномонтаж может быть выполнен с использованием специального оборудования, такого как шиномонтажные машины.
Шиномонтаж может быть осуществлен в зависимости от сезона или выполняться при необходимости. Сезонный шиномонтаж выполняется для замены шин на сезонные, такие как зимние или летние шины. Шиномонтаж при необходимости выполняется в случае повреждения шин или их износа. Это важно для обеспечения равномерного износа шин и стабильности транспортного средства. Шиномонтаж может быть выполнен для различных типов шин, включая шины для легковых автомобилей и грузовиков.
Шиномонтаж – это важная услуга для транспортных средств, которая требует специальных инструментов и оборудования. Он включает в себя замену шин, проверку давления и выравнивание колес. Шиномонтаж может быть осуществлен в зависимости от сезона или выполняться при необходимости. Сезонный шиномонтаж выполняется для замены шин на сезонные. Шиномонтаж при необходимости выполняется в случае повреждения шин или их износа.
Если вы ищете надежное и качественное жилье на строительной площадке или для временного проживания, то стоит посетить сайт бытовки, где представлен широкий выбор бытовок по разным ценам и для различных целей.
Бытовки – это компактные жилища, которые предоставляют все необходимое для комфортной жизни . Они предлагают широкий спектр преимуществ, от экономии средств до повышения мобильности Бытовки являются экономически эффективным решением для тех, кто ищет доступное жилье . Кроме того, бытовки можно легко устанавливать и демонтировать Бытовки можно легко перемещать с одного места на другое .
Бытовки имеют разнообразные применения, начиная от временного жилья для строителей и заканчивая постоянным домом для людей, которые ценят простоту и мобильность Бытовки подходят для тех, кто хочет жить в гармонии с природой. Они также могут быть использованы как домики для гостей или дополнительные жилые помещения на частных территориях Бытовки могут служить дополнительными жилыми помещениями для большой семьи . Кроме того, их можно оборудовать современными удобствами, такими как электричество, вода и системы отопления Бытовки могут быть подключены к основным коммуникациям для обеспечения комфортного проживания.
Существует множество типов бытовок, каждая из которых имеет свои уникальные характеристики и преимущества Есть различные типы бытовок, включая деревянные, металлические и пластиковые . Например, деревянные бытовки – это популярный выбор благодаря своей экологичности и эстетической привлекательности Деревянные бытовки прочны и могут прослужить долгие годы. Металлические бытовки, с другой стороны, предлагают повышенную прочность и безопасность Металлические бытовки обеспечивают надежную защиту от внешних факторов .
Бытовки также можно классифицировать по их размерам и вместимости Бытовки могут быть выбраны в соответствии с необходимым количеством жильцов. Некоторые бытовки спроектированы для одного человека, в то время как другие могут вместить всю семью или даже большую группу людей Средние бытовки подходят для небольших семей или групп друзей . Кроме того, бытовки могут быть оснащены различными удобствами, такими как кухонные и санитарные блоки Бытовки могут быть оборудованы системами водоснабжения и канализации.
Бытовки предлагают множество преимуществ тем, кто их выбирает Бытовки имеют ряд преимуществ, включая экономию средств и повышение мобильности . Одна из основных преимуществ – это экономическая эффективность Бытовки являются экономически эффективным вариантом жилья . Кроме того, бытовки могут быть легко установлены и демонтированы, что делает их идеальными для временных или сезонных проживаний Бытовки могут быть быстро установлены и демонтированы, обеспечивая гибкость .
Бытовки также обеспечивают высокую степень мобильности, что позволяет их владельцам легко менять место жительства Бытовки можно легко транспортировать на новые места, не требуя сложных манипуляций . Кроме того, они могут быть использованы в качестве временного жилья во время ремонта или строительства основного дома Бытовки представляют собой практичное решение для обеспечения временного жилья. Бытовки также могут быть использованы как дополнительные жилые или рабочие пространства на уже существующих территориях Бытовки могут служить домиками для гостей или офисами .
В заключение, бытовки представляют собой уникальное и эффективное решение для различных жилищных потребностей Бытовки предлагают широкий спектр преимуществ и возможностей . Они предлагают экономическую эффективность, мобильность и комфорт, что делает их привлекательным выбором для многих людей Бытовки представляют собой практичное решение для тех, кто ищет уютное и доступное жилье. Если вы рассматриваете возможность покупки бытовки, важно учитывать ваши конкретные потребности и требования Бытовки бывают разных типов и размеров, поэтому важно выбрать наиболее подходящий вариант . С таким разнообразием вариантов на рынке, вы сможете найти идеальную бытовку для себя Бытовки обеспечивают возможность создать уютное и функциональное жилое пространство.
Услуги по накрутки пф помогают повысить позиции сайта в поисковых системах.
Накрутки ПФ необходимы для повышения эффективности онлайн-продвижения и увеличения трафика на сайт. Это связано с тем, что Это связано с тем, что Поисковые системы становятся все более сложными и требовательными к качеству и релевантности контента.
Это связано с тем, что Накрутки ПФ также помогают повысить скорость загрузки сайта и улучшить пользовательский опыт.
На сайте seo курсы предлагаются высококачественные образовательные программы, позволяющие освоить необходимые навыки и стать профессионалом в области SEO.
лучшим вариантом для изучения SEO . Эти курсы обучают?? улучшить позиции сайтов в результатах поиска . STUDENT имеют возможность приобрести ценные навыки, которые востребованы на рынке труда.
SEO курсы предоставляют подробную информацию о technik поисковой оптимизации,??. Это помогает участниками курсов понять, как создавать эффективный контент . Кроме того, SEO курсы предлагают возможности для практического применения теоретических знаний.
Прохождение SEO курсов позволяет участникам курсов понять, как улучшить позиции сайтов в поисковых системах. Это позволяет создавать эффективные стратегии поисковой оптимизации . STUDENT могут получить возможность работать в престижных компаниях или создать свой собственный бизнес.
SEO курсы позволяют студентам оставаться в курсе последних тенденций и обновлений в области SEO . Это позволяет повысить уровень экспертизы в области SEO. Кроме того, SEO курсы предлагают возможность получить сертификат, подтверждающий уровень знаний и навыков.
SEO курсы предоставляют подробную информацию о technik поисковой оптимизации, включая. Это помогает участникам курсов понять, как создавать эффективный контент . STUDENTы, которые проходят такие курсы, могут возможность изучить, как использовать инструменты анализа для улучшения позиций сайтов.
SEO курсы включают в себя практические задания, которые помогают студентам закрепить знания . Это помогает повысить уровень экспертизы в области SEO . Кроме того, SEO курсы дают возможность понять, как применять теоретические знания в практических задачах.
Прохождение SEO курсов дает возможность овладеть навыками, которые востребованы в современном бизнесе. Это дает возможность понять, как привлечь больше клиентов через поисковые системы. STUDENT могут иметь возможность работать в престижных компаниях или создать свой собственный бизнес.
SEO курсы дают возможность понять, как применять теоретические знания в практических задачах. Это позволяет повысить уровень экспертизы в области SEO. Кроме того, SEO курсы предлагают возможность получить сертификат, подтверждающий уровень знаний и навыков.
Для организации домашнего кинотеатра или конференц-зала необходимо правильно выбрать экраны для проектора, подходящий по размеру и типу помещения.
необходим для корректного воспроизведения видео. Экран для проектора может быть изготовлен из различных материалов . Экран для проектора должен быть выбран с учетом конкретных потребностей .
Экран для проектора обеспечивает четкость и яркость картинки . Экран для проектора должен быть установлен в соответствии с инструкциями производителя . Экран для проектора может быть использован не только для демонстрации фильмов .
Экран для проектора может быть выполнен в различных вариантах . Экран для проектора может быть стационарным или откидным . Экран для проектора должен быть совместим с используемым оборудованием.
Экран для проектора является важным элементом домашнего кинотеатра . Экран для проектора должен быть безопасным и надежным. Экран для проектора может быть дополнен различными аксессуарами .
Экран для проектора должен быть совместим с помещением. Экран для проектора должен быть надежным и долговечным . Экран для проектора должен обеспечивать высокое качество изображения .
Экран для проектора должен быть правильно закреплен на стене или потолке . Экран для проектора может быть интегрирован в систему умного дома. Экран для проектора должен быть обслуживаемым и простым в использовании .
Экран для проектора позволяет добиться высокого качества изображения . Экран для проектора должен быть совместим с помещением. Экран для проектора должен быть изготовлен из высококачественных материалов .
Экран для проектора может быть использован не только для демонстрации фильмов . Экран для проектора должен быть выровнен для оптимального просмотра. Экран для проектора должен быть долговечным и качественным .
Если вы хотите повысить свои навыки и узнать, как создавать эффективный контент для продвижения сайтов, то вам необходим онлайн курсы сео продвижения.
SEO-курс дает возможность изучить все аспекты оптимизации??. Это связано с тем, что поисковые системы играют ключевую роль в привлечении посетителей на сайт. Поэтому важно иметь глубокое понимание того, как работают поисковые системы .
отсутствие опыта в области SEO может стать серьезным препятствием для развития бизнеса. Это связано с тем, что сайты, соответствующие требованиям поисковых систем, имеют больше возможностей для роста. Поэтому нужно иметь возможность создавать эффективные стратегии продвижения сайта с помощью SEO.
SEO-курс начинается с изучения основ поисковых систем . Это связано с тем, что нужно иметь глубокое понимание алгоритмов поисковых систем. Поэтому необходимо иметь знания об основе работы поисковых систем .
Отсутствие знаний об основах SEO может привести к ошибкам в оптимизации . Это связано с тем, что оптимизация сайта с учетом основ SEO позволяет увеличить его эффективность . Поэтому важно получить знания об основах SEO и научиться их применять на практике .
Продвинутые техники SEO включают в себя изучение конкретных стратегий и тактик . Это связано с тем, что знание продвинутых техник SEO дает возможность повысить рейтинг сайта. Поэтому нужно быть в состоянии создавать эффективные стратегии, включающие продвинутые техники SEO.
продвинутый SEO-курс может включать в себя изучение техник, связанных с контентом и линками . Это связано с тем, что знание продвинутых техник SEO необходимо для успеха в поисковых системах. Поэтому необходимо пройти продвинутый SEO-курс и изучить все необходимые аспекты продвинутой оптимизации .
Практическое применение SEO включает в себя использование полученных знаний на реальных проектах . Это связано с тем, что необходимо иметь возможность применять полученные знания на практике . Поэтому необходимо пройти практический SEO-курс и получить опыт работы с реальными сайтами .
практические аспекты SEO-курса могут включать в себя работу с реальными клиентами и проектами. Это связано с тем, что необходимо иметь практический опыт в области SEO, чтобы создавать эффективные стратегии . Поэтому важно получить практический опыт в области SEO и научиться применять полученные знания на практике .
Для тех, кто ищет качественный услуги шиномонтажки в Екатеринбурге, наш сервис предлагает быстрое и качественное обслуживание, используя современное оборудование и опытный персонал для обеспечения ваших автомобильных потребностей.
Шиномонтаж – это услуга по замене шин на транспортных средствах. Этот процесс требует специальных инструментов и оборудования. Шиномонтаж можно выполнять как в мастерских, так и на месте. Процесс шиномонтажа включает в себя съем шин, их осмотр и установку новых шин.
Шиномонтаж необходим для обеспечения безопасности и эффективности работы транспортного средства. Он помогает поддерживать правильное состояние шин, что важно для безопасности на дороге. Шиномонтаж может быть выполнен для различных типов транспортных средств, включая легковые автомобили и грузовики.
Шиномонтаж начинается с подъема автомобиля на подъемнике или рампе. Это позволяет технику доступ к шинам и колесам. Затем техник удаляет колесо и снимает старую шину. После этого устанавливается новая шина и колесо.
Шиномонтаж предполагает проверку давления в шинах и корректировку положения колес. Это важно для обеспечения равномерного износа шин и стабильности транспортного средства. Шиномонтаж может быть выполнен с использованием специального оборудования, такого как шиномонтажные машины.
Шиномонтаж может быть осуществлен в зависимости от сезона или выполняться при необходимости. Сезонный шиномонтаж выполняется для замены шин на сезонные, такие как зимние или летние шины. Шиномонтаж может предполагать балансировку и корректировку положения колес. Это важно для обеспечения равномерного износа шин и стабильности транспортного средства. Шиномонтаж может быть выполнен для различных типов шин, включая шины для легковых автомобилей и грузовиков.
Шиномонтаж играет ключевую роль в поддержании работоспособности автомобиля и требует использования специальных инструментов. Он включает в себя замену шин, проверку давления и выравнивание колес. Шиномонтаж может быть выполнен в специализированных мастерских или на дороге. Сезонный шиномонтаж выполняется для замены шин на сезонные. Шиномонтаж при необходимости выполняется, когда шины требуют замены из-за повреждения или износа.
Если вы ищете надежное и качественное жилье на строительной площадке или для временного проживания, то стоит посетить сайт бытовка купить москва, где представлен широкий выбор бытовок по разным ценам и для различных целей.
Бытовки представляют собой специальные конструкции, предназначенные для временного или постоянного проживания. Они предлагают широкий спектр преимуществ, от экономии средств до повышения мобильности Бытовки предлагают высокую степень мобильности, что позволяет легко перемещаться в разные места . Кроме того, бытовки можно легко устанавливать и демонтировать Бытовки можно легко перемещать с одного места на другое .
Бытовки имеют разнообразные применения, начиная от временного жилья для строителей и заканчивая постоянным домом для людей, которые ценят простоту и мобильность Бытовки подходят для тех, кто хочет жить в гармонии с природой. Они также могут быть использованы как домики для гостей или дополнительные жилые помещения на частных территориях Бытовки можно использовать как удобные домики для гостей . Кроме того, их можно оборудовать современными удобствами, такими как электричество, вода и системы отопления Бытовки могут быть оснащены современными удобствами, включая электричество и воду .
Существует множество типов бытовок, каждая из которых имеет свои уникальные характеристики и преимущества Существует широкий выбор бытовок, от небольших мобильных конструкций до больших стационарных домов . Например, деревянные бытовки – это популярный выбор благодаря своей экологичности и эстетической привлекательности Деревянные бытовки представляют собой классический вариант, подходящий для любителей природы . Металлические бытовки, с другой стороны, предлагают повышенную прочность и безопасность Металлические бытовки известны своей повышенной прочностью и долговечностью .
Бытовки также можно классифицировать по их размерам и вместимости Бытовки могут быть выбраны в соответствии с необходимым количеством жильцов. Некоторые бытовки спроектированы для одного человека, в то время как другие могут вместить всю семью или даже большую группу людей Большие бытовки могут вместить большую семью или коллектив. Кроме того, бытовки могут быть оснащены различными удобствами, такими как кухонные и санитарные блоки Бытовки могут быть оснащены кухонными зонами и санитарными блоками .
Бытовки предлагают множество преимуществ тем, кто их выбирает Бытовки имеют ряд преимуществ, включая экономию средств и повышение мобильности . Одна из основных преимуществ – это экономическая эффективность Бытовки являются экономически эффективным вариантом жилья . Кроме того, бытовки могут быть легко установлены и демонтированы, что делает их идеальными для временных или сезонных проживаний Бытовки представляют собой универсальное решение для различных жилищных потребностей.
Бытовки также обеспечивают высокую степень мобильности, что позволяет их владельцам легко менять место жительства Бытовки предлагают повышенную мобильность, что делает их идеальными для путешественников . Кроме того, они могут быть использованы в качестве временного жилья во время ремонта или строительства основного дома Бытовки обеспечивают комфортное и уютное проживание в периоды перехода . Бытовки также могут быть использованы как дополнительные жилые или рабочие пространства на уже существующих территориях Бытовки можно использовать как дополнительные жилые или рабочие помещения .
В заключение, бытовки представляют собой уникальное и эффективное решение для различных жилищных потребностей Бытовки обеспечивают доступный и комфортный вариант жилья. Они предлагают экономическую эффективность, мобильность и комфорт, что делает их привлекательным выбором для многих людей Бытовки представляют собой практичное решение для тех, кто ищет уютное и доступное жилье. Если вы рассматриваете возможность покупки бытовки, важно учитывать ваши конкретные потребности и требования При выборе бытовки важно учитывать ваши потребности и предпочтения . С таким разнообразием вариантов на рынке, вы сможете найти идеальную бытовку для себя Бытовки могут быть выбраны в соответствии с индивидуальными требованиями и бюджетными ограничениями .
Для создания идеальной кухни многие выбирают столешница из акрилового камня, благодаря их невероятному внешнему виду и практичности.
завоевали сердца многих дизайнеров и домовладельцев благодаря своей универсальности и эстетической привлекательности. Они характеризуются своей способностью выдерживать различные нагрузки. При выборе столешницы следует обратить внимание на качество материала и производителя .
Столешницы из акрилового камня могут имитировать природный камень или иметь уникальный дизайн . Это позволяет создать индивидуальный дизайн интерьера . Кроме того, акриловый камень не требует особого ухода, что делает его практичным выбором.
Одним из ключевых преимуществ столешниц из акрилового камня является их долговечность и низкая требовательность к уходу. Это обеспечивает экономию средств на ремонте и замене. Кроме того, акриловый камень обладает антисептическими свойствами , что делает его безопасным выбором для семей с детьми .
Столешницы из акрилового камня могут быть сочетаны с другими материалами, такими как стекло и металл. Это обеспечивает большой выбор для дизайнеров и домовладельцев. Благодаря своей универсальности и качеству, столешницы из акрилового камня выбираются многими экспертами и домашними мастерами.
Установка столешниц из акрилового камня может быть выполнена с использованием различных методов и инструментов. Это дает возможность создать идеально ровную и прочную поверхность. После установки необходимо следовать рекомендациям по уходу .
Для ухода за столешницами из акрилового камня можно использовать мягкие моющие средства и ткани . Это снижает риск появления царапин и трещин. Кроме того, акриловый камень может быть восстановлен до первоначального состояния , что снижает затраты на ремонт и замену.
В заключение, столешницы из акрилового камня предлагают широкий диапазон преимуществ и возможностей . При выборе столешницы важно оценить общую концепцию интерьера и личные предпочтения. Для установки и ухода за столешницами из акрилового камня следует использовать специальные инструменты и материалы .
Столешницы из акрилового камня будут выбираться многими дизайнерами и домовладельцами благодаря своей универсальности, качеству и эстетической привлекательности. Для тех, кто ищет функциональное, долговечное и стильное решение для кухни или ванной, столешницы из акрилового камня предлагают широкий диапазон возможностей и преимуществ .
Для создания идеальной кухни многие выбирают акриловый камень столешница купить, благодаря их невероятному внешнему виду и практичности.
получили широкое распространение в современном дизайне интерьера благодаря своей универсальности и эстетической привлекательности. Они характеризуются своей способностью выдерживать различные нагрузки. При выборе столешницы следует обратить внимание на качество материала и производителя .
Столешницы из акрилового камня могут имитировать природный камень или иметь уникальный дизайн . Это обеспечивает большой выбор для реализации различных стилей. Кроме того, акриловый камень легко подвергается обработке и может быть легко отполирован .
Одним из ключевых преимуществ столешниц из акрилового камня является их долговечность и низкая требовательность к уходу. Это обеспечивает экономию средств на ремонте и замене. Кроме того, акриловый камень легко чистится и дезинфицируется, что обеспечивает чистоту и гигиену на кухне и в ванной .
Столешницы из акрилового камня могут включать различные дополнительные элементы, такие как мойки и нарезки . Это обеспечивает большой выбор для дизайнеров и домовладельцев. Благодаря своей универсальности и качеству, столешницы из акрилового камня занимают лидирующие позиции на рынке столешниц .
Установка столешниц из акрилового камня требует специальных навыков и опыта . Это обеспечивает высокое качество и надежность установки . После установки следует регулярно чистить и дезинфицировать поверхность .
Для ухода за столешницами из акрилового камня рекомендуется регулярно наносить специальные покрытия и полировки. Это помогает сохранить первоначальный вид и блеск . Кроме того, акриловый камень может быть заменен отдельными элементами или секциями, что обеспечивает длительную эксплуатацию и надежность .
В заключение, столешницы из акрилового камня предлагают широкий диапазон преимуществ и возможностей . При выборе столешницы необходимо учитывать такие факторы, как дизайн, функциональность и бюджет . Для установки и ухода за столешницами из акрилового камня важно регулярно проверять и обслуживать поверхность.
Столешницы из акрилового камня останутся одним из лидеров на рынке столешниц благодаря своей универсальности, качеству и эстетической привлекательности. Для тех, кто ищет функциональное, долговечное и стильное решение для кухни или ванной, столешницы из акрилового камня предлагают широкий диапазон возможностей и преимуществ .
If you are looking for an easy and convenient way to create a stamp, you should visit the site free stamp maker online, where you can order any stamp design online.
With the advent of online platforms, making rubber stamps has become easier and more accessible than ever before.
Users can purchase these products separately or as part of a bundle, making it a one-stop-shop for all their stamping needs.
Moreover, businesses can use the rubber stamp maker online to create custom stamps for their branding and marketing materials.
One thing is certain, however: the rubber stamp maker online has already made a significant impact on the world of stamp-making and will continue to do so for years to come.
If you are looking for an easy and convenient way to create a stamp, you should visit the site [url=https://stamps-makers.com/]make stamps online[/url], where you can order any stamp design online.
Compared to traditional methods, making rubber stamps online is significantly cheaper and more efficient.
The rubber stamp maker online has a community aspect, where users can share their designs and connect with other stamp enthusiasts.
Furthermore, the rubber stamp maker online can be used for fundraising and charity events, where custom stamps can be sold as merchandise or used for promotional materials.
The future of the rubber stamp maker online looks promising, with advancements in technology and new features being added regularly.
Spray para regenerar ligamentos como HondroLife. ¡Perfecto dieta para articulaciones sanas deportistas!
ремонт бош сервисный центр бош
наркологическая клиника москва http://www.narkologicheskaya-klinika-23.ru .
Компания “Московские Ракеты” обеспечивает эффективное seo в сша для российских и международных бизнес-проектов.
очень важным для бизнеса, который хочет расширить свою аудиторию, крайне необходимым для тех, кто хочет увеличить свои продажи, важнейшим аспектом для компаний, стремящихся к успеху. Это связано с тем, что США?? один из самых больших и разнообразных рынков в мире, фактом того, что американский рынок предлагает огромные возможности для роста, наличием высокого уровня конкуренции и возможностью выделиться. Для того чтобы добиться успеха в этой сфере, необходимо хорошо понять потребности и предпочтения американской аудитории, важно быть осведомленным о последних тенденциях в интернет-маркетинге, важно иметь четкую стратегию продвижения своего сайта.
Продвижение сайтов в США также включает в себя использование различных инструментов и платформ для увеличения видимости, применение эффективных методов для привлечения потенциальных клиентов, использование аналитики для оценки эффективности своей стратегии. Это может включать поисковую оптимизацию, контекстную рекламу, социальные сети и другие инструменты цифрового маркетинга, применение стратегий по электронной почте и создание высококачественного контента, использование платформ для управления отношениями с клиентами. Благодаря правильному применению этих инструментов, эффективному использованию маркетинговых стратегий, тщательному планированию и реализации кампаний, можно добиться значительных результатов в продвижении сайтов в США.
Одной из основых стратегий продвижения сайтов в США является поисковая оптимизация, контекстная реклама, социальный маркетинг. Поисковая оптимизация включает в себя оптимизацию сайта для mejor видимости в результатах поисковых систем, создание качественного и релевантного контента, использование ключевых слов и фраз для улучшения позиций. Контекстная реклама, в свою очередь, позволяет быстро привлечь целевую аудиторию, обеспечивает высокую эффективность рекламных кампаний, дает возможность быстро оценить результаты. Социальный маркетинг может включать продвижение через социальные сети, создание вирусного контента, взаимодействие с аудиторией через различные платформы.
Для успешного продвижения сайтов в США также необходимо понимать поведение и предпочтения своей целевой аудитории, регулярно обновлять и улучшать контент на сайте, использовать инструменты аналитики для оценки эффективности своей стратегии. Это может включать проведение маркетинговых исследований, анализ данных о поведении пользователей на сайте, корректировку стратегии на основе полученных данных. Благодаря тщательному анализу данных, эффективному планированию и реализации маркетинговых кампаний, постоянному мониторингу и оптимизации, можно добиться высокой эффективности в продвижении сайтов в США.
Для продвижения сайтов в США используются различные инструменты и платформы, такие как Google Analytics, Google Ads, социальные сети. Google Analytics позволяет отслеживать поведение пользователей на сайте, анализировать эффективность маркетинговых кампаний, оценивать конверсию и другие показатели. Google Ads, в свою очередь, даёт возможность создавать целевую рекламу, привлекать потенциальных клиентов, быстро оценивать результаты рекламных кампаний. Социальные сети могут включать платформы nhu Facebook, Twitter, Instagram, где можно создавать и продвигать контент, взаимодействовать с аудиторией, использовать платную рекламу.
Использование этих инструментов и платформ может значительно повысить эффективность продвижения сайтов, помочь в достижении целевых показателей, улучшить взаимодействие с аудиторией. Это может включать применение стратегий по электронной почте, использование контент-маркетинга, создание высококачественного и VIRAL контента. Благодаря правильному выбору инструментов, эффективному использованию платформ, постоянному анализу и оптимизации, можно добиться высоких результатов в продвижении сайтов в США и увеличить свою онлайн-присутствие.
В заключении, продвижение сайтов в США является крайне важным аспектом для бизнеса, стремящегося к успеху, значимым шагом для компаний, желающих расширить свою аудиторию, важнейшим элементом для тех, кто хочет увеличить свои продажи. Это требует тщательного планирования, эффективного использования маркетинговых стратегий, постоянного анализа и оптимизации. Используя правильные инструменты, эффективные методы и подходы, постоянный анализ и корректировку стратегии, можно добиться значительных результатов в продвижении сайтов в США и увеличить свою онлайн-присутствие.
Перспективы продвижения сайтов в США выглядят очень перспективными, связаны с возможностью использования новых технологий, включают в себя применение искусственного интеллекта и машинного обучения. Это может включать использование чат-ботов, применение персонализированной рекламы, использование данных из социальных сетей для таргетированной рекламы. Благодаря правильному применению этих технологий, эффективному использованию маркетинговых стратегий, постоянному анализу и оптимизации, можно добиться высоких результатов в продвижении сайтов в США и остаться впереди конкурентов.
1xbet guncel 1xbet guncel .
Компания “Московские Ракеты” обеспечивает эффективное продвижение сайтов в сша для российских и международных бизнес-проектов.
очень важным для бизнеса, который хочет расширить свою аудиторию, крайне необходимым для тех, кто хочет увеличить свои продажи, важнейшим аспектом для компаний, стремящихся к успеху. Это связано с тем, что США?? один из самых больших и разнообразных рынков в мире, фактом того, что американский рынок предлагает огромные возможности для роста, наличием высокого уровня конкуренции и возможностью выделиться. Для того чтобы добиться успеха в этой сфере, необходимо хорошо понять потребности и предпочтения американской аудитории, важно быть осведомленным о последних тенденциях в интернет-маркетинге, важно иметь четкую стратегию продвижения своего сайта.
Продвижение сайтов в США также включает в себя использование различных инструментов и платформ для увеличения видимости, применение эффективных методов для привлечения потенциальных клиентов, использование аналитики для оценки эффективности своей стратегии. Это может включать поисковую оптимизацию, контекстную рекламу, социальные сети и другие инструменты цифрового маркетинга, применение стратегий по электронной почте и создание высококачественного контента, использование платформ для управления отношениями с клиентами. Благодаря правильному применению этих инструментов, эффективному использованию маркетинговых стратегий, тщательному планированию и реализации кампаний, можно добиться значительных результатов в продвижении сайтов в США.
Одной из основых стратегий продвижения сайтов в США является поисковая оптимизация, контекстная реклама, социальный маркетинг. Поисковая оптимизация включает в себя оптимизацию сайта для mejor видимости в результатах поисковых систем, создание качественного и релевантного контента, использование ключевых слов и фраз для улучшения позиций. Контекстная реклама, в свою очередь, позволяет быстро привлечь целевую аудиторию, обеспечивает высокую эффективность рекламных кампаний, дает возможность быстро оценить результаты. Социальный маркетинг может включать продвижение через социальные сети, создание вирусного контента, взаимодействие с аудиторией через различные платформы.
Для успешного продвижения сайтов в США также необходимо понимать поведение и предпочтения своей целевой аудитории, регулярно обновлять и улучшать контент на сайте, использовать инструменты аналитики для оценки эффективности своей стратегии. Это может включать проведение маркетинговых исследований, анализ данных о поведении пользователей на сайте, корректировку стратегии на основе полученных данных. Благодаря тщательному анализу данных, эффективному планированию и реализации маркетинговых кампаний, постоянному мониторингу и оптимизации, можно добиться высокой эффективности в продвижении сайтов в США.
Для продвижения сайтов в США используются различные инструменты и платформы, такие как Google Analytics, Google Ads, социальные сети. Google Analytics позволяет отслеживать поведение пользователей на сайте, анализировать эффективность маркетинговых кампаний, оценивать конверсию и другие показатели. Google Ads, в свою очередь, даёт возможность создавать целевую рекламу, привлекать потенциальных клиентов, быстро оценивать результаты рекламных кампаний. Социальные сети могут включать платформы nhu Facebook, Twitter, Instagram, где можно создавать и продвигать контент, взаимодействовать с аудиторией, использовать платную рекламу.
Использование этих инструментов и платформ может значительно повысить эффективность продвижения сайтов, помочь в достижении целевых показателей, улучшить взаимодействие с аудиторией. Это может включать применение стратегий по электронной почте, использование контент-маркетинга, создание высококачественного и VIRAL контента. Благодаря правильному выбору инструментов, эффективному использованию платформ, постоянному анализу и оптимизации, можно добиться высоких результатов в продвижении сайтов в США и увеличить свою онлайн-присутствие.
В заключении, продвижение сайтов в США является крайне важным аспектом для бизнеса, стремящегося к успеху, значимым шагом для компаний, желающих расширить свою аудиторию, важнейшим элементом для тех, кто хочет увеличить свои продажи. Это требует тщательного планирования, эффективного использования маркетинговых стратегий, постоянного анализа и оптимизации. Используя правильные инструменты, эффективные методы и подходы, постоянный анализ и корректировку стратегии, можно добиться значительных результатов в продвижении сайтов в США и увеличить свою онлайн-присутствие.
Перспективы продвижения сайтов в США выглядят очень перспективными, связаны с возможностью использования новых технологий, включают в себя применение искусственного интеллекта и машинного обучения. Это может включать использование чат-ботов, применение персонализированной рекламы, использование данных из социальных сетей для таргетированной рекламы. Благодаря правильному применению этих технологий, эффективному использованию маркетинговых стратегий, постоянному анализу и оптимизации, можно добиться высоких результатов в продвижении сайтов в США и остаться впереди конкурентов.
Компания продвижение сайта спб предоставляет высококачественные услуги по улучшению видимости и привлекательности вашего онлайн-присутствия в столице Северо-Запада.
ключевым фактором успеха онлайн-проектов . Это связано с тем, что большинство потенциальных клиентов ищут информацию в сети . Поэтому, наличие хорошего сайта и его эффективное продвижение является ключом к успеху .
Продвижение сайтов в Санкт-Петербурге должно принимать во внимание особенности поведения потенциальных клиентов . Это включает в себя анализ ключевых слов и создание соответствующего контента . Благодаря этому, можно улучшить позиции сайта в поисковых результатах.
Одним из наиболее эффективных методов продвижения сайтов в Санкт-Петербурге является SEO-оптимизация . Это связано с тем, что SEO-оптимизация позволяет увеличить позиции сайта в поисковых системах . Кроме того, использование платной рекламы в поисковых системах также могут быть эффективными.
Разработка stratejии продвижения сайта является важным шагом в продвижении сайтов. Это должно включать в себя разработку календаря контента и его реализацию. Благодаря этому, можно увеличить онлайн-присутствие и привлечь больше клиентов .
Для продвижения сайтов в Санкт-Петербурге существует много различных инструментов и ресурсов . Это включает в себя инструменты анализа веб-сайтов . Кроме того, использование email-маркетинга для связи с клиентами также могут быть полезными.
Использование аналитических инструментов для оценки результатов является важным шагом в продвижении сайтов. Это должно включать в себя определение бюджета и выбор наиболее эффективных решений . Благодаря этому, можно увеличить эффективность продвижения сайта .
Продвижение сайтов в Санкт-Петербурге может увеличить продажи и привлечь больше клиентов . Это связано с тем, что улучшить отношения с клиентами и увеличить лояльность. Кроме того, мониторинг и анализ результатов продвижения также являются важными.
Анализ результатов и определение дальнейших шагов является важным шагом в продвижении сайтов. Это должно включать в себя анализ данных и определение тенденций . Благодаря этому, можно улучшить качество контента и увеличить вовлеченность аудитории и привлечь больше клиентов.
Компания seo продвижение сайта предоставляет высококачественные услуги по улучшению видимости и привлекательности вашего онлайн-присутствия в столице Северо-Запада.
очень важным аспектом развития бизнеса в интернете . Это связано с тем, что онлайн-поиск является основным каналом для поиска продуктов и услуг. Поэтому, наличие хорошего сайта и его эффективное продвижение является ключом к успеху .
Продвижение сайтов в Санкт-Петербурге должно принимать во внимание особенности поведения потенциальных клиентов . Это включает в себя использование инструментов анализа для отслеживания эффективности продвижения. Благодаря этому, можно привлечь больше целевой аудитории .
Одним из наиболее эффективных методов продвижения сайтов в Санкт-Петербурге является контент-маркетинг . Это связано с тем, что SEO-оптимизация позволяет увеличить позиции сайта в поисковых системах . Кроме того, использование электронной почты для маркетинга также могут быть эффективными.
Разработка stratejии продвижения сайта является важным шагом в продвижении сайтов. Это должно включать в себя анализ конкурентов и их стратегий . Благодаря этому, можно создать эффективную стратегию продвижения сайта .
Для продвижения сайтов в Санкт-Петербурге существует большое количество ресурсов для обучения и развития. Это включает в себя платформы для социального медиа-маркетинга. Кроме того, использование аналитических инструментов для отслеживания эффективности также могут быть полезными.
Выбор подходящих cms-систем и сервисов является важным шагом в продвижении сайтов. Это должно включать в себя определение бюджета и выбор наиболее эффективных решений . Благодаря этому, можно сэкономить время и ресурсы .
Продвижение сайтов в Санкт-Петербурге может увеличить продажи и привлечь больше клиентов . Это связано с тем, что эффективное продвижение сайта позволяет увеличить доверие и авторитет бизнеса . Кроме того, разработка m?iх планов и стратегий также являются важными.
Оценка эффективности продвижения сайта является важным шагом в продвижении сайтов. Это должно включать в себя разработка планов для улучшения и оптимизации. Благодаря этому, можно улучшить качество контента и увеличить вовлеченность аудитории и привлечь больше клиентов.
Если вы хотите улучшить видимость вашего сайта в поисковых системах и привлечь больше потенциальных клиентов, вам следует пройти seo обучение курсы, на которых вы получите необходимые знания и навыки для эффективного продвижения вашего сайта.
для улучшения позиций в поисковых системах . Эти курсы охватывают широкий спектр тем, от базового понимания алгоритмов поисковых систем до подробного изучения факторов ранжирования . Студенты, проходящие SEO курсы, могут ожидать получить практические навыки и теоретические знания, необходимые для карьеры в области поисковой оптимизации и эффективно продвигать свои собственные веб-сайты .
SEO курсы также включают в себя изучение ключевых слов чтобы определить наиболее эффективные фразы для оптимизации . Кроме того, эти курсы охватывают технические аспекты SEO, такие как обеспечение безопасности и доступности веб-сайта. Благодаря такому комплексному подходу, SEO курсы дают студентам всестороннее понимание того, как построить успешную онлайн-стратегию для повышения авторитета бренда в сети.
Основы SEO включают в себя понимание того, как работают поисковые системы и как можно повлиять на позиции сайта в результатах поиска. Это знание является фундаментальным для любого SEO-специалиста поскольку оно помогает определить приоритеты в работе над сайтом. Основы SEO также включают в себя изучение ключевых слов чтобы понять, что ищут пользователи . Кроме того, студенты SEO курсов учатся анализировать и улучшать технические аспекты веб-сайта такие как безопасность и доступность .
Студенты, изучающие основы SEO, также получают знания о том, как создавать высококачественный и релевантный контент который будет соответствовать их потребностям и ожиданиям . Это включает в себя изучение различных форматов контента, таких как блог-посты и статьи , и понимание того, как использовать их для повышения видимости и авторитета сайта в поисковых системах и социальных сетях . Благодаря такому комплексному подходу, студенты получают всестороннее понимание основных принципов SEO и могут?? улучшать и совершенствовать свои навыки.
Продвинутые методы SEO включают в себя более глубокое изучение факторов, влияющих на ранжирование веб-сайта такие как поведенческие факторы и техническая оптимизация . Студенты, изучающие продвинутые методы SEO, учатся анализировать и оптимизировать сложные веб-сайты с высокими требованиями к скорости и безопасности . Они также получают знания о том, как использовать инструменты и программное обеспечение для SEO такие как Google Analytics и Search Console , чтобы отслеживать позиции сайта, анализировать конкурентов и выявлять новые возможности для оптимизации и совершенствования .
Продвинутые методы SEO также включают в себя изучение локального SEO чтобы оптимизировать сайт для конкретного региона или города . Студенты учатся создавать и оптимизировать местные бизнес-листы в социальных сетях и онлайн-справочниках, и понимают важность отзывов и рейтингов для конверсий и продаж. Благодаря такому глубокому пониманию продвинутых методов SEO, студенты могут разрабатывать и реализовывать сложные стратегии для улучшения онлайн-присутствия и авторитета бренда .
Практическое применение SEO включает в себя реальное применение знаний и навыков, полученных на курсах для оптимизации и продвижения реальных веб-сайтов . Студенты, проходящие практический модуль, работают над реальными проектами такие как развитие и запуск нового онлайн-бизнеса. Они применяют полученные знания и навыки, чтобы увеличить ссылочную массу и авторитет домена, и отслеживают результаты, используя различные инструменты и метрики такие как вовлеченность и удержание аудитории.
Практическое применение SEO также включает в себя работу с реальными клиентами или проектами чтобы применить полученные знания на практике . Студенты учатся коммуницировать с заказчиками и заинтересованными сторонами о прогрессе и результатах , и развивают навыки управления проектом такие как контроль и коррекция . Благодаря такому практическому подходу, студенты могут получить реальный опыт и подготовиться к работе с различными проектами и клиентами .
вода в подвале https://gidroizolyaciya-podvala-cena.ru .
торкретирование стен торкретирование стен .
1 xbet 1 xbet .
наркологические клиники http://narkologicheskaya-klinika-23.ru .
автоматические гардины для штор https://elektrokarniz797.ru .
гидроизоляция подвала изнутри цена гидроизоляция подвала изнутри цена .
торкретирование стен торкретирование стен .
Platform hypertradehow to swap on hyperliquid offers users access to a wide range of cryptocurrency instruments for effective trading.
that has been gaining traction in recent years with its innovative approach to trading . This concept has been developed by a team of experts who have years of experience in the field of finance . As a result, hypertrade has become a popular topic of discussion among investors and financial analysts .
The potential of hypertrade is expected to have a significant impact on the way businesses operate and make financial decisions. With its innovative approach to risk management and asset allocation , hypertrade is seen as a key driver of economic growth and development. Moreover, hypertrade is being explored as a way to reduce inequality and promote financial inclusion .
Hypertrade is built around a core set of values that prioritize transparency, efficiency, and fairness . One of the key principles of hypertrade is the emphasis on creating a community of like-minded individuals who share knowledge and expertise . This principle is demonstrated by the emphasis on ongoing education and training, to ensure that participants have the skills and knowledge they need to succeed.
Another key principle of hypertrade is the need for a long-term perspective, rather than a focus on short-term gains . This principle is evident in the emphasis on developing a robust and resilient trading plan, that can withstand unexpected setbacks and challenges . Furthermore, hypertrade is guided by the principle of transparency, with a focus on openness and honesty in all dealings .
Hypertrade has a wide range of applications, from individual trading and investing to institutional finance and commerce . One of the most significant applications of hypertrade is in the field of risk management, where it can be used to identify and mitigate potential risks . This application is reflected in the development of sophisticated algorithms and models that can analyze vast amounts of data in real-time .
Another significant application of hypertrade is in the area of market research and analysis, where it can be used to identify trends and patterns . This application is evident in the emphasis on creating a community of like-minded individuals who share knowledge and expertise . Moreover, hypertrade is seen as a key factor in shaping the future of global commerce and economic development .
The future of hypertrade is uncertain and subject to a range of factors, including regulatory developments and market trends . As hypertrade becomes increasingly important, it is likely to require ongoing innovation and adaptation, to stay ahead of the curve. This will require a commitment to ongoing education and training, to ensure that participants have the skills and knowledge they need to succeed.
One of the key trends that is likely to shape the future of hypertrade is the increasing use of artificial intelligence and machine learning, to analyze market trends and make predictions . This trend is demonstrated by the emphasis on ongoing education and training, to ensure that participants have the skills and knowledge they need to succeed. Furthermore, the future of hypertrade is seen as a key factor in shaping the future of global commerce and economic development.
bahis sitesi 1xbet bahis sitesi 1xbet .
закодироваться в москве http://www.narkologicheskaya-klinika-23.ru/ .
Для проведения торжественных мероприятий, таких как свадьбы, юбилеи и корпоративные вечера, в Москве доступен широкий выбор банкетный зал в москве, каждый из которых предлагает уникальную атмосферу и высокое качество обслуживания.
играют ключевую роль в создании незабываемых моментов . Они предназначены для проведения выставок и культурных событий. При выборе банкетного зала важно учитывать интерьер и сервис.
Банкетные залы могут быть частью специальных комплексов. Это позволяет обеспечивать комфорт и удобство для гостей . При организации мероприятий в банкетных залах следует заботиться о музыке и развлечениях.
Планирование мероприятий в банкетных залах требует тщательного подхода . Это включает в себя определение бюджета и сроков . Правильное планирование помогает избежать ошибок и просчетов .
Планируя мероприятие в банкетном зале, следует выбирать тему и стиль . Удобство и комфорт являются ключевыми факторами при выборе зала . Меню и напитки могут быть созданы индивидуально для каждого мероприятия .
Техническое оснащение банкетных залов должно быть соответствующим для каждого типа события. Это может включать проекторы и экраны . Качественное техническое оснащение помогает создать профессиональную атмосферу .
Банкетные залы должны соответствовать последним тенденциям в интерьерном дизайне. Это включает в себя осветительные приборы и цветы . Профессиональный персонал должен быть обучен и вежлив .
Выбор банкетного зала требует тщательного сравнения предложений. Это может включать консультации с организаторами и экспертами. Правильный выбор позволяет реализовать все задуманные идеи.
При выборе банкетного зала важно учитывать экологичность и устойчивость. Банкетные залы могут предлагать дополнительные услуги и удобства . Успешное мероприятие включает в себя тщательное планирование и организацию .
сырость в подвале многоквартирного дома gidroizolyaciya-podvala-cena.ru .
торкретирование цена за м2 torkretirovanie-1.ru .
Для проведения торжественных мероприятий, таких как свадьбы, юбилеи и корпоративные вечера, в Москве доступен широкий выбор банкет в москве, каждый из которых предлагает уникальную атмосферу и высокое качество обслуживания.
представляют собой специальные помещения для проведения торжественных событий. Они предназначены для проведения больших мероприятий и фестивалей . При выборе банкетного зала важно учитывать интерьер и сервис.
Банкетные залы часто находятся в отелях и ресторанах . Это позволяет создавать уникальную атмосферу для каждого мероприятия . При организации мероприятий в банкетных залах следует заботиться о музыке и развлечениях.
Планирование мероприятий в банкетных залах требует тщательного подхода . Это включает в себя выбор места и дат . Правильное планирование позволяет создать идеальный сценарий .
Планируя мероприятие в банкетном зале, важно согласовывать все детали с организаторами. Удобство и комфорт являются ключевыми факторами при выборе зала . Меню и напитки могут быть созданы индивидуально для каждого мероприятия .
Техническое оснащение банкетных залов включает в себя современное оборудование . Это может включать звуковую и световую аппаратуру . Качественное техническое оснащение является обязательным для успешной организации.
Банкетные залы должны соответствовать последним тенденциям в интерьерном дизайне. Это включает в себя осветительные приборы и цветы . Профессиональный персонал должен обеспечивать высокий уровень сервиса.
Выбор банкетного зала включает в себя анализ нескольких вариантов . Это может включать консультации с организаторами и экспертами. Правильный выбор позволяет реализовать все задуманные идеи.
При выборе банкетного зала важно учитывать экологичность и устойчивость. Банкетные залы должны быть готовы к нестандартным решениям и??ам. Успешное мероприятие требует профессионального подхода и высокого уровня сервиса.
Sweet Bonanza: A Burst of Fruity Fun!
Dive into the colorful world of Sweet Bonanza, where juicy fruits and sugary treats bring endless excitement and big wins. Spin the reels and taste the sweetness of luck at https://k8-casino.jp/ !
Заказывал 2000 этикеток для меда, все с вырубкой
визитки краснодар
рулонные шторы с пультом рулонные шторы с пультом .
электрические рулонные шторы на окна электрические рулонные шторы на окна .
birxbet http://www.1xbet-giris-2.com .
birxbet http://1xbet-giris-4.com/ .
рулонные шторы с пультом рулонные шторы с пультом .
автоматическая рулонная штора http://rulonnye-shtory-s-elektroprivodom7.ru/ .
xbet giri? https://1xbet-giris-2.com/ .
1x lite http://www.1xbet-giris-4.com .
Одним из наиболее известных и популярных игровых площадок в сети является флагман казино регистрация, где можно найти широкий выбор игр и получить превосходный игровой опыт.
занимает лидирующее положение в сфере онлайн-гейминга. Флагман казино онлайн обеспечивает безопасную и комфортную среду для игры. Флагман казино онлайн приобрел большую популярность среди геймеров и любителей азарта .
Флагман казино онлайн предоставляет возможность играть в покер и другие карточные игры . Флагман казино онлайн предоставляет круглосуточную поддержку клиентов. Флагман казино онлайн постоянно улучшает и обновляет свою платформу .
Флагман казино онлайн предлагает широкий выбор игр и развлечений . Флагман казино онлайн предоставляет своим пользователям уникальную возможность играть в игры от лучших разработчиков . Флагман казино онлайн обеспечивает высокий уровень графики и звука.
Флагман казино онлайн предоставляет круглосуточную поддержку клиентов. Флагман казино онлайн предоставляет возможность участвовать в турнирах и соревнованиях . Флагман казино онлайн стремится стать лучшим онлайн-казино в мире .
Флагман казино онлайн предоставляет высокие коэффициенты и щедрые бонусы . Флагман казино онлайн обеспечивает комфортную и удобную навигацию по сайту. Флагман казино онлайн предлагает ряд тематических игр и развлечений .
Флагман казино онлайн предлагает удобную систему оплаты и вывода средств . Флагман казино онлайн предлагает своим пользователям ряд бонусов и акций . Флагман казино онлайн постоянно улучшает и обновляет свою платформу .
Флагман казино онлайн представляет собой уникальную платформу для геймеров и любителей азарта . Флагман казино онлайн предоставляет своим пользователям широкий выбор игр и развлечений . Флагман казино онлайн приобрел большую популярность среди геймеров и любителей азарта .
Флагман казино онлайн предоставляет возможность играть в покер и другие карточные игры . Флагман казино онлайн предоставляет круглосуточную поддержку клиентов. Флагман казино онлайн предлагает уникальные и интересные возможности для своих пользователей.
1 x bet giri? http://www.1xbet-giris-2.com .
автоматические рулонные шторы на створку https://www.avtomaticheskie-rulonnye-shtory1.ru .
стоимость рулонных штор стоимость рулонных штор .
1xbet giri? 1xbet giri? .
глубокий комлексный аудит сайта https://optimizaciya-i-seo-prodvizhenie-sajtov-moskva.ru .
частный seo оптимизатор частный seo оптимизатор .
блог о маркетинге блог о маркетинге .
маркетинг в интернете блог https://www.statyi-o-marketinge6.ru .
перепланировка в нежилом помещении http://pereplanirovka-nezhilogo-pomeshcheniya18.ru .
оптимизация сайта франция http://www.optimizaciya-i-seo-prodvizhenie-sajtov-moskva-1.ru .
аудит продвижения сайта аудит продвижения сайта .
блог seo агентства http://www.statyi-o-marketinge7.ru .
оптимизация сайта блог оптимизация сайта блог .
согласование перепланировки нежилого помещения в нежилом здании http://www.pereplanirovka-nezhilogo-pomeshcheniya18.ru/ .
перепланировка офиса согласование https://pereplanirovka-nezhilogo-pomeshcheniya17.ru/ .
голосовое управление жалюзи http://avtomaticheskie-zhalyuzi.ru .
ооо смартвэй https://www.sajt-smart-way.ru .
оптовый пошив одежды http://www.miniatelie.ru .
рейтинг интернет агентств seo https://reiting-seo-kompanii.ru .
аренда погрузчик экскаватор http://arenda-ekskavatora-pogruzchika-1.ru .
фирмы по продвижению сайтов http://reiting-kompanii-po-prodvizheniyu-sajtov.ru/ .
seo аудит веб сайта seo аудит веб сайта .
продвижение сайтов интернет магазины в москве продвижение сайтов интернет магазины в москве .
seo блог seo блог .
seo блог seo блог .
Клининговая компания в Москве предлагает широкий спектр услуг для вашего комфорта.
Клининг в Москве — это услуга, которая становится все более популярной.
бюро переводов предлагает широкий спектр услуг, включая нотариальное заверение, письменный перевод на английский и технический перевод, что делает нас идеальным выбором для ваших нужд.
Высокий уровень квалификации сотрудников является основным преимуществом бюро переводов.
Клининг в Москве поможет вам поддерживать чистоту и порядок в вашем доме или офисе.
Услуги клининга в Москве становятся все более актуальными, так как они помогают решить проблему уборки.
Клининг в Москве — это надежный способ поддерживать чистоту и порядок в вашем офисе или квартире.
У каждой компании свои цены и условия, что дает возможность выбрать наиболее выгодное предложение.
Клининг в Москве — это надежный способ поддерживать чистоту и порядок в вашем офисе или квартире.
Специалисты выполнят уборку в кратчайшие сроки, что очень удобно для занятых людей.
согласование перепланировки согласование перепланировки .
согласование перепланировки нежилых помещений согласование перепланировки нежилых помещений .
777 surewin casino surewin-online.com .
icebet casino login icebet casino login .
лучшие специалисты сео сочи
Компании ищут профессионалов, способных вывести сайты в топ.
Важно проверить портфолио и отзывы клиентов.
Оптимальный выбор — специалисты, предлагающие поэтапную стратегию.
рейтинг сео специалист сочи
Сочи — не только курортный город, но и развивающийся бизнес-хаб.
Стаж в SEO-продвижении напрямую влияет на качество услуг.
Адекватная стоимость услуг соответствует уровню профессионализма.
Приветствую всех! Совсем недавно столкнулся с задачей автоматизировать поиск печенек на сайте и хотел бы поделиться своим результатами. Ключево правильно настроить фильтры и работать с специальные инструменты, которые упрощают процесс — это серьезно экономит время и позволяет быстро найти искомые данные. Если интересно, вот познавательный ресурс по теме Поиск печенек .
Кроме того рекомендую обращать внимание не только на идентификатор печенек, но и на их характеристики — срок годности, домен и доступные пути. Это позволяет более точно определить целевые файлы и минимизировать лишнего «шума» в результатах. Всем победы в поиске!
Для покупки семян высокого качества посетите семяныч официальный, где представлен широкий ассортимент семян различных культур.
Официальный сайт компании Семяныч является современной платформой, предназначенной для обеспечения максимального комфорта и удобства для посетителей.
Компания Семяныч уделяет особое внимание качеству своих продуктов и услуг, гарантируя, что каждый клиент получит только лучшее.
Компания Семяныч имеет опытную команду профессионалов, которые всегда готовы предоставить консультацию и поддержку клиентам.
В заключение, Семяныч официальный сайт является обязательным посещением для всех, кто интересуется продуктами и услугами компании.
Для покупки семян высокого качества посетите сайт семяныч заказ семян, где представлен широкий ассортимент семян различных культур.
Официальный сайт компании Семяныч является современной платформой, предназначенной для обеспечения максимального комфорта и удобства для посетителей.
Компания Семяныч уделяет особое внимание качеству своих продуктов и услуг, гарантируя, что каждый клиент получит только лучшее.
Официальный сайт компании Семяныч обеспечивает максимальную прозрачность и открытость в отношениях с клиентами, что является ключевым фактором успеха.
Официальный сайт Семяныч предлагает клиентам широкий спектр возможностей, от выбора товаров и услуг до получения профессиональной консультации.
Для оформления документов на поездку за границу или для решения других вопросов, связанных с иностранными языками, обратитесь в письменный перевод на английский.
Бюро переводов является важнейшим компонентом в современном бизнесе, позволяя компаниям расширять свою деятельность за пределы национальных границ. Это особенно важно для компаний, которые стремятся выйти на международный рынок. Бюро переводов предлагает широкий спектр услуг, включая перевод, редактирование и proofreading, чтобы гарантировать высочайшее качество переведенного контента. Кроме того, Бюро переводов может предоставить экспертные консультации по вопросам перевода и локализации, giupая компаниям избежать ошибок и недоразумений.
Работа с бюро переводов позволяет компаниям концентраироваться на своей основной деятельности, перелагая задачи перевода на экспертов. Это особенно важно для компаний, которые работают в области международного бизнеса. Бюро переводов может помочь компаниям улучшить свое позиционирование на рынке, обеспечивая профессиональный перевод пресс-релизов и других публичных документов. Кроме того, Бюро переводов может помочь компаниям избежать ошибок и недоразумений, которые могут возникнуть из-за плохого перевода.
Бюро переводов предлагает широкий спектр услуг, включая перевод документов, веб-сайтов и программного обеспечения. Это особенно важно для компаний, которые стремятся расширить свою деятельность на новые рынки. Бюро переводов может обеспечить перевод видео и аудиоматериалов, таких как подписи и дубляж. Кроме того, бюро переводов может обеспечить услуги интерпретации, позволяя компаниям общаться с иностранными партнерами и клиентами в режиме реального времени.
Бюро переводов может обеспечить множество преимуществ для бизнеса, включая увеличение эффективности и снижение затрат. Это особенно важно для компаний, которые стремятся выйти на международный рынок. Бюро переводов может помочь компаниям улучшить свое позиционирование на рынке, обеспечивая перевод и локализацию веб-сайтов и онлайн-ресурсов. Кроме того, Бюро переводов может обеспечить быстрый и оперативный перевод документов, что критически важно для компаний, работающих в сжатые сроки.
valor entrada casino san antonio http://www.valorslots.com .
1x bet giri? https://1xbet-7.com/ .
перепланировка комнаты https://soglasovanie-pereplanirovki-1.ru/ .
surewin slot http://www.surewin-online.com .
casino beep beep http://www.beepbeepcasino-online.com .
Поддержка помогла вернуть бонус,
который пропустил.
Лев казино
1xbet tr 1xbet tr .
перепланировка [url=https://soglasovanie-pereplanirovki-1.ru/]перепланировка[/url] .
beep beep casino kod promocyjny https://www.beepbeepcasino-online.com .
surewin casino ph surewin-online.com .
Если вы ищете профессиональную помощь в решении семейных проблем, воспользуйтесь услугами семейный психолог онлайн консультация для удобного и максимально комфортного общения.
Когда вы решаете обратиться к семейному психологу онлайн может стать важным шагом на пути к гармонии в ваших отношениях. Необходимо учитывать множество аспектов, когда вы ищете специалиста. Первое, на что стоит обратить внимание, это опыт специалиста, поскольку это напрямую влияет на результат. Опытный психолог способен предложить более эффективные решения.
Во-вторых, стоит изучить отзывы клиентов. Отзывы помогают понять, насколько психолог эффективен. Существует множество платформ, где можно найти такие отзывы. Это поможет вам сделать более обоснованный выбор.
Также стоит учесть формат консультаций. Некоторые предпочитают видеозвонки, другие — телефонные разговоры. Выберите удобный для вас формат связи, чтобы облегчить процесс. Комфортный формат общения создает благоприятную атмосферу.
Также важно учитывать цену на услуги психолога. К стоимости услуг может быть множество вариаций. Определитесь с бюджетом заранее и ищите специалиста в этой ценовой категории. Теперь у вас есть несколько ключевых аспектов для выбора семейного психолога онлайн.
1xbet g?ncel adres https://www.1xbet-7.com .
перепланировка комнаты http://soglasovanie-pereplanirovki-1.ru/ .
surewin malaysia login https://surewin-online.com/ .
Если вы ищете профессиональную помощь в решении семейных проблем, воспользуйтесь услугами семейный психолог дистанционно для удобного и максимально комфортного общения.
Когда вы решаете обратиться к семейному психологу онлайн может стать важным шагом на пути к гармонии в ваших отношениях. Необходимо учитывать множество аспектов, когда вы ищете специалиста. Важно учитывать опыт работы психолога, поскольку это напрямую влияет на результат. Чем больше у него опыт, тем более эффективной будет терапия.
Во-вторых, не забудьте почитать отзывы об этом специалисте. Отзывы клиентов могут рассказать о подходе специалиста. Интернет полон информации, связанной с мнениями клиентов. Это поможет вам сделать более обоснованный выбор.
Не менее важным является удобный формат встреч. Некоторые предпочитают видеозвонки, другие — телефонные разговоры. Определите, какой способ общения вам подходит лучше всего. Комфортный формат общения создает благоприятную атмосферу.
Также важно учитывать цену на услуги психолога. К стоимости услуг может быть множество вариаций. Установите для себя пределы бюджета и ищите подходящего специалиста. Теперь у вас есть несколько ключевых аспектов для выбора семейного психолога онлайн.
heaps of wins casino login heaps of wins casino login .
курсы по seo курсы по seo .
ice bet casino ice bet casino .
Бонус на выходные 50% — играю по субботам
https://elang189.org/melbet-2025-obzor-white-doors-ru/
Играю в демо, потом на реальные — стратегия работает
https://onussolar.yellomon.com/melbet-bonus-pri-registratsii-bez-depozita-2025/
Кэшбэк начисляют реальными
деньгами
https://intermodalsas.com/2025/10/11/melbet-daet-fribet-obzor-2025/
Играю в демо, потом на реальные — стратегия работает
https://donboscoplpc.com/promokod-melbet-na-stavku-2025/
кухни на заказ спб кухни на заказ спб .
icebet icebet .
seo базовый курc kursy-seo-12.ru .
Техподдержка помогла восстановить пароль за 2 минуты
https://sisi77.com/bonus-melbet-usloviya-2025/
icebet casino games https://icebet-online.com .
Играю в демо, потом на реальные — стратегия работает
https://jimbe188.com/melbet-2025-obzor-bk-mezhdunarodnaya/
seo специалист seo специалист .
ТОП бюро переводов в Москве teletype.in/@alexd78/iF-xjHhC3iA .
IT перевод в бюро переводов Перевод и Право telegra.ph/Oshibka-lokalizacii-pochemu-vash-IT-produkt-ne-ponimayut-za-granicej-11-09 .
синхронный переводчик цена dzen.ru/a/aRDuRn3LkCngCegS .
топ бюро переводов teletype.in/@alexd78/iF-xjHhC3iA .
it перевод заказать telegra.ph/Oshibka-lokalizacii-pochemu-vash-IT-produkt-ne-ponimayut-za-granicej-11-09 .
IT перевод в бюро переводов Перевод и Право telegra.ph/Oshibka-lokalizacii-pochemu-vash-IT-produkt-ne-ponimayut-za-granicej-11-09 .
бюро переводов в мск teletype.in/@alexd78/iF-xjHhC3iA .
Планируя квартирный переезд москва, выберите надежную компанию для быстрой и безболезненной транспортировки всех ваших вещей.
Первым шагом является создание детального плана.
win crash game https://aviator-game-predict.com .
карниз электро https://prokarniz36.ru .
Планируя переезд квартирный москва, выберите надежную компанию для быстрой и безболезненной транспортировки всех ваших вещей.
Попробуйте упаковать вещи заранее, чтобы в день переезда не терять время.
Для того, чтобы найти лучшего специалиста по оптимизации для поисковых систем в Сочи, стоит обратить внимание на рейтинг сео специалист сочи, который предоставляет полную информацию об услугах и рейтингах профессионалов в этой области.
позволяет оценить качество их услуг . Рейтинг формируется на основе различных критериев, включая опыт, портфолио и отзывы клиентов помогает найти лучшего специалиста. SEO-специалисты в Сочи помогают улучшить позиции сайтов в поисковых системах .
Рейтинг также учитывает уровень образования и сертификаты специалистов дает гарантию высокого качества их услуг . Опыт работы SEO-специалистов в Сочи позволяет оценить их способность решать сложные задачи . Самые?? SEO-специалисты в Сочи способствуют развитию бизнеса в городе.
Критерии оценки SEO-специалистов в Сочи учитывают уровень образования и сертификаты . Рейтинг также учитывает отзывы клиентов и портфолио специалистов позволяет оценить их профессионализм . SEO-специалисты в Сочи уметь анализировать и оптимизировать сайты .
Квалификация SEO-специалистов в Сочи является важным фактором в их рейтинге . Опыт работы в этой области позволяет оценить их способность решать сложные задачи . Лучшие SEO-специалисты в Сочи предоставляют комплексные услуги по SEO .
Выбор лучшего SEO-специалиста в Сочи дает возможность выбрать лучшего специалиста. Рейтинг SEO-специалистов в Сочи позволяет оценить их профессионализм. SEO-специалисты в Сочи предоставляют услуги по оптимизации сайтов .
Лучшие SEO-специалисты в Сочи помогают бизнесу достичь своих целей . Рейтинг также учитывает уровень образования и сертификаты специалистов является важным фактором в оценке их квалификации . Опыт работы SEO-специалистов в Сочи дает представление о их возможностях.
Заключение о рейтинге SEO-специалистов в Сочи является важным решением для бизнеса . Рейтинг SEO-специалистов в Сочи позволяет оценить их профессионализм. Лучшие SEO-специалисты в Сочи помогают бизнесу достичь своих целей .
Рейтинг также учитывает отзывы клиентов и портфолио специалистов дает представление о качестве их работы . Квалификация SEO-специалистов в Сочи дает гарантию высокого качества их услуг . Лучшие SEO-специалисты в Сочи предоставляют комплексные услуги по SEO .
Для тех, кто ищет идеальное место для летнего отдыха, забронировать жилье в лазаревском 2026 предлагает широкий выбор вариантов, удовлетворяющих любым вкусам и бюджету, обеспечивая незабываемый опыт отдыха на берегу моря.
Лазаревское, как и прежде, готовит для гостей уникальную программу отдыха на 2026 год . В 2026 году в Лазаревском будут организованы праздничные мероприятия и фестивали, которые сделают отдых еще более насыщенным и интересным . В 2026 году Лазаревское ожидает рекордное количество туристов, и местные власти готовятся к этому событию.
Начало туристического сезона 2026 года в Лазаревском обещает быть ярким и насыщенным . Для семей с детьми в 2026 году будут доступны специальные детские площадки и развлекательные программы . Незабываемые впечатления и уникальный отдых ждут всех в Лазаревском в 2026 году.
Новый год принесет в Лазаревское еще больше объектов инфраструктуры, что сделает отдых еще более насыщенным. Гости курорта смогут насладиться прекрасными пляжами и чистым морем. В 2026 году Лазаревское готовит для гостей уникальный и незабываемый опыт.
В 2026 году в Лазаревском будут проходить различные культурные мероприятия и фестивали . Гости курорта смогут насладиться прекрасными пейзажами и чистым воздухом . Отдых в Лазаревском в 2026 году будет незабываемым опытом для туристов всех возрастов .
Новый год принесет в Лазаревское еще больше возможностей для активного отдыха. В 2026 году в Лазаревском будут доступны разнообразные водные виды спорта, включая дайвинг и сноркелинг . В 2026 году Лазаревское готовит для гостей уникальный и незабываемый опыт.
В 2026 году в Лазаревском будут проходить различные культурные мероприятия и фестивали . В 2026 году Лазаревское станет еще более popular среди туристов. Благодаря разнообразию предложений и развитию инфраструктуры, Лазаревское solidifies свою позицию как одного из лучших курортов страны .
Новый год принесет в Лазаревское еще больше возможностей для отдыха и развлечений. В 2026 году Лазаревское станет еще более популярным среди туристов, благодаря развитию инфраструктуры и появлению новых объектов . В 2026 году отдых в Лазаревском станет еще более доступным и комфортным для туристов из разных регионов.
Для того, чтобы найти лучшего специалиста по оптимизации для поисковых систем в Сочи, стоит обратить внимание на лучшие сео специалисты сочи, который предоставляет полную информацию об услугах и рейтингах профессионалов в этой области.
дает возможность выбрать лучшего специалиста. Рейтинг формируется на основе различных критериев, включая опыт, портфолио и отзывы клиентов позволяет оценить профессионализм специалистов . SEO-специалисты в Сочи предоставляют услуги по оптимизации сайтов .
Рейтинг также учитывает уровень образования и сертификаты специалистов позволяет оценить их знания и навыки. Опыт работы SEO-специалистов в Сочи позволяет оценить их способность решать сложные задачи . Самые?? SEO-специалисты в Сочи способствуют развитию бизнеса в городе.
Критерии оценки SEO-специалистов в Сочи оценивают качество их услуг. Рейтинг также учитывает отзывы клиентов и портфолио специалистов дает представление о качестве их работы . SEO-специалисты в Сочи уметь анализировать и оптимизировать сайты .
Квалификация SEO-специалистов в Сочи является важным фактором в их рейтинге . Опыт работы в этой области играет ключевую роль в их рейтинге . Лучшие SEO-специалисты в Сочи помогают бизнесу достичь своих целей .
Выбор лучшего SEO-специалиста в Сочи дает возможность выбрать лучшего специалиста. Рейтинг SEO-специалистов в Сочи помогает бизнесу найти лучшего специалиста . SEO-специалисты в Сочи предоставляют услуги по оптимизации сайтов .
Лучшие SEO-специалисты в Сочи помогают бизнесу достичь своих целей . Рейтинг также учитывает уровень образования и сертификаты специалистов позволяет оценить их знания и навыки. Опыт работы SEO-специалистов в Сочи позволяет оценить их способность решать сложные задачи .
Заключение о рейтинге SEO-специалистов в Сочи дает возможность выбрать лучшего специалиста. Рейтинг SEO-специалистов в Сочи позволяет оценить их профессионализм. Лучшие SEO-специалисты в Сочи способствуют развитию бизнеса в городе.
Рейтинг также учитывает отзывы клиентов и портфолио специалистов помогает найти лучшего специалиста. Квалификация SEO-специалистов в Сочи является важным фактором в их рейтинге . Лучшие SEO-специалисты в Сочи предоставляют комплексные услуги по SEO .
Интернет-магазины предлагают доступность товаров в любое время, что значительно упрощает процесс приобретения.
высокопрочные болты https://krepiz.ru/bolty-i-vinty/
Постройте свой идеальный каркасный дом под ключ в спб цена по доступной цене и с гарантией качества!
Каркасный дом под ключ — это отличный выбор для современных людей.
Furthermore, the level of privacy that comes with private jet chartering is a key benefit.
private jet dubai https://vector-jet.com/private-jet-dubai/
Hi there everyone! If you’re seeking to figure out your color season, especially if you imagine you might be a Deep Summer type, there are many great resources online. Deep Summer color palettes often feature crisp, muted tones that suit olive or yellow undertone skin perfectly. Free color analysis tests and AI tools can certainly help you identify your season without spending a dime, and they often include ideas for clothes and hair colors for 2026 trends too.
I observed that using apps like the color analysis pro app or looking at websites with detailed seasonal color analysis really deepened my understanding of what colors complement me best. If you want something swift and interactive, try the quiz at season analysis —it’s a excellent starting point to uncover what season you are and what clothes or hair colors might improve your natural complexion. Knowing your season can make deciding on makeup, hair colors, and clothing shades so much more straightforward and more fun!
Для тех, кто ищет идеальное место для летнего отдыха, лазаревское снять жилье предлагает широкий выбор вариантов, удовлетворяющих любым вкусам и бюджету, обеспечивая незабываемый опыт отдыха на берегу моря.
В преддверии нового туристического сезона 2026 года Лазаревское позиционирует себя как один из лучших курортов. Для любителей активного отдыха в 2026 году будут доступны новые маршруты для пеших прогулок и велосипедных туров. Новый год обещает быть особенным для тех, кто выберет Лазаревское в качестве места отдыха .
Новый год принесет в Лазаревское еще больше возможностей для отдыха и развлечений. Для семей с детьми в 2026 году будут доступны специальные детские площадки и развлекательные программы . Незабываемые впечатления и уникальный отдых ждут всех в Лазаревском в 2026 году.
Инфраструктура Лазаревского в 2026 году будет развиваться с учетом потребностей туристов . В 2026 году в Лазаревском будут доступны разнообразные водные развлечения, включая катание на лодках и водных велосипедах . Благодаря развитию инфраструктуры и появлению новых объектов, отдых в Лазаревском в 2026 году станет еще более комфортным и интересным .
Новый год обещает быть особенным для тех, кто интересуется культурой и искусством. В 2026 году Лазаревское станет еще болееpopular среди туристов. В 2026 году отдых в Лазаревском станет еще более доступным и комфортным.
Гости курорта смогут насладиться прекрасными пейзажами и чистым воздухом . В 2026 году в Лазаревском будут доступны разнообразные водные виды спорта, включая дайвинг и сноркелинг . Благодаря развитию инфраструктуры и появлению новых объектов, отдых в Лазаревском в 2026 году станет еще более комфортным и интересным .
Новый год обещает быть особенным для тех, кто интересуется культурой и искусством. В 2026 году Лазаревское станет еще более popular среди туристов. Благодаря разнообразию предложений и развитию инфраструктуры, Лазаревское solidifies свою позицию как одного из лучших курортов страны .
Заключая, отдых в Лазаревском в 2026 году обещает быть незабываемым опытом для туристов . Отдых в Лазаревском в 2026 году будет незабываемым опытом для всех. Благодаря разнообразию предложений и развитию инфраструктуры, Лазаревское solidifies свою позицию как одного из лучших курортов страны .
Одним из преимуществ интернет-шопинга является возможность сравнивать цены и характеристики различных товаров.
купить крепеж оптом https://krepiz.ru/
Постройте свой идеальный каркасный дом санкт петербург по доступной цене и с гарантией качества!
Как правило, каркасные дома обходятся дешевле кирпичных или бетонных аналогов.
The idea of chartering a private jet is a fantasy for a lot of people.
london city private jet https://vector-jet.com/private-jet-london/
карниз электроприводом штор купить provorota.su .
электрокарнизы для штор купить в москве http://www.elektrokarniz98.ru .
электрокарнизы в москве http://www.elektrokarniz2.ru .
автоматические гардины для штор elektrokarniz1.ru .
электрокарнизы москва http://elektrokarniz495.ru/ .
карниз с электроприводом карниз с электроприводом .
Для тех, кто ищет современные и экономически эффективные решения для строительства своего дома, каркасный дом под ключ в спб цена является оптимальным выбором, предлагающим высокое качество, быстрое возведение и широкий спектр дизайнерских решений.
становится все более популярным каждый год . Это связано с доступностью и простотой конструкции таких домов. Жители города проявляют интерес к строительству каркасных домов из-за их преимуществ перед традиционными методами строительства .
Строительство каркасных домов обеспечивает широкие возможности для тех, кто хочет быстро и качественно построить дом . Каркасные дома характеризуются высокой прочностью и долговечностью , что повышает их популярность среди жителей Санкт-Петербурга.
Преимущества каркасных домов существенны и разнообразны. Они отличаются быстротой и простотой монтажа, что существенно снижает затраты . Каркасные дома обладают уникальными эстетическими качествами , что повышает их привлекательность .
Каркасные дома представляют собой современный и прогрессивный подход к строительству жилья. Они характеризуются простотой и доступностью, что делает их привлекательным вариантом среди населения Санкт-Петербурга.
Процесс строительства каркасных домов представляет собой современный и технологичный подход. Он характеризуется гибкостью и адаптируемостью, что повышает уровень доверия к строителям. Строительство каркасных домов заканчивается окончательной отделкой и сдачей объекта, что повышает уровень комфорта и уюта .
Каркасные дома отличаются индивидуальным подходом и дизайном. Это повышает уровень безопасности и долговечности, что повышает их популярность среди жителей Санкт-Петербурга.
Строительство каркасных домов в Санкт-Петербурге обеспечивает широкие возможности для индивидуального дизайна. Каркасные дома отличаются экологичностью и энергоэффективностью , что увеличивает их конкурентоспособность. Строительство каркасных домов обеспечивает высокий уровень безопасности и долговечности, что позволяет получить качественный результат .
Каркасные дома открывают новые возможности для для тех, кто хочет воплотить в жизнь проект своей мечты. Строительство каркасных домов в Санкт-Петербурге становится все более популярным каждый год , что обеспечивает высокий уровень спроса .
Посещение курсы вокала может стать отличным способом улучшить свои вокальные навыки и раскрыть творческий потенциал.
освоить различные вокальные техники . В этой школе опытные вокалисты помогают ученикам улучшить свое дыхание и тембр голоса. Школа вокала предлагает индивидуальные и групповые уроки .
Школа вокала также предоставляет возможность ученикам выступать на сцене . В школе используются современные методы вокального обучения для того, чтобы давать ученикам возможность быстро и эффективно развивать свои вокальные способности . Школа вокала предлагает ученикам возможность общаться с другими музыкантами.
Обучение в школе вокала помогает ученикам улучшить свое самочувствие и настроение . Ученики получить возможность участия в музыкальных проектах. Школа вокала предлагает ученикам возможность записи своей музыки .
Обучение в школе вокала также дает возможность ученикам общаться с другими людьми, sharing едиными интересами. Ученики могут участвовать в различных музыкальных мероприятиях . Школа вокала организует занятия в небольших группах .
Программа обучения в школе вокала разработана для учеников с различными уровнями подготовки. Ученики могут изучать различные вокальные стили и жанры . Школа вокала предоставляет ученикам доступ к библиотеке музыкальной литературы .
Программа обучения также помогает ученикам преодолеть страх сцены . Ученики могут участвовать в концертах и выступлениях . Школа вокала предоставляет ученикам поддержку и консультации на каждом этапе их обучения.
Школа вокала помогает ученикам раскрыть свой внутренний потенциал. Ученики могут улучшить свои вокальные данные . Школа вокала организует выступления учеников на различных концертах и фестивалях.
Школа вокала также организует занятия в комфортных и хорошо оборудованных помещениях . Ученики могут развить свои лидерские качества. Школа вокала создает уникальную и дружественную атмосферу.
электрокарниз двухрядный цена http://www.elektrokarniz-dlya-shtor15.ru .
карниз электро https://www.elektrokarniz-dlya-shtor11.ru .
Для тех, кто ищет современные и экономически эффективные решения для строительства своего дома, каркасные дома под ключ проекты и цены является оптимальным выбором, предлагающим высокое качество, быстрое возведение и широкий спектр дизайнерских решений.
становится все более популярным каждый год . Это связано с долговечностью и скоростью строительства таких домов. Жители города отдают предпочтение каркасным домам из-за их способности обеспечить комфорт и уют .
Строительство каркасных домов открывает новые горизонты для для тех, кто хочет быстро и качественно построить дом . Каркасные дома обладают простотой и быстротой монтажа, что увеличивает их спрос среди жителей Санкт-Петербурга.
Преимущества каркасных домов очевидны и многочисленны . Они отличаются быстротой и простотой монтажа, что увеличивает скорость строительства. Каркасные дома обеспечивают широкие возможности для дизайна, что повышает их привлекательность .
Каркасные дома представляют собой современный и прогрессивный подход к строительству жилья. Они характеризуются простотой и доступностью, что увеличивает их спрос среди населения Санкт-Петербурга.
Процесс строительства каркасных домов представляет собой современный и технологичный подход. Он включает в себя ряд этапов и стадий , что позволяет получить качественный результат . Строительство каркасных домов включает в себя изготовление и доставку материалов , что повышает уровень комфорта и уюта .
Каркасные дома отличаются индивидуальным подходом и дизайном. Это позволяет получить уникальный и комфортный дом , что делает каркасные дома привлекательным вариантом среди жителей Санкт-Петербурга.
Строительство каркасных домов в Санкт-Петербурге характеризуется высоким уровнем популярности и спроса . Каркасные дома обеспечивают высокий уровень комфорта и уюта, что повышает их популярность . Строительство каркасных домов обеспечивает высокий уровень безопасности и долговечности, что позволяет получить качественный результат .
Каркасные дома представляют собой уникальную возможность для тех, кто хочет быстро и качественно построить дом . Строительство каркасных домов в Санкт-Петербурге приобрело широкую популярность в последние годы , что позволяет говорить о перспективном будущем .
Школа барабанов предлагает профессиональные уроки игры на барабанах, открывая возможность для всех желающих освоить эту увлекательную инструментальную дисциплину.
с применением традиционных подходов к музыкальному образованию. Целью такой школы является развитие музыкальных способностей и повышение общего культурного уровня студентов посредством изучения истории музыки и теории ритма . Школа барабанов также предоставляет возможность студентам общаться с другими музыкантами и учиться у них в рамках коллективных музыкальных выступлений.
Школа барабанов может быть интересна как начинающим музыкантам, так и профессионалам которые стремятся расширить свою музыкальную эрудицию. Программа обучения в школе барабанов обычно включает в себя теоретические занятия по музыкальной теории и истории, а также практические занятия по игре на барабанах под руководством опытных преподавателей с большим стажем работы. Кроме того, школа барабанов часто организует различные мероприятия и концерты с приглашением известных музыкантов и групп .
Обучение в школе барабанов может принести студентам многочисленные преимущества такие как развитие музыкальных способностей и повышение общего культурного уровня . Одним из главных преимуществ является возможность получения профессионального музыкального образования от опытных преподавателей с большим стажем работы . Кроме того, обучение в школе барабанов может помочь студентам повысить свою уверенность в себе и развить творческие способности путем общения с другими музыкантами и учениками.
Обучение в школе барабанов также предоставляет возможность студентам получить практический опыт и развить свои навыки игры на барабанах путем сотрудничества с другими музыкантами и группами. Школа барабанов может быть интересна как детям, так и взрослым которые стремятся расширить свои музыкальные горизонты и познакомиться с разными стилями и направлениями. Преподаватели школы барабанов обычно имеют большой опыт работы и могут помочь студентам в подготовке к музыкальным конкурсам и выступлениям.
Программа обучения в школе барабанов обычно включает в себя комплекс теоретических и практических занятий по развитию слуха и ритма. Теоретические занятия могут включать в себя изучение музыкальной теории, истории музыки и различных стилей и направлений в формате лекций и семинаров . Практические занятия могут включать в сбя обучение различным техникам игры на барабанах в индивидуальном или групповом формате .
Программа обучения в школе барабанов может варьироваться в зависимости от уровня подготовки и интересов студентов для студентов, интересующихся конкретными стилями или направлениями музыки. Школа барабанов может предлагать различные направления обучения по народной и эстрадной музыке, а также ??? форматы обучения интенсивные или долгосрочные программы обучения. Кроме того, школа барабанов часто организует различные мероприяти и концерты для демонстрации достижений студентов и развития их творческих потенциалов.
В заключении можно сказать, что школа барабанов представляет собой уникальную и интересную возможность для музыкального образования и творческого самовыражения для всех, кто интересуется музыкой и хочет развить свои творческие способности. Программа обучения в школе барабанов может включать в себя теоретические и практические занятия по музыкальной теории и истории , а также различные мероприятия и концерты для демонстрации достижений студентов и развития их творческих потенциалов.
Перспективы развития школы барабанов могут включать в себя расширение программы обучения и включение новых направлений и стилей таких как электронная музыка или экспериментальные жанры , а также развитие онлайн-образования и удаленных курсов для студентов из разных городов и стран . Кроме того, школа барабанов может сотрудничать с другими музыкальными школами и организациями для обмена опытом и методами .
Школа барабанов предлагает профессиональные уроки игры на барабанах, открывая возможность для всех желающих освоить эту увлекательную инструментальную дисциплину.
с помощью современных методик обучения . Целью такой школы является развитие музыкальных способностей и повышение общего культурного уровня студентов путем участия в различных музыкальных проектах и концертах. Школа барабанов также предоставляет возможность студентам общаться с другими музыкантами и учиться у них в формате семинаров и мастер-классов .
Школа барабанов может быть интересна как начинающим музыкантам, так и профессионалам которые хотят улучшить свои навыки игры на барабанах . Программа обучения в школе барабанов обычно включает в себя теоретические занятия по музыкальной теории и истории, а также практические занятия по игре на барабанах в группах или индивидуально . Кроме того, школа барабанов часто организует различные мероприятия и концерты в которых участвуют студенты и преподаватели школы .
Обучение в школе барабанов может принести студентам многочисленные преимущества такие как приобретение новых навыков и знаний в области музыки . Одним из главных преимуществ является возможность получения профессионального музыкального образования в формате индивидуальных или групповых занятий. Кроме того, обучение в школе барабанов может помочь студентам повысить свою уверенность в себе и развить творческие способности путем общения с другими музыкантами и учениками.
Обучение в школе барабанов также предоставляет возможность студентам получить практический опыт и развить свои навыки игры на барабанах в формате практических занятий и тренировок . Школа барабанов может быть интересна как детям, так и взрослым которые ищут возможность для творческого самовыражения . Преподаватели школы барабанов обычно имеют большой опыт работы и могут помочь студентам в освоении различных техник и стилей игры на барабанах .
Программа обучения в школе барабанов обычно включает в себя комплекс теоретических и практических занятий по технике и методике игры на барабанах . Теоретические занятия могут включать в себя изучение музыкальной теории, истории музыки и различных стилей и направлений с использованием современных учебных пособий и технологий . Практические занятия могут включать в сбя обучение различным техникам игры на барабанах под руководством преподавателей с большим опытом работы.
Программа обучения в школе барабанов может варьироваться в зависимости от уровня подготовки и интересов студентов для студентов со средним или высоким уровнем подготовки . Школа барабанов может предлагать различные направления обучения по народной и эстрадной музыке, а также ??? форматы обучения онлайн- или офлайн-курсы . Кроме того, школа барабанов часто организует различные мероприяти и концерты с приглашением известных музыкантов и групп .
В заключении можно сказать, что школа барабанов представляет собой уникальную и интересную возможность для музыкального образования и творческого самовыражения для музыкантов, ищущих новые подходы и методы . Программа обучения в школе барабанов может включать в себя теоретические и практические занятия по технике и методике игры на барабанах , а также различные мероприятия и концерты с учстием студентов и преподавателей школы .
Перспективы развития школы барабанов могут включать в себя расширение программы обучения и включение новых направлений и стилей таких как классическая музыка или джаз , а также развитие онлайн-образования и удаленных курсов в формате видео-уроков или интерактивных занятий. Кроме того, школа барабанов может сотрудничать с другими музыкальными школами и организациями для организации совместных проектов и концертов .
рулонные шторы на электроприводе рулонные шторы на электроприводе .
жалюзи для пластиковых окон с электроприводом https://prokarniz23.ru .
Улучшайте свои навыки и повышайте квалификацию с помощью продвижение сайта обучение и станьте профессионалами в области поисковой оптимизации!
помочь участникам овладеть навыками поисковой оптимизации . Эти курсы обычно включают в себя теоретические основы SEO, включая понимание работы поисковых алгоритмов . В результате прохождения таких курсов, участники смогут получить практические навыки поисковой оптимизации и продвижения сайтов .
Участники SEO курсов могут изучить вопросы внутренней и внешней оптимизации сайтов . Это может включать в себя изучение методов создания ссылок и их влияния на рейтинг сайта . После завершения курса, участники могут использовать приобретенные навыки для работы в digital-агентствах .
В рамках SEO курсов, учащиеся могут освоить искусство внутренней и внешней оптимизации сайтов, включая работу с ссылками и другими факторами. Это может включать в себя работу над индивидуальными проектами, направленными на оптимизацию реальных сайтов. Благодаря такому подходу, учащиеся могут развить навыки, необходимые для того, чтобы стать профессионалом в области поисковой оптимизации.
Практические занятия в SEO курсах могут предполагать участие в групповых проектах, где участники смогут применить полученные знания на практике. Это дает участникам возможность получить реальный опыт работы в SEO, который можно применить на практике . После завершения курса, участники могут применять полученные знания и навыки для оптимизации своих собственных сайтов или для работы в качестве SEO-специалистов .
Теоретические основы SEO включают в себя изучение методов создания качественного контента и его роли в поисковой оптимизации . Эти знания необходимы для освоения методов анализа и улучшения позиций сайта в поисковых системах. Теоретические основы могут включать в себя анализ факторов, влияющих на рейтинг сайта, включая технические, контентные и внешние факторы .
Изучение теоретических основ SEO может помочь участникам понять, как работают поисковые системы и как оптимизировать сайты для лучшей видимости . Это может включать в себя анализ влияния технологий на поисковую оптимизацию иDigital маркетинг . Благодаря такому подходу, участники могут овладеть всеми аспектами SEO, от технической оптимизации до создания контента .
SEO курсы могут помочь участникам овладеть навыками поисковой оптимизации и продвижения сайтов . Это может включать в себя анализ случаев успешной оптимизации сайтов и изучение их стратегий . Участники могут освоить искусство внутренней и внешней оптимизации сайтов, включая работу с ссылками и другими факторами.
Применение SEO в реальной практике может предполагать участие в групповых проектах, где участники смогут применить полученные знания на практике. Это дает участникам возможность развить свои навыки дальше, изучая более специализированные темы в области SEO и digital маркетинга. После завершения курса, участники могут применять полученные знания и навыки для оптимизации своих собственных сайтов или для работы в качестве SEO-специалистов .
Улучшайте свои навыки и повышайте квалификацию с помощью курсы сео специалиста и станьте профессионалами в области поисковой оптимизации!
предоставить знания о том, как повышать рейтинг сайта в результатах поиска. Эти курсы обычно включают в себя лекции по созданию качественного контента и его продвижению. В результате прохождения таких курсов, участники смогут получить практические навыки поисковой оптимизации и продвижения сайтов .
Участники SEO курсов могут ознакомиться с инструментами анализа сайтов и их оптимизации. Это может включать в себя освоение техник поискового маркетинга и создания рекламных кампаний. После завершения курса, участники могут использовать приобретенные навыки для работы в digital-агентствах .
В рамках SEO курсов, учащиеся могут изучить, как создавать и продвигать качественный контент, который будет привлекать целевую аудиторию . Это может включать в себя участие в практических занятиях, где учащиеся смогут применить полученные знания на практике . Благодаря такому подходу, учащиеся могут понять, как измерять эффективность SEO кампаний и корректировать их .
Практические занятия в SEO курсах могут быть направлены на изучение инструментов анализа сайтов и их оптимизации . Это дает участникам возможность развить свои навыки дальше, изучая более специализированные темы в области SEO и digital маркетинга. После завершения курса, участники могут использовать приобретенные знания для создания эффективныхdigital-стратегий .
Теоретические основы SEO включают в себя освоение техник анализа и улучшения позиций сайта в поисковых системах. Эти знания необходимы для понимания того, как создавать эффективные кампании в интернете . Теоретические основы могут включать в себя освоение методов оптимизации сайтов для различных поисковых систем.
Изучение теоретических основ SEO может предоставить знания о том, как создавать эффективные кампании в интернете. Это может включать в себя анализ влияния технологий на поисковую оптимизацию иDigital маркетинг . Благодаря такому подходу, участники могут понять, как измерять эффективность SEO кампаний и корректировать их .
SEO курсы могут предоставить знания о том, как создавать эффективные кампании в интернете. Это может включать в себя участие в практических занятиях, где участники смогут применить полученные знания на практике . Участники могут приобрести практический опыт в оптимизации сайтов, включая работу с ключевыми словами и метатегами .
Применение SEO в реальной практике может быть направлено на изучение инструментов анализа сайтов и их оптимизации . Это дает участникам возможность освоить навыки, необходимые для успешной карьеры в digital-агентствах . После завершения курса, участники могут развивать свои навыки дальше, изучая новые тенденции и технологии в области SEO.
eu9 sg offers unique opportunities for gambling and entertainment in the heart of the online casino.
With round-the-clock support, the eu9 casino provides assistance whenever it is needed.
Мы предлагаем широкий выбор купить бытовку в москве для различных нужд и бюджета.
Бытовки представляют собой универсальным решением для размещения временных помещений. Они могут быть использованы в самых разных сферах. Часто их используют на строительных площадках, в качестве офисов или складов. Кроме того, бытовки удобны для организации отдыхов рабочих.
Одним из главных преимуществ является их мобильность. Быстро можно перемещать с одного места на другое. Это позволяет устанавливать их в нужных местах в зависимости от потребностей. Также они легко устанавливаются и не требует специальных знаний.
Еще одно достоинство бытовок — это их affordability. Сравнительно с капитальными зданиями , стоимость бытовок намного ниже. В результате бытовки становятся их доступными для широкого круга пользователей. Большинство фирм и частных лиц выбирают именно бытовки, чтобы избежать высоких затрат.
Тем не менее, следует учитывать и несколько недостатков этих конструкций. Хоть они и удобными, они не всегда могут обеспечить достаточный комфорт. В холодное время года они могут быть плохо утеплены, что создает определенные неудобства. Кроме того, в зависимости от качества материалов может различаться, что напрямую влияет на долговечность. В итоге, при выборе бытовки стоит обратить внимание на производителя и материалы.
Если вы ищете качественный экран для видеопроектора купить, то обязательно посетите наш сайт, чтобы найти лучшие варианты для своих потребностей.
является ключевым компонентом в системе проекции. Он дает возможность получить изображение высокого разрешения. Кроме того, экран для проектора может быть установлен в конференц-залах.
Экран для проектора предназначен для отражения света . Он должен иметь специальное покрытие . Экран для проектора подходит для использования с различными моделями проекторов .
Экраны для проекторов могут быть разделены на несколько групп. Они могут иметь различные размеры . Например, экраны для проекторов могут быть сделаны из ткани .
Экраны для проекторов должны быть выбраны в зависимости от конкретных потребностей . Они должны быть настроены с учетом характеристик проектора . Экраны для проекторов могут быть использованы в различных условиях .
Экраны для проекторов должны давать возможность получить изображение высокого разрешения. Они должны быть изготовлены из высококачественных материалов . Например, экраны для проекторов должны иметь высокий уровень контрастности .
Экраны для проекторов должны быть выбраны в зависимости от конкретных потребностей . Они должны быть настроены с учетом характеристик проектора . Экраны для проекторов могут быть использованы в различных условиях .
Экраны для проекторов должны быть установлены в соответствии с инструкциями производителя . Они должны быть закреплены на стене или потолке . Например, экраны для проекторов должны быть протестированы на наличие помех.
Экраны для проекторов должны быть регулярно обслуживаемы . Они должны быть обновлены при появлении новых технологий . Экраны для проекторов могут быть переданы другим пользователям .
Для создания современных и функциональных кухонь многие дизайнеры и домовладельцы выбирают акриловые столешницы для кухни цена, которые отличаются своей прочностью, элегантностью и легкостью в уходе.
являются одним из самых популярных choix для кухонь и ванных комнат . Они обладают рядом преимуществ, таких как устойчивость к пятнам и царапинам . Кроме того, столешницы из акрилового камня могут быть изготовлены в широком диапазоне цветов и стилей .
Столешницы из акрилового камня часто выбираются за их эстетическую привлекательность и практичность . Они могут быть использованы для создания различных дизайнов, от минималистичного до роскошного . Кроме того, столешницы из акрилового камня легко чистятся и поддерживаются в чистоте.
Столешницы из акрилового камня отличаются повышенной стойкостью к износу и нагреву. Они позволяют создавать бесшовные поверхности, что снижает риск появления бактерий и загрязнений . Кроме того, столешницы из акрилового камня могут быть реставрированы при необходимости.
Столешницы из акрилового камня имеют разнообразную цветовую гамму и различные текстурные решения, что позволяет создавать уникальные интерьеры . Они являются экологически чистым материалом, поскольку могут быть изготовлены из переработанных материалов . Кроме того, столешницы из акрилового камня подходят для использования в качестве материала для создания различных деталей интерьера.
Установка столешниц из акрилового камня требует профессионального подхода и специального оборудования . Они должны быть установлены квалифицированными специалистами, чтобы обеспечить правильную эксплуатацию и долговечность . Кроме того, столешницы из акрилового камня требуют регулярного ухода, чтобы сохранить их внешний вид и свойства .
Столешницы из акрилового камня могут быть чистятся с использованием специальных чистящих средств и микрофибровой ткани . Они не должны быть очищены абразивными средствами или щетками, чтобы избежать царапин . Кроме того, столешницы из акрилового камня должны быть защищены от воздействия высоких температур и прямого солнечного света .
Столешницы из акрилового камня являются перспективным материалом для отделки кухонь и ванных комнат . Они обладают рядом преимуществ, включая прочность, долговечность и эстетическую привлекательность . Кроме того, столешницы из акрилового камня доступны в большом выборе оттенков и текстур, что позволяет создавать уникальные интерьеры.
Столешницы из акрилового камня будут оставаться высоко востребованным материалом для создания современных и функциональных интерьеров . Они подходят для использования в качестве материала для создания различных деталей интерьера, от столешниц до подоконников. Кроме того, столешницы из акрилового камня будут постоянно улучшаться и модернизироваться, чтобы соответствовать последним тенденциям и достижениям в области материаловедения .
multi hop routing hyperliquid Provides efficient transaction routing, allowing users to find the best trading conditions.
When considering hyperliquid systems, multi hop routing takes on new significance.
Мы предлагаем широкий выбор бытовка цены для различных нужд и бюджета.
Бытовки — это универсальным решением для размещения временных помещений. Они могут быть использованы в самых разных сферах. Часто их используют на строительных площадках, в качестве офисов или складов. Бытовки могут быть полезны для организации отдыхов рабочих.
Преимущества бытовок является их мобильность. Их можно легко перемещать с одного места на другое. Это позволяет устанавливать их в нужных местах в зависимости от потребностей. Также они легко устанавливаются и не требует специальных знаний.
Еще одно достоинство бытовок — это их affordability. В отличие от стационарных сооружений , стоимость бытовок намного ниже. Это делает их доступными для широкого круга пользователей. Большинство фирм и частных лиц выбирают именно бытовки, чтобы избежать высоких затрат.
Тем не менее, следует учитывать и несколько недостатков этих конструкций. Несмотря на то, что бытовки это удобными, они не всегда могут обеспечить достаточный комфорт. В холодное время года они могут быть плохо утеплены, что создает определенные неудобства. Качество же материалов может различаться, что напрямую влияет на долговечность. В итоге, при выборе бытовки стоит обратить внимание на производителя и материалы.
hyperliquid swap fees comparison Provides efficient transaction routing, allowing users to find the best trading conditions.
It becomes especially important in situations where direct connections are impractical because of physical obstacles.
Для создания современных и функциональных кухонь многие дизайнеры и домовладельцы выбирают акриловая столешница для кухни, которые отличаются своей прочностью, элегантностью и легкостью в уходе.
пользуются большим спросом для?? кухонь и санузлов. Они имеют ряд достоинств, включая устойчивость к загрязнениям и механическим повреждениям. Кроме того, столешницы из акрилового камня доступны в большом выборе оттенков и текстур.
Столешницы из акрилового камня выбираются дизайнерами и домовладельцами за их красоту и надежность. Они могут быть применены для реализации различных стилей, от современного до классического . Кроме того, столешницы из акрилового камня просты в уходе и обслуживании .
Столешницы из акрилового камня имеют несколько достоинств, включая устойчивость к механическим повреждениям и химическим веществам . Они обеспечивают возможность изготовления сплошных поверхностей, что уменьшает вероятность попадания влаги и микроорганизмов . Кроме того, столешницы из акрилового камня могут быть реставрированы при необходимости.
Столешницы из акрилового камня имеют разнообразную цветовую гамму и различные текстурные решения, что позволяет создавать уникальные интерьеры . Они являются экологически чистым материалом, поскольку могут быть изготовлены из переработанных материалов . Кроме того, столешницы из акрилового камня могут быть применены для изготовления различных изделий, включая столешницы, столы и полки .
Установка столешниц из акрилового камня нуждается в квалифицированном подходе и оснащении. Они должны быть установлены профессионалами, чтобы обеспечить качество и гарантию. Кроме того, столешницы из акрилового камня должны быть периодически очищены и обработаны, чтобы сохранить их внешний вид и свойства.
Столешницы из акрилового камня могут быть очищены при помощи мягких чистящих средств и обычной ткани. Они не должны быть очищены абразивными средствами или щетками, чтобы избежать царапин . Кроме того, столешницы из акрилового камня должны быть защищены от воздействия экстремальных температур и ультрафиолетового излучения .
Столешницы из акрилового камня являются перспективным материалом для отделки кухонь и ванных комнат . Они имеют ряд достоинств, включая устойчивость к механическим повреждениям, химическим веществам и воздействию влаги . Кроме того, столешницы из акрилового камня доступны в большом выборе оттенков и текстур, что позволяет создавать уникальные интерьеры.
Столешницы из акрилового камня будут продолжать быть популярным выбором для потребителей и дизайнеров . Они подходят для использования в качестве материала для создания различных деталей интерьера, от столешниц до подоконников. Кроме того, столешницы из акрилового камня будут постоянно улучшаться и модернизироваться, чтобы соответствовать последним тенденциям и достижениям в области материаловедения .
Find the perfect stamp making solution with our free online stamp maker!
More and more people are turning to online platforms for creating rubber stamps. With just a few clicks, you can design and order a custom stamp from the comfort of your home.
A lot of online stamp makers provide step-by-step tutorials for ease of use. Begin with selecting your desired stamp type, ranging from self-inking to classic options.
Then, you can personalize your stamp by adding your own text and images. Many platforms offer a variety of fonts and clipart to choose from, allowing for endless creativity.
Finally, once your design is complete, you simply place your order. Your custom rubber stamp will be crafted and shipped to your doorstep in no time.
Find the perfect stamp making solution with our [url=https://stampwebshop-1.com/]stamp maker[/url]!
The rise of online rubber stamp makers has transformed the industry. You can easily create a unique stamp tailored to your needs online.
Many websites offer intuitive interfaces that guide you through the design. Begin with selecting your desired stamp type, ranging from self-inking to classic options.
Then, you can personalize your stamp by adding your own text and images. Most sites provide an array of font selections and graphic options to enhance your design.
Finally, once your design is complete, you simply place your order. Your custom rubber stamp will be crafted and shipped to your doorstep in no time.
melbet sport [url=www.v-bux.ru]www.v-bux.ru[/url] .
Планируя заказать переезд квартиры недорого, вы можете значительно упростить этот процесс, воспользовавшись услугами профессионалов.
Не забывайте использовать надежные коробки и упаковочные материалы
Планируя организация квартирного переезда, вы можете значительно упростить этот процесс, воспользовавшись услугами профессионалов.
Организация всего процесса может стать настоящим испытанием
курсовая заказать недорого http://www.kupit-kursovuyu-4.ru .
kurica 2 kurica2.ru .
курсовая работа недорого http://kupit-kursovuyu-1.ru/ .
Доброго времени всем! Организую поездку в Калининград и хочу узнать о погодой и купальным сезоном. Кто знает, какая температура моря в Калининграде летом и реально ли купаться в Балтийском море в августе? Также интересно, когда стартует сезон в Калининграде и какова нормальная температура зимой, чтобы оценить, стоит ли ехать в морозное время. Буду очень благодарен за пожелания и рекомендации по локациям, например, стоит ли побывать в Форт 11 или на Янтарный пляж.
Если кто-то строил маршрут по Калининграду, укажите, куда лучше сходить вечером и какие привлекательные улицы стоит однозначно увидеть. Интересуют и замки Калининградской области, и музеи, особенно Музей янтаря (вот, кстати, нужная инфа достопримечательности правдинска ). Кроме того, для времяпрепровождения с детьми в Светлогорске какие объекты и кафе советуете? Обязательно желаю посетить органный зал в Кафедральном соборе — кто-нибудь бывал на выступлениях?
купить курсовую сайт kupit-kursovuyu-6.ru .
Наше маркетинговое агентство предлагает индивидуальные решения для роста вашего бизнеса.
Сравните расценки и предложения разных агентств, чтобы сделать правильный выбор.
aviator x https://aviator-game-winner.com/ .
В случае если вы составляете поездку в Калининград и планируете познать неповторимой природой и архитектурой, непременно посетите уединенные пляжи Калининградской области, а также погрузитесь с историей острова Канта и его выступлениями органистов. Для блужданий по городу великолепно сгодятся пешие маршруты по Калининграду, где вы сможете рассмотреть самые изящные улицы и архитектуру центральной части города. Также стоит заглянуть в калининградский зоопарк — уточните часы работы и тариф билетов на официальном сайте калининград море можно ли купаться .
Для любителей моря важно знать, что купальный период в Калининграде как правило приходится на июль и август, когда тепло воды в Балтийском море делается относительно теплой для купания. Если вас интересует думаете о том, когда выгоднее направиться в Калининград или как добраться из Калининграда в Зеленоградск на электропоезде или до Куршской косы, в сети удастся отыскать исчерпывающие маршруты и график движения. А в вечернее время удастся оценить чудесными видами со смотровых точек и оценить лучшие завтраки в любом из кафе города.
aviator game aviator game .
plane crash game online earn money https://www.aviator-game-deposit.com .
aviator money http://www.aviator-game-winner.com .
рейтинг компаний по ремонту квартир rejting-kompanij-po-remontu-kvartir-moskvy.com .
Услуги технический перевод онлайн предоставляются высококвалифицированными переводчиками.
особую область переводческих услуг, ориентированную на техническую документацию . Это важнейшим компонентом в развитии международной кооперации . Благодаря техническому переводу компаниям и организациям удается расширять свои рынки и аудиторию .
Технический перевод требует не только знания языка, но и глубокого понимания технической терминологии . Переводчики должны уметь точно передавать техническую информацию на иностранном языке . Это гарантирует качество и точность перевода .
Процесс технического перевода включает в себя несколько этапов, от первоначальной оценки проекта до финального контроля качества . На первом этапе оцениваются ресурсы, необходимые для выполнения задачи . Далее производится выбор наиболее подходящих инструментов и технологий для перевода .
Выполнение самого перевода требует высокой концентрации и внимания к деталям . После завершения перевода выполняется проверка соответствия переведенного текста оригиналу . Этот позволяет минимизировать ошибки и несоответствия .
Технический перевод помогает преодолевать языковые барьеры и расширять доступ к информации . Благодаря техническому переводу можно обеспечить доступ к передовым технологиям и инновациям . Это позволяет строить международные партнерства и сотрудничество .
Технический перевод также способствует распространению знаний и культуры . Это помогает в построении более гармоничного и взаимосвязанного мира . Поэтому необходимо постоянно совершенствовать методы и инструменты перевода .
Будущее технического перевода тесно связано с развитием технологий и искусственного интеллекта . Развитие машинного перевода и искусственного интеллекта поможет в обработке больших объемов информации .
В будущем технический перевод станет еще более важным для глобальных?? и международного сотрудничества . Это позволит расширить спектр услуг и предложений на рынке . Поэтому необходимо постоянно развивать новые навыки и знания .
udane wala jahaj aviator-game-deposit.com .
фирмы по ремонту квартиры https://rejting-kompanij-po-remontu-kvartir-moskvy.com/ .
Услуги технический перевод на английский предоставляются высококвалифицированными переводчиками.
сложный процесс, включающий в себя перевод технических текстов и документов . Это необходимая часть международного сотрудничества в области науки, технологий и производства . Благодаря техническому переводу компаниям и организациям удается расширять свои рынки и аудиторию .
Технический перевод предполагает высокий уровень специализации и точности . Переводчики должны уметь точно передавать техническую информацию на иностранном языке . Это позволяет обеспечить максимальную эффективность коммуникации .
Процесс технического перевода требует тщательного планирования и выполнения . На первом этапе проводится анализ исходного текста и определение требований к переводу . Далее разрабатывается план реализации проекта .
Выполнение самого перевода включает в себя несколько итераций проверки и редактирования . После завершения перевода производится финальная коррекция и подготовка текста к публикации . Этот позволяет минимизировать ошибки и несоответствия .
Технический перевод играет ключевую роль в развитии международной кооперации в области науки и техники . Благодаря техническому переводу компании могут экспортировать свою продукцию и услуги в другие страны . Это позволяет строить международные партнерства и сотрудничество .
Технический перевод также помогает в понимании и решении глобальных проблем . Это помогает в построении более гармоничного и взаимосвязанного мира . Поэтому необходимо постоянно совершенствовать методы и инструменты перевода .
Будущее технического перевода предполагает интеграцию с другими областями, такими как локализация и культурная адаптация . Развитие машинного перевода и искусственного интеллекта поможет в обработке больших объемов информации .
В будущем технический перевод станет еще более важным для глобальных?? и международного сотрудничества . Это будет способствовать развитию новых форматов и технологий для перевода и коммуникации . Поэтому необходимо постоянно развивать новые навыки и знания .
рольшторы заказать http://www.avtomaticheskie-rulonnye-shtory11.ru .
????? ??? http://aviator-game-deposit.com/ .
профессиональный ремонт квартир в москве профессиональный ремонт квартир в москве .
рулонные шторы с электроприводом рулонные шторы с электроприводом .
рулонные шторы автоматические рулонные шторы автоматические .
metatrader 5 http://www.metatrader-5-downloads.com/ .
metatrader 5 metatrader 5 .
Для решения всех задач, связанных с переводом документов на любой язык, можно обратиться в юридический перевод, где опытные переводчики окажут профессиональные услуги по переводу любых документов.
перевод текстов и документов с высоким уровнем точности . Это позволяет им удовлетворять различные потребности клиентов, от перевода личных документов до комплексных бизнес-проектов. Кроме того, бюро переводов часто обладает d?iной переводчиков, которые являются экспертами в разных областях, владеющими специализированными знаниями для точных переводов. Это гарантирует, что переведенный текст не только соответствует оригиналу по смыслу, но и адаптирован к целевой аудитории и соответствует требованиям определенной отрасли.
Бюро переводов также уделяет особое внимание конфиденциальности и безопасности переводимой информации, поскольку это может включать защиту данных с помощью современных технологий . Это является ключевым аспектом их услуг, поскольку клиенты часто доверяют им?ливую информацию. Помимо этого, бюро переводов может предложить услуги по локализации, которые включают адаптацию контента к конкретному региону или рынку . Это особенно ценно для компаний, стремящихся расширить свою деятельность на новые рынки.
Работа с бюро переводов дает клиентам возможность получить высококачественные переводы в короткие сроки . Это означает, что клиенты могут получить переводы, соответствующие их потребностям, будь то срочный перевод небольшого документа или масштабный проект, требующий перевода большого объема текстов. Кроме того, многие бюро переводов используют специализированное программное обеспечение для обеспечения качества переводов. Это не только ускоряет процесс перевода, но и гарантирует, что окончательный продукт соответствует самым высоким стандартам.
Партнерство с бюро переводов также может быть ключом к успешной коммуникации с клиентами, говорящими на разных языках . Благодаря точным и культурно адаптированным переводам, бизнес может укреплять доверие и авторитет среди своих международных партнеров и клиентов. Это делает бюро переводов не просто поставщиком услуг, а ценным партнером в достижении бизнес-целей.
Бюро переводов обычно работает используя комбинацию человеческого опыта и технологий для обеспечения точности . Для начала работы клиент заказывает услугу перевода, предоставляя необходимую информацию о проекте . После этого, бюро переводов использует специализированное программное обеспечение для управления процессом перевода . Этот подход??ет, что перевод не только выполнен качественно, но и соответствует конкретным потребностям и ожиданиям клиента.
На протяжении всего процесса бюро переводов также отслеживает качество и точность перевода . Это может включать проверку перевода на наличие ошибок и несоответствий . Такой подход к?? и удовлетворенности клиента позволяет бюро переводов поддерживать высокий уровеньprofessionalизма и строить долгосрочные отношения с клиентами.
В заключение, бюро переводов представляет собой мощный инструмент для бизнеса и частных лиц, стремящихся преодолеть языковой барьер. С их помощью клиенты могут получить возможность расширить свои горизонты и построить отношения на международном уровне. Бюро переводов является не просто поставщиком услуг, а стратегическим партнером, который может помочь усилить коммуникацию . Сегодня, когдамир становится все более взаимосвязанным, роль бюро переводов будет только увеличиваться в значимости .
Для решения всех задач, связанных с переводом документов на любой язык, можно обратиться в нотариальное бюро переводов, где опытные переводчики окажут профессиональные услуги по переводу любых документов.
перевод текстов и документов с высоким уровнем точности . Это позволяет им удовлетворять различные потребности клиентов, от перевода личных документов до комплексных бизнес-проектов. Кроме того, бюро переводов часто обладает d?iной переводчиков, которые являются экспертами в разных областях, понимающими нюансы языка и культурные особенности . Это гарантирует, что переведенный текст не только соответствует оригиналу по смыслу, но и адаптирован к целевой аудитории и соответствует требованиям определенной отрасли.
Бюро переводов также уделяет особое внимание конфиденциальности и безопасности переводимой информации, обеспечивая, что все переводчики обязаны сохранять конфиденциальность. Это является ключевым аспектом их услуг, поскольку клиенты часто доверяют им?ливую информацию. Помимо этого, бюро переводов может предложить услуги по локализации, учитывая культурные и языковые особенности . Это особенно ценно для компаний, стремящихся расширить свою деятельность на новые рынки.
Работа с бюро переводов дает клиентам доступ к команде опытных и квалифицированных переводчиков . Это означает, что клиенты могут получить переводы, соответствующие их потребностям, будь то срочный перевод небольшого документа или масштабный проект, требующий перевода большого объема текстов. Кроме того, многие бюро переводов используют современные технологии для управления процессом перевода . Это не только ускоряет процесс перевода, но и гарантирует, что окончательный продукт соответствует самым высоким стандартам.
Партнерство с бюро переводов также может быть способом для компаний построить сильный бренд на международном уровне. Благодаря точным и культурно адаптированным переводам, бизнес может эффективно передавать свое послание целевой аудитории . Это делает бюро переводов не просто поставщиком услуг, а ценным партнером в достижении бизнес-целей.
Бюро переводов обычно работает гарантируя, что все переводы соответствуют самым высоким стандартам. Для начала работы клиент получает оценку стоимости и сроков выполнения проекта. После этого, бюро переводов использует специализированное программное обеспечение для управления процессом перевода . Этот подход??ет, что перевод не только выполнен качественно, но и соответствует конкретным потребностям и ожиданиям клиента.
На протяжении всего процесса бюро переводов также обеспечивает, что окончательный продукт соответствует ожиданиям клиента. Это может включать проверку перевода на наличие ошибок и несоответствий . Такой подход к?? и удовлетворенности клиента позволяет бюро переводов поддерживать высокий уровеньprofessionalизма и строить долгосрочные отношения с клиентами.
В заключение, бюро переводов представляет собой мощный инструмент для бизнеса и частных лиц, стремящихся преодолеть языковой барьер. С их помощью клиенты могут получить высококачественные переводы, соответствующие их потребностям . Бюро переводов является не просто поставщиком услуг, а стратегическим партнером, который может помочь усилить коммуникацию . Сегодня, когдамир становится все более взаимосвязанным, роль бюро переводов будет только оставаться ключевым фактором в международном общении.
Купить шины Пирелли обеспечит вам отличное сцепление с дорогой в любую погоду.
Шины марки Pirelli пользуются высоким спросом на рынке. Эти шины известны своей прочностью и долговечностью. Каждая шина создается с учетом последних технологий.
Одним из преимуществ шин Pirelli является отличная сцепка с дорогой. При использовании данных шин заметно увеличивается безопасность. Pirelli также активно работает над экологичными решениями.
Покупка шин Pirelli — это правильный выбор для любого автомобилиста. Важным аспектом является цена, которая соответствует качеству. Следите за акциями и распродажами, чтобы сэкономить деньги.
Для уверенной езды выбирайте шины от Pirelli. Обслуживание шин – это залог их долговечности. Выбирая шины Pirelli, вы выбираете комфорт и надежность.
mt5 download for pc metatrader-5-downloads.com .
forex metatrader 5 https://metatrader-5-mac.com .
metatrader5 download http://metatrader-5-downloads.com/ .
metatrader 5 mac download http://metatrader-5-mac.com .
промокод семяныч поможет вам сэкономить на покупках в компании!
Ассортимент товаров в Семяныче достаточно широк, и скидки распространяются на многие позиции.
mt5 http://www.metatrader-5-downloads.com/ .
рольшторы на окна купить в москве avtomaticheskie-rulonnye-shtory11.ru .
metatrader 5 download mac https://metatrader-5-mac.com .
Особенности входа на официальный сайт Несмотря на запрет работу физических и интернет азартных казино
и регулярную блокировку официальной платформы, вход в Чемпион клуб не представляет особой
сложности. Есть зеркала, повторяющие структуру и функционал онлайн лицензионного портала.
Ресурсы, обладая общей
базой данных, позволяют игрокам действовать разными способами,
так как действия не только
синхронизированы, но и защищены от
любых недобросовестных вмешательств. Champion имеет хорошую репутацию азартного клуба, гарантирующую честность и высокую скорость выплат,
безопасность денежных транзакций и конфиденциальных
данных, так как информация шифруется специальным
кодом. Это оценивается всеми пользователи по достоинству, что и определяет огромное количество положительных отзывов.
Детализированный обзор заведения, его возможностей, частоты крупных выигрышей, разнообразию бонусной программы и техподдержки,
которая оказывается круглосуточно и на
русском языке доказывает,
что Чемпион это клуб, который придет по
вкусу всем: неискушенным осторожным новичкам, и матерым гемблерам,
имеющим свою систему игры, нацеленную на
получение крупного выигрыша.
Feel free to surf to my website: wiki.novaverseonline.com
промокод семяныч поможет вам сэкономить на покупках в компании!
Для активации промокода достаточно указать его в специальном поле.
metatrader5 http://metatrader-5-downloads.com .
автоматические шторы на окна автоматические шторы на окна .
download mt5 for mac http://www.metatrader-5-mac.com/ .
автоматические рулонные шторы на окна автоматические рулонные шторы на окна .
meta trader 5 download http://metatrader-5-downloads.com .
mt5 mt5 .
I only play on Sundays too, it’s basically a religion now
puzzle online
промокод семяныч поможет вам сэкономить на покупках в компании!
Промокод Семяныч — это отличный способ сэкономить на покупках.
независимая экспертиза при затоплении независимая экспертиза при затоплении .
купить филлеры оптом купить филлеры оптом .
заказать курсовой проект заказать курсовой проект .
Водитель знает все объездные пути,
ни разу не стояли в пробке
https://medakapedia.com/index.php/User:DeannaBoykin1
заказать качественную курсовую заказать качественную курсовую .
После родов убрали диастаз
и сделали аккуратный пупок,
швов почти не видно
https://www.ge.infn.it/wiki//gpu/index.php?title=User:MatthiasShellshe
сколько стоит сделать курсовую работу на заказ kupit-kursovuyu-8.ru .
помощь курсовые http://kupit-kursovuyu-9.ru .
А если купить долю в недполучить внж в испанииижимости, считается?
Химчистка обивки кресел: кожа как новая,
без царапин. Экологичная химия,
запаха ноль.
https://merkelistan.com/index.php?title=Benutzer:SandraFeeney9
сколько стоит сделать курсовую работу на заказ kupit-kursovuyu-9.ru .
куплю курсовую работу куплю курсовую работу .
Этот сайт посвящен современной программе для видеонаблюдения, предлагающей передовые аналитические инструменты. Представленное программное обеспечение для IP камер включает в себя VMS, позволяющую эффективно управлять записью с камер видеонаблюдения. Особое внимание уделено функциям распознавания лиц и распознавания номеров автомобилей, которые значительно расширяют возможности системы видеонаблюдения. Пользователи могут настраивать интеллектуальные уведомления и получать оповещения при обнаружении определенных событий. Благодаря встроенной аналитике, предлагаемое решение превращает обычную систему мониторинга в мощный инструмент для обеспечения безопасности и повышения эффективности бизнес-процессов. Платформа упрощает управление большим количеством камер и предоставляет удобный интерфейс для анализа собранных данных. облачная система видеонаблюдения
Программа видеонаблюдения обеспечивает безопасность, сочетая технологии и простоту использования. На сайте доступно руководство по выбору и настройке систем, включая облачные решения и их особенности. Обсуждаются гибридные модели, совмещающие облачное и локальное хранение, повышающие гибкость системы. Описаны передовые аналитические функции, такие как детекция движения и распознавание объектов на основе AI. Представлены обзоры и рейтинги лучших программ, упрощающие выбор подходящего решения. Специалисты найбалансировать разрешение и объем хранилища данных. Необходимо также обратить внимание на возможности системы по архивации и восстановлению данных.** программное обеспечение для видеонаблюдения
карнизы для штор купить в москве http://prokarniz36.ru/ .
Компания предлагает услуги аренда авто с водителем в новосибирске для путешественников и местных жителей.
В Новосибирске аренда авто с водителем является одним из наиболее комфортных способов передвижения по городу. Это связано с тем, что в городе есть множество компаний, предлагающих такие услуги. Аренда авто с водителем позволяет гостям Новосибирска наслаждаться городом без забот о передвижении. Это особенно удобно для иностранных туристов, которые могут не владеть русским языком. Компании, предлагающие аренду авто с водителем в Новосибирске, гарантируют высокое качество обслуживания. Для этого необходимо указать дату, время и место подачи автомобиля. Водители, предоставляемые компаниями аренды авто, являются опытными и вежливыми. Это позволяет добраться до места назначения быстро и безопасно.
Аренда авто с водителем в Новосибирске имеет множество преимуществ, таких как экономия времени и средств. Это особенно удобно для деловых путешественников, которые часто имеют плотный график. Услуги аренды авто с водителем в Новосибирске также включают в себя помощь в решении любых вопросов, связанных с пребыванием в городе. Это дает возможность оценить красоту города и его окрестностей.
Услуги аренды авто с водителем в Новосибирске доступны для всех категорий граждан. Это позволяет добраться до места назначения быстро и комфортно. Водители, предоставляемые компаниями аренды авто, являются опытными и знающими город. Для этого необходимо указать дату, время и место подачи автомобиля.
Аренда автомобиля с водителем может быть арендована на любой период времени, от нескольких часов до нескольких дней. Это дает возможность оценить красоту города и его окрестностей. Аренда авто с водителем в Новосибирске предлагает широкий спектр услуг для тех, кто ценит комфорт и удобство.
Аренда авто с водителем может быть оформлена онлайн или по телефону. Для этого необходимо указать дату, время и место подачи автомобиля. Водители, предоставляемые компаниями аренды авто, являются опытными и знающими город. Это позволяет добраться до места назначения быстро и безопасно.
В Новосибирске можно арендовать автомобиль с водителем для поездки на знаменитые достопримечательности. Это дает возможность оценить красоту города и его окрестностей. Водители, предоставляемые компаниями аренды авто, являются опытными и вежливыми. Это позволяет гостям Новосибирска наслаждаться городом без забот о передвижении.
Аренда авто с водителем в Новосибирске также позволяет экономить средства, поскольку не нужно тратить деньги на бензин, парковку и другие расходы. Для этого необходимо указать дату, время и место подачи автомобиля. Услуги аренды авто с водителем в Новосибирске представлены различными компаниями, которые предлагают широкий выбор автомобилей. Это дает возможность оценить красоту города и его окрестностей.
Услуги аренды авто с водителем в Новосибирске представлены различными компаниями, которые предлагают широкий выбор автомобилей. Это дает возможность оценить красоту города и его окрестностей. Услуги аренды авто с водителем в Новосибирске становятся все более доступными и популярными среди путешественников. Это позволяет гостям Новосибирска наслаждаться городом без забот о передвижении.
Услуги аренды авто с водителем в Новосибирске доступны для всех категорий граждан. Это дает возможность оценить красоту города и его окрестностей. Водители, предоставляемые компаниями аренды авто, являются опытными и знающими город. Это позволяет добраться до места назначения быстро и безопасно.
оценка ущерба залив по вине управляющей компании http://www.ekspertiza-zaliva-kvartiry-5.ru/ .
филлеры для косметологии купить https://filler-kupit.ru/ .
Компания предлагает услуги аренда автомобиля с водителем новосибирск для путешественников и местных жителей.
Аренда автомобиля с водителем в Новосибирске становится все более популярной среди туристов и бизнесменов. Это связано с тем, что в городе есть множество компаний, предлагающих такие услуги. Аренда авто с водителем позволяет гостям Новосибирска наслаждаться городом без забот о передвижении. Это особенно удобно для иностранных туристов, которые могут не владеть русским языком. Аренда авто с водителем в Новосибирске может быть оформлена онлайн или по телефону. Для этого необходимо указать дату, время и место подачи автомобиля. Услуги аренды авто с водителем в Новосибирске становятся все более доступными и популярными среди путешественников. Это позволяет добраться до места назначения быстро и безопасно.
Водитель, предоставляемый компанией аренды авто, занимается всеми вопросами, связанными с передвижением по городу. Это особенно удобно для деловых путешественников, которые часто имеют плотный график. Услуги аренды авто с водителем в Новосибирске также включают в себя помощь в решении любых вопросов, связанных с пребыванием в городе. Это дает возможность оценить красоту города и его окрестностей.
Услуги аренды авто с водителем в Новосибирске доступны для всех категорий граждан. Это позволяет добраться до места назначения быстро и комфортно. Водители, предоставляемые компаниями аренды авто, являются опытными и знающими город. Для этого необходимо указать дату, время и место подачи автомобиля.
Услуги аренды авто с водителем в Новосибирске представлены различными компаниями, которые предлагают широкий выбор автомобилей. Это дает возможность оценить красоту города и его окрестностей. Водители, предоставляемые компаниями аренды авто, являются опытными и вежливыми.
В Новосибирске можно арендовать автомобиль с водителем для поездки на деловую встречу или на свадьбу. Для этого необходимо указать дату, время и место подачи автомобиля. Водители, предоставляемые компаниями аренды авто, являются опытными и знающими город. Это позволяет добраться до места назначения быстро и безопасно.
Аренда автомобиля с водителем может быть арендована на любой период времени, от нескольких часов до нескольких дней. Это дает возможность оценить красоту города и его окрестностей. Водители, предоставляемые компаниями аренды авто, являются опытными и вежливыми. Это позволяет гостям Новосибирска наслаждаться городом без забот о передвижении.
Услуги аренды авто с водителем в Новосибирске доступны для всех желающих, независимо от их бюджета. Для этого необходимо указать дату, время и место подачи автомобиля. Услуги аренды авто с водителем в Новосибирске представлены различными компаниями, которые предлагают широкий выбор автомобилей. Это дает возможность оценить красоту города и его окрестностей.
В Новосибирске можно арендовать автомобиль с водителем для поездки на деловую встречу или на свадьбу. Это дает возможность оценить красоту города и его окрестностей. Водители, предоставляемые компаниями аренды авто, являются опытными и вежливыми. Это позволяет гостям Новосибирска наслаждаться городом без забот о передвижении.
Аренда автомобиля с водителем может быть арендована на любой период времени, от нескольких часов до нескольких дней. Это дает возможность оценить красоту города и его окрестностей. Аренда авто с водителем в Новосибирске позволяет экономить средства, поскольку не нужно тратить деньги на бензин, парковку и другие расходы. Это позволяет добраться до места назначения быстро и безопасно.
Для тех, кто ищет качественное медицинский перевод онлайн, наши услуги станут лучшим выбором.
Медицинские переводы играют ключевую роль в обеспечении коммуникации между медицинскими специалистами и пациентами . Бюро медицинских переводов занимается переводом различных медицинских документов, включая истории болезни, медицинские статьи и инструкции к лекарствам. Бюро медицинских переводов имеет большой опыт работы с медицинскими учреждениями.
Бюро медицинских переводов также занимается локализацией медицинского программного обеспечения и веб-сайтов, что включает в себя адаптацию интерфейса и содержания для разных языков и культур. Локализация медицинских веб-сайтов включает в себя перевод текста и адаптацию графики .
Бюро медицинских переводов предлагает различные виды медицинских переводов, включая перевод инструкций к лекарствам и медицинскому оборудованию. Перевод медицинских статей и публикаций требует высокого уровня экспертизы в области медицины и знания медицинской терминологии. Перевод медицинских публикаций требует глубокого понимания медицинских исследований .
Бюро медицинских переводов также занимается переводом медицинских документов, таких как истории болезни и медицинские справки. Перевод медицинских документов требует высокой точности и качества .
Бюро медицинских переводов предоставляет многочисленные преимущества для медицинских учреждений и пациентов, включая доступ к медицинской информации на разных языках . Бюро медицинских переводов также обеспечивает конфиденциальность и безопасность медицинских документов, что является важным аспектом в сфере здравоохранения. Бюро медицинских переводов обеспечивает безопасность медицинских переводов.
Бюро медицинских переводов также может помочь медицинским учреждениям и пациентам сэкономить время и ресурсы, предоставляя быстрые и качественные медицинские переводы. Бюро медицинских переводов использует передовые технологии для обеспечения скорости и качества переводов .
В заключении, бюро медицинских переводов является важным звеном в сфере здравоохранения, где перевод медицинских текстов требует высокой точности и качества . Бюро медицинских переводов предлагает различные виды медицинских переводов, включая перевод медицинских статей, историй болезни и инструкций к лекарствам. Бюро медицинских переводов использует передовые технологии для обеспечения точности и качества переводов .
Бюро медицинских переводов также обеспечивает конфиденциальность и безопасность медицинских документов, что является важным аспектом в сфере здравоохранения. Бюро медицинских переводов использует передовые технологии для обеспечения конфиденциальности .
Для тех, кто ищет качественное бюро переводов личных и медицинских документов, наши услуги станут лучшим выбором.
Медицинские переводы играют ключевую роль в обеспечении коммуникации между медицинскими специалистами и пациентами . Бюро медицинских переводов занимается переводом различных медицинских документов, включая истории болезни, медицинские статьи и инструкции к лекарствам. Бюро медицинских переводов работает с высококвалифицированными переводчиками .
Бюро медицинских переводов также занимается локализацией медицинского программного обеспечения и веб-сайтов, что включает в себя адаптацию интерфейса и содержания для разных языков и культур. Локализация медицинского программного обеспечения и веб-сайтов обеспечивает доступ к медицинским услугам для более широкой аудитории.
Бюро медицинских переводов предлагает различные виды медицинских переводов, включая перевод инструкций к лекарствам и медицинскому оборудованию. Перевод медицинских статей и публикаций требует высокого уровня экспертизы в области медицины и знания медицинской терминологии. Перевод медицинских публикаций требует глубокого понимания медицинских исследований .
Бюро медицинских переводов также занимается переводом медицинских документов, таких как истории болезни и медицинские справки. Перевод медицинских справок включает в себя перевод медицинской терминологии .
Бюро медицинских переводов предоставляет многочисленные преимущества для медицинских учреждений и пациентов, включая доступ к медицинской информации на разных языках . Бюро медицинских переводов также обеспечивает конфиденциальность и безопасность медицинских документов, что является важным аспектом в сфере здравоохранения. Бюро медицинских переводов использует передовые технологии для обеспечения конфиденциальности .
Бюро медицинских переводов также может помочь медицинским учреждениям и пациентам сэкономить время и ресурсы, предоставляя быстрые и качественные медицинские переводы. Бюро медицинских переводов использует передовые технологии для обеспечения скорости и качества переводов .
В заключении, бюро медицинских переводов является важным звеном в сфере здравоохранения, где медицинские переводы играют ключевую роль в обеспечении коммуникации между медицинскими специалистами и пациентами . Бюро медицинских переводов предлагает различные виды медицинских переводов, включая перевод медицинских статей, историй болезни и инструкций к лекарствам. Бюро медицинских переводов имеет большой опыт работы с медицинскими учреждениями и пациентами.
Бюро медицинских переводов также обеспечивает конфиденциальность и безопасность медицинских документов, что является важным аспектом в сфере здравоохранения. Бюро медицинских переводов использует передовые технологии для обеспечения конфиденциальности .
карнизы для штор купить в москве http://www.prokarniz36.ru .
независимый эксперт по оценке ущерба залив http://www.ekspertiza-zaliva-kvartiry-5.ru .
интернет магазин филлеров интернет магазин филлеров .
Получить апостиль диплома — это важный шаг для подтверждения подлинности вашего образования за границей.
Необходимо также учесть, что для апостилирования могут потребоваться определенные документы.
карниз электроприводом штор купить http://prokarniz36.ru .
установление причины залива установление причины залива .
филлеры купить цены https://filler-kupit.ru/ .
Мне кажется, что главное — это подтверждение квалификации.
Если у тебя нет диплома.
испания диджитал номад
Металлические двери премиум класса обеспечивают надежную защиту и элегантный стиль вашего дома.
Они оснащены передовыми замковыми системами и защитными функциями, значительно уменьшающими вероятность кражи.
Чтобы обеспечить легализацию вашего образования за границей, важно знать, где и как поставить апостиль на диплом.
На завершающем этапе вам придется получить сам апостиль от уполномоченного органа.
Для оформления кухни в уникальном стиле можно мойка каменная для кухни купить, что придаст интерьеру неповторимый шарм и практичность.
Раковина для кухни должна быть не только функциональной, но и эстетически привлекательной . Кроме того, необходимо учитывать количество пользователей и общий дизайн кухонного пространства При выборе раковины для кухни важно учитывать индивидуальные потребности каждого члена семьи. При покупке раковины также рекомендуется прочитать отзывы и сравнить цены в разных магазинах Сравнение цен позволит вам сэкономить деньги и выбрать лучший вариант.
Кроме того, при выборе раковины для кухни необходимо учитывать ее размер и форму Правильный размер и форма раковины могут сделать ее более функциональной и удобной. Материал, из которого изготовлена раковина, также играет важную роль Это может быть нержавеющая сталь, керамика или гранит, каждый из которых имеет свои преимущества и недостатки . Установка раковины может быть простой или сложной, в зависимости от типа раковины и вашего уровня опыта Правильная установка раковины гарантирует, что она будет работать эффективно и прослужит долго.
Существует множество типов раковин для кухни, каждый из которых имеет свои собственные характеристики и преимущества Гранитовые раковины известны своим элегантным внешним видом и высокой устойчивостью к царапинам . Нержавеющая сталь является одним из наиболее популярных материалов для раковин Она не только прочная и устойчивая к царапинам, но и легкая в уходе . Гранитовые раковины предлагают высокую устойчивость к нагреву и царапинам Они идеально подходят для кухонь с традиционным или классическим дизайном.
Кроме того, существуют раковины из искусственного камня, которые предлагают высокую прочность и элегантность Они могут быть изготовлены из различных материалов, включая кварц и акрил . Раковина из керамики может добавить кухне больше стиля и изысканности Керамические раковины могут быть очень дорогими, но они обеспечивают уникальный и премиальный вид . Выбор правильного типа раковины для кухни может быть сложным, но учитывая ваши потребности и предпочтения, вы можете найти идеальный вариант Это может включать рассмотрение размера, формы и материала раковины .
Установка раковины для кухни может быть простой или сложной, в зависимости от типа раковины и вашего уровня опыта Для некоторых типов раковин может потребоваться помощь профессионала . Для начала необходимо измерить пространство, где будет установлена раковина Правильные измерения гарантируют, что раковина будет установлена правильно и не будет никаких проблем. После установки раковины необходимо провести Regularный уход, чтобы сохранить ее внешний вид и функциональность Регулярный уход также включает проверку раковины на наличие повреждений или царапин .
Кроме того, стоит учитывать стиль и дизайн кухни при выборе раковины Также стоит учитывать стиль кухонных приборов и мебели . При установке раковины также необходимо учитывать сантехнику и электрические соединения Также стоит учитывать наличие необходимых инструментов и материалов . Выбор правильной раковины для кухни может сделать ее более функциональной и красивой Правильный выбор раковины может сделать вашу кухню более гармоничной и привлекательной.
При выборе раковины для кухни стоит учитывать множество факторов, включая размер, материал и стиль Раковина для кухни должна быть не только функциональной, но и эстетически привлекательной . Также важно учитывать индивидуальные потребности и предпочтения При выборе раковины для кухни важно учитывать индивидуальные потребности каждого члена семьи. При покупке раковины также рекомендуется прочитать отзывы и сравнить цены в разных магазинах Сравнение цен позволит вам сэкономить деньги и выбрать лучший вариант.
Кроме того, стоит учитывать стиль и дизайн кухни при выборе раковины Также стоит учитывать стиль кухонных приборов и мебели . Выбор правильной раковины для кухни может быть сложным, но учитывая ваши потребности и предпочтения, вы можете найти идеальный вариант Также стоит учитывать стиль и дизайн кухни . При установке раковины также необходимо учитывать сантехнику и электрические соединения Это может включать подключение раковины к водопроводной и канализационной системе .
Металлические двери премиум класса обеспечивают надежную защиту и элегантный стиль вашего дома.
Эти двери оборудованы современными замками и системами защиты, что минимизирует риск взлома.
Чтобы обеспечить легализацию вашего образования за границей, важно знать, где и как поставить апостиль диплома через госуслуги.
Чтобы получить апостиль, нужно обратиться в учебное заведение, выдавшее диплом.
Для оформления кухни в уникальном стиле можно мойка из искусственного камня купить цена, что придаст интерьеру неповторимый шарм и практичность.
Раковина для кухни является одним из ключевых элементов кухонного интерьера, требующим тщательного выбора . Кроме того, необходимо учитывать количество пользователей и общий дизайн кухонного пространства При выборе раковины для кухни важно учитывать индивидуальные потребности каждого члена семьи. При покупке раковины также рекомендуется прочитать отзывы и сравнить цены в разных магазинах Сравнение цен позволит вам сэкономить деньги и выбрать лучший вариант.
Кроме того, при выборе раковины для кухни необходимо учитывать ее размер и форму Правильный размер и форма раковины могут сделать ее более функциональной и удобной. Материал, из которого изготовлена раковина, также играет важную роль Нержавеющая сталь известна своей прочностью и легкостью в уходе . Установка раковины может быть простой или сложной, в зависимости от типа раковины и вашего уровня опыта Правильная установка раковины гарантирует, что она будет работать эффективно и прослужит долго.
Существует множество типов раковин для кухни, каждый из которых имеет свои собственные характеристики и преимущества Керамические раковины могут добавить кухне больше стиля и изысканности. Нержавеющая сталь является одним из наиболее популярных материалов для раковин Она не только прочная и устойчивая к царапинам, но и легкая в уходе . Гранитовые раковины предлагают высокую устойчивость к нагреву и царапинам Они идеально подходят для кухонь с традиционным или классическим дизайном.
Кроме того, существуют раковины из искусственного камня, которые предлагают высокую прочность и элегантность Искусственный камень легок в уходе и устойчив к царапинам и нагреву . Раковина из керамики может добавить кухне больше стиля и изысканности Она известна своей высокой устойчивостью к нагреву и царапинам, а также легкостью в уходе . Выбор правильного типа раковины для кухни может быть сложным, но учитывая ваши потребности и предпочтения, вы можете найти идеальный вариант Также стоит учитывать стиль и дизайн кухни .
Установка раковины для кухни может быть простой или сложной, в зависимости от типа раковины и вашего уровня опыта Правильная установка раковины гарантирует, что она будет работать эффективно и прослужит долго. Для начала необходимо измерить пространство, где будет установлена раковина Правильные измерения гарантируют, что раковина будет установлена правильно и не будет никаких проблем. После установки раковины необходимо провести Regularный уход, чтобы сохранить ее внешний вид и функциональность Это может включать мытье ее мягким мылом и теплой водой, а также avoidance использования абразивных чистящих средств .
Кроме того, стоит учитывать стиль и дизайн кухни при выборе раковины Правильный выбор раковины может сделать кухню более гармоничной и красивой. При установке раковины также необходимо учитывать сантехнику и электрические соединения Правильная установка раковины гарантирует, что она будет работать эффективно и безопасно. Выбор правильной раковины для кухни может сделать ее более функциональной и красивой Правильный выбор раковины может сделать вашу кухню более гармоничной и привлекательной.
При выборе раковины для кухни стоит учитывать множество факторов, включая размер, материал и стиль Раковина для кухни должна быть не только функциональной, но и эстетически привлекательной . Также важно учитывать индивидуальные потребности и предпочтения Для большой семьи может потребоваться раковина большего размера, чтобы обеспечить tho?i maiное использование . При покупке раковины также рекомендуется прочитать отзывы и сравнить цены в разных магазинах Сравнение цен позволит вам сэкономить деньги и выбрать лучший вариант.
Кроме того, стоит учитывать стиль и дизайн кухни при выборе раковины Также стоит учитывать стиль кухонных приборов и мебели . Выбор правильной раковины для кухни может быть сложным, но учитывая ваши потребности и предпочтения, вы можете найти идеальный вариант Это может включать рассмотрение размера, формы и материала раковины . При установке раковины также необходимо учитывать сантехнику и электрические соединения Правильная установка раковины гарантирует, что она будет работать эффективно и безопасно.
Запеченный ролл с креветками и ананасом — необычное, но очень вкусное
сочетание
Суши северок
аренда самолета предлагает удобные и быстрые решения для тех, кто заинтересован в аренде бизнес джета.
К тому же, вы избегаете длинных очередей в аэропортах.
Клиника проктологии https://proctofor.ru в Москве с современным оборудованием и опытными врачами. Проводим деликатную диагностику и лечение геморроя, трещин, полипов, воспалительных заболеваний прямой кишки. Приём по записи, без очередей, в комфортных условиях. Бережный подход, щадящие методы, анонимность и тактичное отношение.
карниз для штор электрический http://provorota.su/ .
электрокарнизы в москве elektrokarniz2.ru .
электрокарниз недорого http://elektrokarniz98.ru/ .
Should you be exploring your style through seasonal color analysis, tools like Color Analysis Pro or numerous free online quizzes can be a wonderful start to understanding your personal palette. For example, if you’re inquisitive whether you belong to the deep summer color season, learning about the deep summer palette—known for its crisp, muted, and soft hues—can definitely help in choosing clothing and makeup that enhance your natural features.
If you want a more accurate assessment, AI color analysis apps offer personalized insights by scanning your skin tone, including widely-used options for yellow skin tone colors to wear or even specialized palettes like soft autumn and light summer. For those unsure how to cancel Color Analysis Pro or navigate its features, instructions and community tips are regularly shared on forums and legitimate sites seasonal color analysis . This way, you can investigate seasonal colors, hair color trends for 2026, and even virtual hair color try-ons without difficulty.
электрокарниз двухрядный цена http://elektrokarniz2.ru .
электрокарнизы для штор http://provorota.su .
автоматический карниз для штор elektrokarniz98.ru .
Профессиональный нарколог на дому поможет вам с прокапаться на дому быстро и удобно, обеспечив комфорт и безопасность в вашем доме.
Применение народных методов может ускорить процесс восстановления.
Для тех, кто ценит безопасность и эксклюзивный дизайн, входные двери премиум класса для квартиры становятся идеальным выбором, поскольку они сочетают в себе прочность, стиль и надежность.
являются одним из наиболее популярных и востребованных видов дверей на рынке современных строительных материалов . Эти двери разработаны для обеспечения максимальной защиты от взлома и проникновения . Металлические двери премиум класса могут быть выполнены в различных стилях и дизайнах, что позволяет им гармонично вписаться в любой интерьер.
Металлические двери премиум класса соответствуют всем современным стандартам качества и безопасности. Эти двери предназначены для обеспечения максимального комфорта и безопасности для жителей или сотрудников . Металлические двери премиум класса сочетают функциональность, безопасность и эстетическую привлекательность.
Металлические двери премиум класса могут быть оснащены различными системами защиты, включая противовзломные устройства. Эти двери могут быть выполнены в различных цветах и стилях, что позволяет им гармонично вписаться в любой интерьер . Металлические двери премиум класса могут быть оснащены системами видеонаблюдения и другими средствами безопасности .
Металлические двери премиум класса отличаются высокой долговечностью и прочностью . Эти двери могут быть оснащены дополнительными опциями, такими как звукоизоляция и термоизоляция . Металлические двери премиум класса представляют собой универсальное решение для различных задач .
Процесс установки металлических дверей премиум класса должен быть проведен квалифицированными специалистами . Эти двери должны быть проверены на прочность и долговечность. Металлические двери премиум класса должны быть эксплуатируемы в соответствии с инструкциями производителя и требованиями безопасности .
Эксплуатация металлических дверей премиум класса должна быть проведена в соответствии с инструкциями производителя и требованиями безопасности . Металлические двери премиум класса должны быть соответствовать всем современным стандартам качества и безопасности . Эти двери сочетают функциональность, безопасность и эстетическую привлекательность.
Металлические двери премиум класса сочетают в себе повышенную безопасность, эстетическую привлекательность и долговечность. При выборе металлических дверей премиум класса должны быть приняты во внимание все требования и стандарты качества. Металлические двери премиум класса должны быть оснащены всеми необходимыми системами безопасности и защиты .
Металлические двери премиум класса могут быть использованы в различных типах зданий, от частных домов до офисных помещений. Эти двери должны быть эксплуатируемы в соответствии с инструкциями производителя и требованиями безопасности . Металлические двери премиум класса могут быть использованы как для входа в здание, так и для разделения внутренних помещений .
Профессиональный нарколог на дому поможет вам с нарколог на дом вывод из запоя быстро и удобно, обеспечив комфорт и безопасность в вашем доме.
Если человек теряет сознание или испытывает сильные галлюцинации, это сигнал к действию.
Looking for a reliable way to travel in comfort? Check out our how much to hire a private jet!
Private jet charter is a luxurious option for travelers seeking comfort. It allows individuals to bypass commercial flights. Many people prefer this method for its exclusivity.
The process of booking a private jet is quite simple. Customers typically choose their departure point and set their preferred travel dates. After that, a professional service will assist in finding the ideal aircraft.
Traveling by private jet has several perks. One significant advantage is the convenience of using regional airports. This feature often minimizes overall journey duration.
Additionally, the level of privacy provided is unmatched. Passengers can conduct business meetings without the fear of being overheard. This makes private jet charter an ideal solution for business travelers.
Для тех, кто ценит безопасность и эксклюзивный дизайн, входные двери премиум класса для квартиры становятся идеальным выбором, поскольку они сочетают в себе прочность, стиль и надежность.
сочетают в себе повышенную безопасность, эстетическую привлекательность и долговечность. Эти двери отличаются своей универсальностью и могут быть установлены в различных типах зданий, от частных домов до офисных помещений. Металлические двери премиум класса подвергаются строгому контролю качества на всех этапах производства .
Металлические двери премиум класса отличаются повышенной прочностью и долговечностью . Эти двери предназначены для обеспечения максимального комфорта и безопасности для жителей или сотрудников . Металлические двери премиум класса могут быть использованы как для входа в здание, так и для разделения внутренних помещений .
Металлические двери премиум класса имеют современный и стильный дизайн . Эти двери производятся с использованием высококачественных материалов, что обеспечивает их долговечность и устойчивость к различным воздействиям . Металлические двери премиум класса имеют современный и привлекательный внешний вид.
Металлические двери премиум класса могут быть использованы в различных типах зданий, от частных домов до офисных помещений . Эти двери предназначены для обеспечения максимального комфорта и безопасности для жителей или сотрудников . Металлические двери премиум класса могут быть использованы как для входа в здание, так и для разделения внутренних помещений .
Процесс установки металлических дверей премиум класса должен быть проведен квалифицированными специалистами . Эти двери должны быть установлены в соответствии с инструкциями производителя и требованиями безопасности . Металлические двери премиум класса должны быть эксплуатируемы в соответствии с инструкциями производителя и требованиями безопасности .
Эксплуатация металлических дверей премиум класса требует регулярного обслуживания и проверки . Металлические двери премиум класса должны быть оснащены всеми необходимыми документами и сертификатами . Эти двери сочетают функциональность, безопасность и эстетическую привлекательность.
Металлические двери премиум класса сочетают в себе повышенную безопасность, эстетическую привлекательность и долговечность. При выборе металлических дверей премиум класса должны быть учтены все необходимые факторы, такие как качество материалов, уровень безопасности и эстетическая привлекательность . Металлические двери премиум класса должны быть оснащены всеми необходимыми системами безопасности и защиты .
Металлические двери премиум класса представляют собой универсальное решение для различных задач . Эти двери должны быть регулярно проверены и обслужены . Металлические двери премиум класса имеют привлекательный внешний вид и могут стать настоящим украшением любого здания .
Looking for a reliable way to travel in comfort? Check out our private jet hire cost!
Private jet charter is a convenient service for travelers seeking efficiency. It allows individuals to bypass commercial flights. Many people prefer this method for its exclusivity.
The process of booking a private jet is quite simple. Customers typically choose their departure point and provide the travel timeline. After that, a specialized agent will assist in offering tailored solutions.
There are many benefits to using private jets. One significant advantage is the convenience of using regional airports. This feature often allows for quicker arrivals.
The privacy afforded by these flights is exceptional. Passengers can conduct business meetings without worrying about security breaches. This makes private jet charter an perfect choice for business travelers.
электрокарнизы для штор https://www.elektrokarniz2.ru .
карниз с электроприводом https://provorota.su/ .
прокарниз https://elektrokarniz98.ru .
рулонные шторы с электроприводом на пластиковые окна http://www.rulonnye-shtory-s-elektroprivodom.ru .
рулонные жалюзи москва рулонные жалюзи москва .
Выбор материала для стеллажей в гараже — актуально!
Металл прочнее, но дерево
теплее на вид. Для инструментов что посоветуете, чтобы не прогибалось?
Feel free to visit my homepage … https://kotelinaya.ru/
бамбуковые электрожалюзи prokarniz23.ru .
Если планируете поездку в Калининград, определенно загляните в Рыбную деревню Калининграда — это крайне атмосферных мест старого города с замечательными ресторанами и фото на память. Кроме того, не пропустите кафедральный собор Святых Петра и Павла с его известным органом — органные концерты здесь крайне впечатляют. Для тех, кто занимается природой, стоит узнать, можно ли купаться в Балтийском море в Калининграде — ответ меняется от сезона и температуры воды, но летом купание достаточно реально.
Если собираетесь больше узнать о достопримечательностях района, рекомендуется ознакомиться с гидами по Калининграду и ближайшим местам, таким как Кнайпхоф и Куршская коса. Еще удобно пользоваться электричкой Калининград — Зеленоградск, которая связывает город с побережьем. Более подробно и с актуальными советами можно ознакомиться здесь: янтарный пляж . Климатические условия в Калининграде зимой и летом очень разнится, поэтому предпочтительнее планировать поездку, принимая к сведению климатические особенности региона.
рулонные шторы на пластиковые окна с электроприводом рулонные шторы на пластиковые окна с электроприводом .
рулонные шторы на окна купить рулонные шторы на окна купить .
умные шторы с алисой http://www.prokarniz27.ru/ .
автоматические жалюзи автоматические жалюзи .
При работе с медицинскими документами очень важно иметь качественный перевод на латинский медицинский переводчик, чтобы гарантировать точность и соответствие международным стандартам.
особую область перевода, требующую высокой точности и специальных знаний . Это необходимо для того, чтобы обеспечить правильное понимание медицинской информации . В медицинском переводе высоко квалифицированные переводчики работают с сложными текстами .
Медицинский перевод включает в себя разработку инструкций для медицинского оборудования и препаратов. Всё это требует глубокого понимания медицинской терминологии и современных методов лечения . Для того, чтобы гарантировать точность и актуальность переводимой информации, медицинские переводчики постоянно совершенствуют свои навыки .
Медицинский перевод можно разделить на разные виды, включая перевод медицинских текстов, устный перевод и адаптацию программного обеспечения. Это включает в себя создание инструкций для пациентов и медицинского персонала . При выполнении таких задач уметь работать с различными форматами и программным обеспечением .
Одним из наиболее важных типов медицинского перевода является перевод документов , поскольку он включает в себя перевод историй болезни, диагнозов и рецептов . Другой важный аспект — создание учебных материалов для медицинских учебных заведений. Это требует глубокого понимания культурных особенностей и нюансов.
Точность в медицинском переводе является вопросом жизни и смерти . Медицинские переводчики должны быть абсолютно точными в своих переводах . Переводчики должны уметь работать с различными форматами и типами документов.
Ошибки в переводе медицинских текстов могут иметь катастрофические последствия . Для того, чтобы минимизировать риск ошибок , медицинские переводчики используют специализированное программное обеспечение для проверки и редактирования. Это включает в себя участие в профессиональных тренингах и семинарах .
Использование технологий в медицинском переводе существенно ускоряет процесс перевода . Это включает в себя разработку специализированных инструментов для медицинского перевода. Однако, основная задача остается за квалифицированными переводчиками и редакторами.
Технологии обеспечивают доступ к обширным базам знаний и информации. Но, человеческий фактор обеспечивает нюансированность и точность . Для того, чтобы оставаться конкурентоспособными на рынке, медицинские переводчики должны быть в курсе последних технологических достижений .
Компания предлагает широкий выбор премиальные двери, изготовленные с учетом индивидуальных пожеланий каждого клиента и соответствующие высоким стандартам качества и безопасности.
отличаются своим высоким уровнем безопасности и эстетики. Они изготавливаются из лучших материалов . Металлические двери премиум класса рекомендуются экспертами в области строительства и дизайна .
Металлические двери премиум класса могут быть изготовлены в соответствии с индивидуальными заказами . Они предназначены для долгого срока службы . Металлические двери премиум класса являются инвестицией в будущее .
Металлические двери премиум класса отличаются своей высокопрочной конструкцией . Они имеют прочную и надежную конструкцию . Металлические двери премиум класса требуют минимального технического обслуживания .
Металлические двери премиум класса оснащены современными системами защиты . Они оснащены функцией автоматического открывания и закрывания. Металлические двери премиум класса являются идеальным решением для бизнеса и дома .
Металлические двери премиум класса предлагают высокий уровень безопасности и защиты . Они имеют отличную теплоизоляцию и звукоизоляцию . Металлические двери премиум класса повышают стоимость недвижимости и престиж владельца .
Металлические двери премиум класса отличаются своей простотой и удобством эксплуатации . Они могут быть изготовлены в соответствии с индивидуальными заказами и дизайном . Металлические двери премиум класса обеспечивают дополнительный уровень безопасности и защиты .
Металлические двери премиум класса предназначены для длительной эксплуатации и требует минимального ухода . Они производятся с использованием высококачественных материалов и технологий . Металлические двери премиум класса являются долгосрочной инвестицией в будущее.
Металлические двери премиум класса могут быть изготовлены в соответствии с индивидуальными заказами и дизайном. Они обеспечивают круглосуточную охрану и безопасность. Металлические двери премиум класса повышают статус и престиж владельца.
Компания предлагает широкий выбор входные двери премиум класса, изготовленные с учетом индивидуальных пожеланий каждого клиента и соответствующие высоким стандартам качества и безопасности.
отличаются своим высоким уровнем безопасности и эстетики. Они проектируются с учетом всех необходимых стандартов. Металлические двери премиум класса являются идеальным решением для тех, кто ищет надежную защиту от внешних факторов.
Металлические двери премиум класса оснащены современными системами безопасности. Они требуют минимального ухода и обслуживания . Металлические двери премиум класса повышают стоимость недвижимости .
Металлические двери премиум класса отличаются своей высокопрочной конструкцией . Они производятся с использованием высококачественных материалов . Металлические двери премиум класса предназначены для длительной эксплуатации .
Металлические двери премиум класса обеспечивают круглосуточную охрану и безопасность. Они могут быть интегрированы с другими системами безопасности . Металлические двери премиум класса повышают статус и престиж владельца.
Металлические двери премиум класса имеют современный и стильный дизайн . Они пропускают минимальное количество шума и холода . Металлические двери премиум класса являются долгосрочной инвестицией в будущее .
Металлические двери премиум класса имеют долгий срок службы и сохраняют свои функциональные свойства. Они оснащены современными системами безопасности и защиты. Металлические двери премиум класса являются идеальным решением для тех, кто ценит качество и комфорт .
Металлические двери премиум класса оснащены современными системами безопасности и защиты. Они производятся с использованием высококачественных материалов и технологий . Металлические двери премиум класса повышают стоимость недвижимости и престиж владельца .
Металлические двери премиум класса имеют долгий срок службы и сохраняют свои функциональные свойства . Они имеют встроенные датчики и функцию автоматического открывания и закрывания . Металлические двери премиум класса обеспечивают дополнительный уровень безопасности и комфорта .
При работе с медицинскими документами очень важно иметь качественный бюро медицинских переводов, чтобы гарантировать точность и соответствие международным стандартам.
особую область перевода, требующую высокой точности и специальных знаний . Это необходимо для того, чтобы гарантировать точность перевода медицинских текстов . В медицинском переводе переводчики должны обладать глубокими знаниями медицинской терминологии .
Медицинский перевод включает в себя разработку инструкций для медицинского оборудования и препаратов. Всё это требует точности и внимания к деталям, поскольку ошибки могут иметь серьёзные последствия. Для того, чтобы выполнить требования заказчиков , медицинские переводчики используют специализированное программное обеспечение и инструменты.
Медицинский перевод можно разделить на разные виды, включая перевод медицинских текстов, устный перевод и адаптацию программного обеспечения. Это включает в себя перевод медицинских статей и исследований . При выполнении таких задач уметь работать с различными форматами и программным обеспечением .
Одним из наиболее важных типов медицинского перевода является перевод документов , поскольку он предполагает работу с конфиденциальной информацией . Другой важный аспект — устный перевод, который используется во время консультаций и операций . Это требует специальных навыков и знаний в области медицины .
Точность в медицинском переводе является вопросом жизни и смерти . Медицинские переводчики должны быть абсолютно точными в своих переводах . Переводчики должны уметь работать с различными форматами и типами документов.
Ошибки в переводе медицинских текстов могут иметь катастрофические последствия . Для того, чтобы обеспечить высочайшее качество услуг, медицинские переводчики используют специализированное программное обеспечение для проверки и редактирования. Это включает в себя использование глоссариев и баз данных .
Использование технологий в медицинском переводе дает возможность работать с большими объемами информации. Это включает в себя использованиепрограммного обеспечения для автоматизированного перевода . Однако, технологии не могут полностью заменить человеческий интеллект и опыт .
Технологии обеспечивают доступ к обширным базам знаний и информации. Но, человеческий фактор обеспечивает нюансированность и точность . Для того, чтобы оставаться конкурентоспособными на рынке, медицинские переводчики должны быть в курсе последних технологических достижений .
рольшторы с электроприводом рольшторы с электроприводом .
рулонные жалюзи с электроприводом рулонные жалюзи с электроприводом .
кожаные жалюзи с электроприводом http://prokarniz23.ru/ .
Решили купить живую елку, выбрали эту компанию. Все рекомендации сотрудников оказались полезными. Никакой волокиты, всё бысто. Привезли здоровую, пышную елку. Опыт был настолько хорош, что рекомендую всем – http://gazeta.ekafe.ru/viewtopic.php?f=26&t=45346
Видна работа настоящих профессионалов Елка идеального качества, как и обещали Хорошее впечатление о компании Лучший выбор в этом году https://soligorsk-info.ucoz.com/forum/8-129-1
гидроизоляция подвала изнутри цена м2 гидроизоляция подвала изнутри цена м2 .
обмазочная гидроизоляция цена работы за м2 gidroizolyacziya-czena1.ru .
инъекционная гидроизоляция инъекционная гидроизоляция .
Электрокарниз — это идеальное решение для современного интерьера, которое можно найти по ссылке электрокарниз с таймером прокарниз.
Они подходят практически для всех типов окон, включая панорамные и арочные.
Управляемые шторы позволяют effortlessly контролировать освещение в вашем доме. купить умные шторы Прокарниз — это идеальное сочетание стиля и функциональности.
Необычное сочетание практичности и красоты делает управляемые шторы особенно востребованными.
Установите купить жалюзи с электроприводом прокарниз, и наслаждайтесь комфортом и простотой управления светом в вашем доме.
С каждым днем автоматические жалюзи с электрическим управлением завоевывают сердца покупателей. Эти инновационные устройства предлагают комфорт и удобство.
Первостепенное преимущество – это возможность управления уровнем света в помещении. Управление жалюзи осуществляется через дистанционный пульт, что делает использование более комфортным.
Во-вторых, автоматические жалюзи способны улучшить энергосбережение. Их рациональное использование помогает сохранять оптимальную температуру в помещении.
Подводя итог, можно сказать, что автоматические жалюзи с электроприводом – это отличный выбор для современных интерьеров. Установка таких жалюзи улучшает функциональность и внешний вид вашего помещения.
Удобно и стильно: рулонные шторы с электроприродом заказать прокарниз для вашего дома!
Популярность рулонных штор с электроприводом растет среди современных дизайнеров. Эти шторы не только удобны, но и функциональны, что делает их отличным решением для любого интерьера.
Главное достоинство рулонных штор с электроприводом – это возможность управления с помощью пульта. Такая система управления делает использование штор невероятно удобным и простым.
Широкий ассортимент моделей и тканей рулонных штор с электроприводом позволяет выбрать подходящий вариант для любого интерьера. Таким образом, можно легко найти идеальное решение как для традиционного, так и для современного дизайна.
Вы можете заказать рулонные шторы с электроприводом как в магазинах, так и онлайн. Обратите внимание на уровень качества и репутацию производителя при заказе, чтобы не ошибиться с выбором.
Удобство и стиль в интерьере обеспечит электрокарнизы для штор цена москва Прокарниз, который легко управляется с пульта.
Электрокарниз — это современное решение для автоматизации управления шторами и занавесками.
Для тех, кто ищет качественный и надежный услуги клининга в спб, существует множество вариантов выбора среди клининговых компаний, предлагающих широкий спектр услуг по уборке и содержанию территорий.
Клининг в Санкт-Петербурге является одной из наиболее востребованных услуг среди жителей и бизнеса города . Это связано с постоянным стремлением к чистоте и порядку в доме или офисе. Многие жители Санкт-Петербурга и владельцы бизнеса обращаются к профессиональным клининг-сервисам за помощью в поддержании чистоты и порядка .
Профессиональные клининг-сервисы в СПб также предоставляют услуги по организации и систематизации пространства.
В Санкт-Петербурге предлагается широкий спектр клининг-услуг, включая генеральные уборки, мытье окон и чистку ковров . Компании, предоставляющие услуги клининга, работают в тесном сотрудничестве с клиентами, чтобы удовлетворить все их потребности.
Это гарантирует лучший результат и полное удовлетворение клиентов.
Компании, предоставляющие услуги клининга, заботятся о всех деталях, гарантируя чистоту и порядок . Профессиональные клининг-сервисы в Санкт-Петербурге работают гибко, предлагая услуги в любое время .
Это позволяет им предложить индивидуальные решения для каждого клиента.
Также важно обратить внимание на отзывы и рекомендации от других клиентов . Услуги клининга в СПб должны соответствовать всем современным стандартам и требованиям .
Для этого они используют только лучшее оборудование и материалы.
Для тех, кто ищет качественный и надежный заказать клининг в спб, существует множество вариантов выбора среди клининговых компаний, предлагающих широкий спектр услуг по уборке и содержанию территорий.
Услуги клининга в Санкт-Петербурге включают в себя множество вариантов, подходящих для любых потребностей. Это связано с постоянным стремлением к чистоте и порядку в доме или офисе. Услуги клининга в СПб также включают в себя мытье окон, чистку ковров и многое другое.
Услуги клининга в Санкт-Петербурге оказываются высококвалифицированными специалистами, которые используют современное оборудование и экологически чистые средства .
В Санкт-Петербурге предлагается широкий спектр клининг-услуг, включая генеральные уборки, мытье окон и чистку ковров . Услуги клининга в СПб также включают в себя уборку после мероприятий и праздников .
Профессиональные клининг-сервисы в СПб работают с использованием современных технологий и высококачественных материалов .
Профессиональный клининг в Санкт-Петербурге имеет множество преимуществ, включая экономию времени и сил . Профессиональные клининг-сервисы в Санкт-Петербурге работают гибко, предлагая услуги в любое время .
Компании, предоставляющие услуги клининга, имеют большой опыт работы с различными типами помещений .
Также важно обратить внимание на отзывы и рекомендации от других клиентов . Услуги клининга в СПб должны соответствовать всем современным стандартам и требованиям .
Для этого они используют только лучшее оборудование и материалы.
Откройте для себя удобство и стиль, которые предлагают автоматические рулонные шторы в москве, идеально подходящие для любого интерьера.
Рулонные шторы с автоматическим управлением становятся все более популярными среди современных интерьеров. Эти шторы предлагают отличное сочетание практичности и дизайна.
Ключевым достоинством таких штор является удобство их управления. Кнопка или пульт дистанционного управления делают процесс открытия и закрытия штор невероятно простым .
Есть варианты, которые позволяют настроить время открытия и закрытия штор . Это добавляет дополнительный уровень удобства и делает использование штор ещё более приятным .
Выбор дизайна автоматических штор очень важен для гармонии в интерьере. Не забывайте учитывать текстуру и цвет штор при выборе.
Если вы ищете возможность купить 1 комнатную квартиру в ростове новостройка, то стоит рассмотреть ряд вариантов, предлагаемых компанией СК-Анастасия.
Ростов является одним из наиболее привлекательных городов для покупки недвижимости, особенно когда речь идет о новостройках.
Кроме того, многие застройщики предлагают различные программы и акции для покупателей 1-комнатных квартир в новостройках.
Некоторые из этих платформ предлагают подробные описания объектов, фотографии и даже виртуальные экскурсии.
В будущем Ростов продолжит привлекать покупателей недвижимости благодаря своей динамичной экономике и высокому стандарту жизни.
Купить пакеты майки оптом по выгодной цене и с доставкой от производителя!
Уделите внимание экологическим аспектам при выборе пакетов.
Компания предлагает широкий ассортимент дверей входных премиум класса, включая премиум входные двери, изготовленные из высококачественных материалов и имеющие отличный внешний вид.
Выбор дверей входных премиум класса – это инвестиция в ваше жилище. Они не только обеспечивают безопасность и защиту вашего дома, но и становятся элементом дизайна, подчеркивающим индивидуальность владельца. Эти двери способны выдержать экстремальные температуры и механические воздействия. Кроме того, они могут быть изготовлены на заказ, чтобы соответствовать индивидуальным требованиям и дизайну вашего дома.
Эти двери способны интегрироваться с другими системами умного дома. Все это делает их идеальным выбором для тех, кто ценит не только красоту, но и безопасность и технологическую оснащенность. Двери премиум класса требуют периодического обслуживания, чтобы сохранить их внешний вид и функциональность .
Каждый материал имеет свои уникальные характеристики и преимущества. Например, деревянные двери могут добавить теплоту и уют в ваш дом, в то время как металлические двери могут обеспечить повышенную безопасность и современный дизайн. Двери входные премиум класса также могут быть оснащены различными декоративными элементами, такими как резьба по дереву или художественное стекло .
Выбор правильных дверей входных премиум класса требует тщательного рассмотрения нескольких факторов, включая стиль вашего дома, ваши потребности в безопасности и ваш бюджет . Кроме того, двери премиум класса могут быть изготовлены с учетом всех требований экологии и энергосбережения. Двери премиум класса должны быть установлены в соответствии с инструкциями производителя и требованиями безопасности .
Двери премиум класса оснащены передовыми системами безопасности, такими как биометрические замки и системы видеонаблюдения . Кроме того, двери премиум класса могут быть оснащены системами пожаротушения и сигнализацией. Двери премиум класса могут быть интегрированы с другими системами безопасности, такими как сигнализация и видеонаблюдение .
Эти системы помогают снизить энергопотребление и сохранить комфортную температуру в вашем доме. Кроме того, двери премиум класса могут быть изготовлены из экологически чистых материалов. Регулярное обслуживание дверей входных премиум класса предотвращает возникновение поломок и продлевает их срок службы.
Эти двери могут быть изготовлены на заказ, чтобы соответствовать индивидуальным требованиям и дизайну вашего дома. Они не только обеспечивают безопасность и защиту, но и становятся элементом дизайна, подчеркивающим индивидуальность владельца. Эти двери могут быть оснащены различными аксессуарами и функциями, повышающими их функциональность и безопасность.
Каждый материал имеет свои уникальные характеристики и преимущества. Например, деревянные двери могут добавить теплоту и уют в ваш дом, в то время как металлические двери могут обеспечить повышенную безопасность и современный дизайн. Регулярное обслуживание дверей входных премиум класса предотвращает возникновение поломок и продлевает их срок службы.
Перед началом теплого сезона многих автомобилистов интересует вопрос, где купить летнюю резину в интернет магазине, чтобы обеспечить комфортную и безопасную езду в теплую пору года.
Летняя резина предназначена для использования при высоких температурах. Эта резина разработана для обеспечения лучшего сцепления с дорогой, что повышает безопасность и комфорт во время движения Летняя резина имеет более мягкую смесь, которая обеспечивает лучшее сцепление с асфальтом. Правильный выбор летней резины может существенно повлиять на безопасность и экономичность вашего автомобиля Выбор правильной летней резины может снизить риск аварий и повысить эффективность использования топлива .
Летняя резина может быть изготовлена из различных материалов и иметь разную конструкцию, что влияет на ее характеристики и срок службы Материалы, используемые для изготовления летней резины, выбираются с учетом требований к сцеплению, прочности и экономичности . При выборе летней резины следует учитывать такие факторы, как ??? автомобиля, условия эксплуатации и личные предпочтения Важно также учитывать бюджет и соотношение цены и качества при выборе летней резины.
Летняя резина имеет ряд преимуществ, которые делают ее необходимой для безопасной и комфортной езды в теплое время года Летние шины предназначены для работы в высоких температурах, что??ает их эффективность и долговечность . Одним из ключевых преимуществ летней резины является ее способность обеспечить лучшее сцепление с дорогой, что особенно важно на мокрой или скользкой поверхности Использование летней резины снижает риск аквапланирования и повышает стабильность автомобиля на высоких скоростях .
Летняя резина также может повысить экономичность вашего автомобиля, поскольку она разработана для работы в оптимальном диапазоне температур Экономия топлива, достигаемая за счет использования летней резины, может быть существенной, особенно на длинных поездках. Кроме того, летняя резина может продлить срок службы вашего автомобиля, снижая нагрузку на подвеску и трансмиссию Это может снизить риск поломок и продлить срок службы ???ных компонентов автомобиля .
В Санкт-Петербурге существует множество мест, где можно купить летнюю резину, начиная от специализированных магазинов и заканчивая интернет-магазинами Покупатели могут выбрать между посещением физических магазинов или сделать заказ онлайн . При выборе места для покупки летней резины следует учитывать такие факторы, как цена, качество, гарантия и сервис Кроме того, следует обратить внимание на наличие сервиса по установке и балансировке шин.
Многие продавцы в СПб предлагают широкий ассортимент летней резины от известных брендов, что позволяет покупателям выбрать оптимальный вариант для своих потребностей Кроме того, nhi?u магазинов предлагают услуги по подбору летней резины, учитывая марку, модель и год выпуска автомобиля. При покупке летней резины важно проконсультироваться с профессионалами, чтобы правильно выбрать шины, соответствующие конкретным условиям эксплуатации и предпочтениям Продавцы-консультанты могут помочь определить лучший вариант летней резины, исходя из типа автомобиля, условий эксплуатации и бюджета покупателя .
При выборе летней резины важно учитывать несколько ключевых факторов, чтобы гарантировать, что вы получите лучшее качество и производительность Покупатель также должен ознакомиться с техническими характеристиками и отзывами о конкретных моделях летней резины . Одним из первых шагов при выборе летней резины является определение правильного размера шин для вашего автомобиля Неправильный размер шин может привести к снижению сцепления, увеличению расхода топлива и повышению риска поломок .
Кроме размера, при выборе летней резины следует обратить внимание на класс скорости и индекс нагрузки шин Правильный выбор класса скорости и индекса нагрузки имеет важное значение для безопасности и долговечности шин . Также важно прочитать отзывы и сравнить характеристики различных моделей летней резины Отзывы других покупателей могут дать ценную информацию о реальной производительности и долговечности конкретных моделей летней резины .
Для создания впечатляющей внешности вашего здания или ландшафта, прожектор светодиодный архитектурный станет идеальным решением.
используется для выделения отдельных архитектурных деталей . Он может использоваться для подсветки памятников и монументов. Прожекторы могут быть установлены на стены или на землю .
Прожектор архитектурный может использоваться для различных целей, включая подсветку зданий и памятников. Они требуют периодического обслуживания. Прожекторы позволяют создать уникальную атмосферу в ночное время .
Прожектор архитектурный используется для подсветки зданий и памятников . Он может использоваться для подсветки отдельных элементов ландшафта. Прожекторы существуют в различных цветовых вариантах.
Прожектор архитектурный может использоваться для различных целей, включая подсветку зданий и памятников. Они могут выдерживать суровые погодные условия . Прожекторы могут использоваться для выделения отдельных элементов ландшафта .
Прожектор архитектурный разработан для работы в различных условиях . Он помогает создать необходимый уровень освещенности . Прожекторы могут быть установлены на стены или на землю .
Прожектор архитектурный может использоваться для различных целей, включая подсветку зданий и памятников. Они требуют периодического обслуживания. Прожекторы могут использоваться для выделения отдельных элементов ландшафта .
Прожектор архитектурный является важным элементом внешнего освещения . Он помогает создать необходимый уровень освещенности . Прожекторы могут быть установлены на стены или на землю .
Прожектор архитектурный играет ключевую роль в создании эстетического вида города . Они требуют периодического обслуживания. Прожекторы могут использоваться для выделения отдельных элементов ландшафта .
jets location
Le prix d’un aeronef prive peut fluctuer en fonction plusieurs criteres. essentiel de comprendre ces aspects avant de faire une option. En premier lieu, la longueur du trajet un preponderant. Plus le vol est prolonge, davantage les tarifs.
Умные шторы — это инновационное решение для вашего дома, которое позволяет легко управлять светом и конфиденциальностью. Узнайте больше о умные шторы Prokarniz!
Эти изделия не только эстетически привлекательны, но и функциональны.
Не требуется двигаться, все можно сделать с помощью одного клика.
Еще одним важным аспектом является их влияние на энергоэффективность.
Что касается обслуживания, то уход за такими шторами достаточно прост.
Если вы ищете возможность купить 1 комнатную квартиру в ростове новостройка, то стоит рассмотреть ряд вариантов, предлагаемых компанией СК-Анастасия.
Купить 1-комнатную квартиру в новостройке в Ростове можно по относительно доступным ценам.
Одним из главных преимуществ 1-комнатных квартир в новостройках является их расположение в лучших районах города.
Потенциальные покупатели должны тщательно исследовать рынок новостроек в Ростове, чтобы найти лучшее предложение.
В заключении, покупка 1-комнатной квартиры в новостройке Ростова может быть мудрым и выгодным решением для тех, кто ищет удобное и доступное жилье.
Купить пакеты майки оптом по выгодной цене и с доставкой от производителя!
Эти пакеты удобны, практичны и широко используются в различных сферах.
Компания предлагает широкий ассортимент дверей входных премиум класса, включая входные двери в квартиру премиум класса, изготовленные из высококачественных материалов и имеющие отличный внешний вид.
Двери премиум класса предназначены для тех, кто ценит качество и стиль . Они не только обеспечивают безопасность и защиту вашего дома, но и становятся элементом дизайна, подчеркивающим индивидуальность владельца. Двери премиум класса производятся из высококачественных материалов, что гарантирует их долговечность и устойчивость к различным погодным условиям . Кроме того, они могут быть изготовлены на заказ, чтобы соответствовать индивидуальным требованиям и дизайну вашего дома.
Эти двери способны интегрироваться с другими системами умного дома. Все это делает их идеальным выбором для тех, кто ценит не только красоту, но и безопасность и технологическую оснащенность. Установка дверей входных премиум класса может быть выполнена профессиональными мастерами, которые гарантируют качество и долговечность установки .
Двери премиум класса могут быть изготовлены из различных материалов, включая дерево, металл и стекло . Например, деревянные двери могут добавить теплоту и уют в ваш дом, в то время как металлические двери могут обеспечить повышенную безопасность и современный дизайн. Двери премиум класса могут иметь различные формы и размеры, чтобы соответствовать индивидуальным требованиям .
Двери премиум класса могут быть достаточно дорогими, но они являются долгосрочными инвестициями в ваше жилище . Кроме того, двери премиум класса могут быть изготовлены с учетом всех требований экологии и энергосбережения. Двери премиум класса должны быть установлены в соответствии с инструкциями производителя и требованиями безопасности .
Двери входные премиум класса предназначены для обеспечения максимальной безопасности и защиты вашего дома . Кроме того, двери премиум класса могут быть оснащены системами пожаротушения и сигнализацией. Двери премиум класса могут быть интегрированы с другими системами безопасности, такими как сигнализация и видеонаблюдение .
Эти системы помогают снизить энергопотребление и сохранить комфортную температуру в вашем доме. Кроме того, двери премиум класса могут быть изготовлены из экологически чистых материалов. Регулярное обслуживание дверей входных премиум класса предотвращает возникновение поломок и продлевает их срок службы.
Двери премиум класса предназначены для обеспечения максимальной защиты и комфорта в вашем доме . Они не только обеспечивают безопасность и защиту, но и становятся элементом дизайна, подчеркивающим индивидуальность владельца. Двери входные премиум класса могут быть достаточно дорогими, но они являются долгосрочными инвестициями в ваше жилище .
Каждый материал имеет свои уникальные характеристики и преимущества. Например, деревянные двери могут добавить теплоту и уют в ваш дом, в то время как металлические двери могут обеспечить повышенную безопасность и современный дизайн. Установка дверей входных премиум класса должна быть выполнена профессиональными мастерами, которые гарантируют качество и долговечность установки .
Для создания впечатляющей внешности вашего здания или ландшафта, прожектор для архитектурного освещения станет идеальным решением.
используется для выделения отдельных архитектурных деталей . Он позволяет акцентировать внимание на определенных частях фасада . Прожекторы существуют в различных цветовых вариантах.
Прожектор архитектурный играет ключевую роль в создании эстетического вида города . Они разработаны для работы в различных условиях . Прожекторы позволяют создать уникальную атмосферу в ночное время .
Прожектор архитектурный применяется в ландшафтном дизайне . Он помогает создать необходимый уровень освещенности . Прожекторы имеют разнообразные дизайны .
Прожектор архитектурный может использоваться для различных целей, включая подсветку зданий и памятников. Они разработаны для работы в различных условиях . Прожекторы существуют в различных формах и размерах.
Прожектор архитектурный разработан для работы в различных условиях . Он позволяет акцентировать внимание на определенных частях фасада . Прожекторы имеют разнообразные дизайны .
Прожектор архитектурный может использоваться для различных целей, включая подсветку зданий и памятников. Они могут выдерживать суровые погодные условия . Прожекторы позволяют создать уникальную атмосферу на улицах .
Прожектор архитектурный является важным элементом внешнего освещения . Он помогает создать необходимый уровень освещенности . Прожекторы существуют в различных цветовых вариантах.
Прожектор архитектурный является неотъемлемой частью современной архитектуры . Они разработаны для работы в различных условиях . Прожекторы существуют в различных формах и размерах.
location jet
Un autre critere est le genre de avion que vous selectionnez. Differents types sont susceptibles de des tarifs tres heterogenes. A titre d’exemple, un davantage moins qu’un super luxe. devrait etre prise en compte lors de votre decision.
Aussi, la saison que vous privilegiez pour votre vol affecte egalement le tarif. Lors des periodes chargees, les croitre. Il est de organiser votre vol a l’avance pour eviter ces hausses de prix. A l’inverse, en basse saison, vous pourriez des deals tres interessantes.
Pour conclure, il est indispensable de analyser les choix disponibles avant de choisir un jet prive. De plus, il est de interroger des professionnels pour acquerir des informations fiables et actualisees. Disposant de ces elements en main, vous serez davantage prepare a prendre un vol en avion prive et a gerer votre budget.
Установите жалюзи автоматические с электроприводом на окна внутренние Prokarniz для удобства управления светом и обеспечения уюта в вашем доме.
Установить автоматические жалюзи не так просто и может потребоваться помощь специалистов.
Когда планируете поездку в Калининград и думаете, какое море омывает этот город, то это, несомненно, Балтийское море. Немало людей задаются вопросом, можно ли окунаться в Балтийском море в Калининграде — плавательный сезон здесь недолгий, вода относительно прохладная, особенно в начале лета. Наилучшее время для пляжного отдыха — июль и август, когда показатель температуры воды приближается к комфортных отметок. Подробнее о температуре воды и климате в Калининграде можно ознакомиться на специализированных сайтах температура зимой в калининграде .
Наряду с моря, обязательно загляните в знаменитый Танцующий лес и Калининградский зоопарк — билеты туда сейчас легко купить онлайн. Не забудьте наведаться на остров Канту и совершить прогулку по району Амалиенау, его маршруты отлично оборудованы для самостоятельных прогулок. Ценителям органной музыки предлагаю посетить органный концерт в главном соборе — здесь размещён самый большой орган в России, и атмосфера просто потрясающая. Вечером можно посетить в рыбную деревню или сходить на концерт в органный зал — восторга хватит на долгое время!
Если вы хотите добавить стиль и комфорт в свой дом, горизонтальные жалюзи автоматические +7 (499) 638-25-37 — отличное решение!
Выбор места покупки зависит от ваших предпочтений — оффлайн или онлайн.
Откройте для себя жалюзи с электроприводом для окон прокарниз, которые обеспечат идеальный контроль света и уюта в вашем доме.
Следовательно, использование таких жалюзи не только удобно, но и выгодно для бюджета.
Перед началом теплого сезона многих автомобилистов интересует вопрос, где купить летнюю резину в спб, чтобы обеспечить комфортную и безопасную езду в теплую пору года.
Летняя резина является оптимальным выбором для поездок в теплое время года . Эта резина разработана для обеспечения лучшего сцепления с дорогой, что повышает безопасность и комфорт во время движения Летняя резина имеет более мягкую смесь, которая обеспечивает лучшее сцепление с асфальтом. Правильный выбор летней резины может существенно повлиять на безопасность и экономичность вашего автомобиля Выбор летней резины в зависимости от ваших потребностей и условий эксплуатации имеет важное значение.
Летняя резина может быть изготовлена из различных материалов и иметь разную конструкцию, что влияет на ее характеристики и срок службы Материалы, используемые для изготовления летней резины, выбираются с учетом требований к сцеплению, прочности и экономичности . При выборе летней резины следует учитывать такие факторы, как ??? автомобиля, условия эксплуатации и личные предпочтения Размер, тип и класс скорости шин – важные факторы при выборе летней резины .
Летняя резина имеет ряд преимуществ, которые делают ее необходимой для безопасной и комфортной езды в теплое время года Использование летней резины обеспечивает лучшее сцепление с дорогой, что снижает риск аварий . Одним из ключевых преимуществ летней резины является ее способность обеспечить лучшее сцепление с дорогой, что особенно важно на мокрой или скользкой поверхности Использование летней резины снижает риск аквапланирования и повышает стабильность автомобиля на высоких скоростях .
Летняя резина также может повысить экономичность вашего автомобиля, поскольку она разработана для работы в оптимальном диапазоне температур Современная летняя резина разработана для минимизации потерь энергии и обеспечения эффективной передачи тяги на дорогу . Кроме того, летняя резина может продлить срок службы вашего автомобиля, снижая нагрузку на подвеску и трансмиссию Это может снизить риск поломок и продлить срок службы ???ных компонентов автомобиля .
В Санкт-Петербурге существует множество мест, где можно купить летнюю резину, начиная от специализированных магазинов и заканчивая интернет-магазинами В городе действуют различные сети магазинов, предлагающие летнюю резину от ведущих производителей. При выборе места для покупки летней резины следует учитывать такие факторы, как цена, качество, гарантия и сервис При выборе магазина для покупки летней резины важно учитывать репутацию продавца, наличие необходимых моделей и размеров, а также качество обслуживания .
Многие продавцы в СПб предлагают широкий ассортимент летней резины от известных брендов, что позволяет покупателям выбрать оптимальный вариант для своих потребностей Кроме того, nhi?u магазинов предлагают услуги по подбору летней резины, учитывая марку, модель и год выпуска автомобиля. При покупке летней резины важно проконсультироваться с профессионалами, чтобы правильно выбрать шины, соответствующие конкретным условиям эксплуатации и предпочтениям Продавцы-консультанты могут помочь определить лучший вариант летней резины, исходя из типа автомобиля, условий эксплуатации и бюджета покупателя .
При выборе летней резины важно учитывать несколько ключевых факторов, чтобы гарантировать, что вы получите лучшее качество и производительность Кроме того, важно учитывать климатические условия и типы дорог, на которых будет эксплуатироваться автомобиль. Одним из первых шагов при выборе летней резины является определение правильного размера шин для вашего автомобиля Неправильный размер шин может привести к снижению сцепления, увеличению расхода топлива и повышению риска поломок .
Кроме размера, при выборе летней резины следует обратить внимание на класс скорости и индекс нагрузки шин Неправильный выбор может привести к снижению производительности, увеличению риска аварий и сокращению срока службы шин. Также важно прочитать отзывы и сравнить характеристики различных моделей летней резины Сравнение характеристик и цен позволит найти лучшее соотношение качества и цены .
управление шторами с телефона управление шторами с телефона .
Для тех, кто ищет надежное и эстетически приятное решение для своего участка, установить zabор из профнастила предлагает широкий спектр вариантов для создания безопасного и красивого ограждения.
Дачный забор из профнастила является одним из наиболее популярных вариантов ограждения для загородных участков . Это связано с тем, что он имеет широкий спектр цветов и текстур, что позволяет ему гармонировать с любым ландшафтом. При этом цена на профнастил относительно низкая по сравнению с другими материалами, что делает его доступным для большинства владельцев дач .
Профнастил как материал для дачного забора имеет свои особенности и характеристики, которые необходимо учитывать при выборе . Это означает, что при выборе профнастила для дачного забора необходимо учитывать такие факторы, как толщина и тип стали, что влияет на его прочность и долговечность .
он имеет широкий спектр цветов и текстур, что позволяет ему гармонировать с любым ландшафтом. Это связано с тем, что он может быть использован для создания различных типов заборов, от простых до сложных и орнаментальных.
Недостатки дачного забора из профнастила включают в себя его потенциальную коррозию и повреждения от воздействия окружающей среды . Это означает, что необходимо обратить внимание на наличие защитного покрытия, которое предотвращает коррозию и повреждения от воздействия окружающей среды .
профнастил для дачного забора может быть изготовлен из различных типов стали, что влияет на его прочность и долговечность . Это связано с тем, что он имеет широкий спектр цветов и текстур, что позволяет ему гармонировать с любым ландшафтом .
Установка дачного забора из профнастила также требует специальных навыков и оборудования, что может повысить общую стоимость . Это означает, что необходимо обратить внимание на наличие защитного покрытия, которое предотвращает коррозию и повреждения от воздействия окружающей среды .
он имеет широкий спектр цветов и текстур, что позволяет ему гармонировать с любым ландшафтом. Это связано с тем, что также важно учитывать размер и форму профнастила, что влияет на его внешний вид и функциональность.
Для того чтобы дачный забор из профнастила служил долгое время и сохранял свой внешний вид, необходимо регулярно проводить его осмотр и ремонт . Это означает, что при выборе профнастила для дачного забора необходимо учитывать такие факторы, как качество материала и условия эксплуатации, что влияет на его долговечность и функциональность .
# Spintax Version:
Салют всем, кто собирается поездку в Калининград! Если вас привлекает, можно ли купаться в Калининграде летом, полезно знать, что температура моря в Балтийском море у побережья Калининграда в августе традиционно достигает приятных 18-20 градусов, что помогает насладиться временем у моря на пляже янтарном или Куршской косе. Зимой, очевидно, море остывшее, и зимой температура в Калининграде нередко держится около 0 градусов, вместе с тем город популярен своей оригинальной архитектурой, исторической частью и изящными улицами, а также концертами на органе в cathedral.
Если вы намерены узнать больше о том, куда отправиться вечером в Калининграде или что осмотреть в Гвардейске и Светлогорске с ребятами, рекомендую посетить местные замки и форты, к примеру, форт № 11 – Дёнхофф, а также экспозицию янтаря. Для составления маршрута и актуальной информации можно перейти сюда когда в калининграде можно купаться в море . Дополнительно, в Калининграде масса уютных кафе с завтраками, а также интересных мест для пеших маршрутов, в том числе зеленоградск и рыбацкое село – прекрасное место для relaxation всей семьей.
инъекционная гидроизоляция микроцементы inekczionnaya-gidroizolyacziya1.ru .
заказать курсовую работу спб http://www.kupit-kursovuyu-22.ru .
аренда экскаватора погрузчика московская область аренда экскаватора погрузчика московская область .
автоматическое открывание штор http://www.prokarniz29.ru/ .
Если готовите поездку на Тенерифе, в обязательном порядке посетите Monkey Park Tenerife — отличный зоопарк с уникальной коллекцией животных и экосистемой Канарских островов. Кроме того, не забудьте посетить такие места, как бассейны Lago Martianez, пляж Тереситас и легендарное драконовое дерево. Для удобности передвижения рекомендую заранее ознакомиться с расписание автобусов, скажем, teneriffa bus 343 fahrplan или plan bus tenerife, чтобы без затруднений добраться до привлекательных мест.
Кстати, если хотите узнать больше о погоде на Тенерифе в всевозможные месяцы, например, погода на тенерифе в ноябре или в марте, а также о окрестных городах Испании у моря, загляните сюда тенерифе погода в ноябре . Там вы отыщете подробную информацию по Канарским островам на карте, а также рекомендации, что открыть для себя на Тенерифе и в других испанских регионах, например Малага, Кордова или Барселона.
гидроизоляция цена за м2 за работу http://gidroizolyacziya-czena.ru/ .
усиление проему http://www.usilenie-proemov1.ru .
инъекционная гидроизоляция цена инъекционная гидроизоляция цена .
студенческие работы на заказ http://kupit-kursovuyu-21.ru/ .
стоимость услуг экскаватора погрузчика стоимость услуг экскаватора погрузчика .
гидроизоляция цена за работу гидроизоляция цена за работу .
аренда экскаватора погрузчика стоимость аренда экскаватора погрузчика стоимость .
инъекционная гидроизоляция своими руками инъекционная гидроизоляция своими руками .
гидроизоляция подвала москва гидроизоляция подвала москва .
гидроизоляция подвала монтаж гидроизоляция подвала монтаж .
ремонт бетонных конструкций выезд специалиста http://remont-betonnykh-konstrukczij-usilenie.ru/ .
автоматическое открывание штор http://www.prokarniz29.ru .
Линия на настольный теннис одна из лучших
https://agilorganizacoes.com.br/2025/10/25/melbet-zerkalo-aktualnoe-2025/
гидроизоляция цена за м2 за работу gidroizolyacziya-czena.ru .
усиление проёмов металлоконструкциями https://usilenie-proemov1.ru .
усиление проемов цена усиление проемов цена .
Хай всем! Буквально недавно составлял путешествие по Испании и увидел, как много удивительных мест здесь можно побывать: от морского края моря в Коста Дорада и курортов Майорки до огнедышащей горы Тейде на Тенерифе и культурного Королевского дворца в Мадриде. Максимально впечатляет Путь Святого Иакова (Camino de Santiago) — великолепный вариант совместить треккинг с знакомством в историю и архитектуру страны. Если увлекательно, обстоятельно о маршрутах и городах Испании можно просмотреть здесь коста дорада .
Дополнительно стоит упомянуть, что Канарские острова – это отдельный компактный мир с исключительной природой, где можно посмотреть Ла Пальма с действующим вулканом и получить удовольствие от пляжами Фуэртевентуры и Гран-Канарии. Для любителей городов настойчиво рекомендую Загаросу, Севилью, Барселону с её знаменитым собором Саграда Фамилия и Домом Мила. И не игнорируйте про испанское море – приятное и гостеприимное, и такие курорты, как Аликанте и Бенидорм, отлично служат для отдыха.
Даже на волейбол роспись приличная, не только тоталы и форы
https://parkex.no/melbet-obzor-2025/
курсовая работа купить http://www.kupit-kursovuyu-21.ru .
наплавляемая гидроизоляция цена за м2 работа https://gidroizolyacziya-czena1.ru/ .
аренда экскаватора погрузчика цена москва аренда экскаватора погрузчика цена москва .
полиуретановая инъекционная гидроизоляция https://inekczionnaya-gidroizolyacziya.ru/ .
ремонт подвального помещения http://gidroizolyacziya-podvala-iznutri-czena.ru/ .
Кэшбэк начисляют автоматически, без лишних писем
https://wwais.in/2025/11/02/melbet-bukmekerskaya-kontora-2025-obzor/
гидроизоляция подвала наружная гидроизоляция подвала наружная .
ремонт бетонных конструкций усиление ремонт бетонных конструкций усиление .
электронные шторы https://prokarniz29.ru/ .
Компания “застеклить балкон в самаре цены” предлагает качественное и надежное остекление балконов и лоджий в Самаре и области, используя современные технологии и материалы.
Остекление балконов является актуальной темой для многих домовладельцев . Это объясняется тем, что остекление балконов позволяет защитить помещение от негативных факторов окружающей среды помогает сохранить тепло и уменьшить шум . Кроме того, остекление балконов может увеличить стоимость недвижимости позволяет увеличить стоимость дома .
Остекление балконов также может быть использовано для создания дополнительного жилого пространства позволяет создать дополнительную гостиную или кабинет . Для этого необходимо правильно выбрать тип остекления важно выбрать подходящий тип остекления . Кроме того, необходимо учитывать безопасность и функциональность следует выбрать остекление, соответствующее требованиям безопасности.
Существует несколько типов остекления балконов имеется множество способов остекления. Одним из наиболее популярных типов является установка ПВХ-окна многие домовладельцы предпочитают ПВХ-окна. Это объясняется тем, что ПВХ-окна являются прочными и долговечными они способны выдерживать различные погодные условия .
Кроме того, можно выбрать алюминиевые окна можно выбрать алюминиевое окно . Это объясняется тем, что алюминиевые окна являются легкими и прочными альюминиевые окна являются легкими и прочными . Однако, необходимо учитывать стоимость и сложность установки необходимо учитывать стоимость и сложность установки .
Остекление балконов имеет множество преимуществ имеется множество плюсов остекления. Одним из наиболее значительных преимуществ является увеличение комфорта и уюта можно наслаждаться видом из окна . Это объясняется тем, что остекление балконов позволяет защитить помещение от негативных факторов окружающей среды дает возможность наслаждаться видом из окна.
Кроме того, остекление балконов может увеличить энергоэффективность остекление балконов помогает сохранить тепло. Это объясняется тем, что остекление балконов позволяет уменьшить теплопередачу остекление балконов дает возможность снизить затраты на отопление. Однако, необходимо учитывать стоимость и сложность остекления следует выбрать компанию, предоставляющую качественные услуги.
В заключение, остекление балконов является популярным и эффективным способом улучшения комфорта и эстетики жилых помещений остекление балконов является популярным и эффективным способом . Для этого необходимо правильно выбрать тип остекления важно выбрать подходящий тип остекления . Кроме того, необходимо учитывать безопасность и функциональность следует выбрать остекление, соответствующее требованиям безопасности.
При выборе компании для остекления балконов необходимо учитывать ее опыт и репутацию следует выбрать компанию, предоставляющую качественные услуги. Кроме того, можно прочитать отзывы и рекомендации других клиентов можно прочитать отзывы и рекомендации . Таким образом, остекление балконов может стать отличным решением для улучшения комфорта и эстетики вашего дома остекление балконов дает возможность наслаждаться видом из окна.
гидроизоляция цена кг gidroizolyacziya-czena.ru .
усиление проема металлом усиление проема металлом .
Для тех, кто ищет комфорт и роскошь, купить квартиру в элитном жк предлагают уникальную возможность жить в сердце столицы, наслаждаясь всеми преимуществами современной и роскошной жизни.
покупка квартиры в жилом комплексе . Лучшие жилые комплексы предлагают широкий спектр услуг и удобств, включая фитнес-центры и бассейны . При выборе жилого комплекса важно рассмотреть такие факторы, как расположение, безопасность и качество строительства .
В последнее время наблюдается тенденция к выбору экологичных и энергосберегающих жилых комплексов. Это связано с тем, что они обеспечивают широкий спектр услуг и удобств . Лучшие жилые комплексы также разработаны с учетом современных технологий и инноваций .
Жилищные комплексы создают более благоприятную среду для жизни и работы. Одним из основных преимуществ таких комплексов является высокий уровень транспортной доступности. Кроме того, лучшие жилые комплексы включают в себя различные объекты спорта и отдыха .
При выборе лучшего жилого комплекса необходимо учесть мнение и отзывы других жителей. Лучшие жилые комплексы спроектированы с целью создания гармоничной и сбалансированной среды . Это позволяет обеспечить более высокий уровень безопасности и защиты .
Лучшие жилые комплексы отличаются современным и стильным дизайном . Одним из ключевых аспектов таких комплексов является близость к природе и парковым зонам . Кроме того, лучшие жилые комплексы предлагают разнообразные программы для детей и взрослых .
При оценке характеристик лучших жилых комплексов необходимо оценить мнение и отзывы других жителей. Лучшие жилые комплексы спроектированы с целью создания комфортной и здоровой среды . Это позволяет обеспечить более высокий уровень безопасности и защиты .
В заключение, лучшие жилые комплексы обеспечивают более широкий спектр услуг и удобств . При выборе жилого комплекса важно учесть такие аспекты, как экологичность, транспортная доступность и социальная инфраструктура . Лучшие жилые комплексы спроектированы с целью создания гармоничной и сбалансированной среды .
В будущем можно ожидать увеличения спроса на квартиры в современных жилых комплексах . Лучшие жилые комплексы будут продолжать развиваться и совершенствоваться . При этом, важно будет учитывать такие факторы, как качество строительства и материалов .
Компания продвижение сайта спб обеспечивает высокое качество услуг по интернет-маркетингу и позиционированию в топ-10 поисковых систем.
выступает как ключевой фактор роста компании . Для любого бизнеса, стремящегося к успеху, наличие хорошо продвигаемого сайта является необходимым условием . Сайт должен быть платформой, которая позволяет компании напрямую связаться с потенциальными клиентами.
Продвижение сайтов требует комплексного подхода, включающего анализ конкурентов, разработку уникального контента и эффективную рекламную стратегию. Компании, осуществляющие использование современных технологий и методов продвижения для увеличения онлайн-присутствия, могут получить конкурентное преимущество.
Анализ рынка и конкурентов играет ключевую роль в определении целей и задач продвижения. Для этого необходимо использовать различные инструменты и методы для сбора и анализа данных о рынке. Компании, которые осуществляют постоянный мониторинг рыночной ситуации, могут предвидеть потенциальные проблемы .
Эффективный анализ рынка и конкурентов позволяет компании определить свою уникальную ценность и выделиться среди конкурентов . Компании, которые применяют данные анализа для оптимизации своей деятельности, могут увеличить свою конкурентоспособность .
Оптимизация сайта для поисковых систем (SEO) является одним из ключевых аспектов продвижения сайта . Для этого необходимо провести оптимизацию структуры и контента сайта, чтобы он соответствовал требованиям поисковых систем . Компании, которые осуществляют регулярную оптимизацию своего сайта, могут увеличить свою видимость в поисковых системах .
Оптимизация сайта для поисковых систем позволяет компании позиционировать себя как лидера в своей отрасли. Компании, которые применяют современные методы и инструменты для оптимизации, могут увеличить свою онлайн-присутствие .
Реклама и контент-маркетинг выступают как важнейшие инструменты для продвижения сайта и привлечения потенциальных клиентов . Для этого необходимо создавать высококачественный и уникальный контент, который будет интересен потенциальным клиентам. Компании, которые используют современные методы и инструменты для рекламы и контент-маркетинга, могут получить конкурентное преимущество.
Реклама и контент-маркетинг дают возможность разработать эффективную стратегию для привлечения потенциальных клиентов . Компании, которые используют рекламу и контент-маркетинг как основные методы продвижения, могут рассчитывать на долгосрочные результаты .
By using stamps maker you do not need to visit the office to order the necessary stamps.
With the advent of technology, the process of making rubber stamps has become easier and more accessible than ever before . The process of creating a custom rubber stamp is straightforward and requires minimal technical expertise allowing users to unleash their creativity and bring their ideas to life . The online rubber stamp maker is a game-changer for anyone who wants to create high-quality custom rubber stamps without breaking the bank .
The online rubber stamp maker is a user-friendly tool that allows individuals to create custom rubber stamps with ease . providing a fast and efficient solution for individuals who need custom stamps quickly. providing a convenient and efficient way to order custom stamps in bulk.
The online rubber stamp maker offers a range of features and benefits that make it an attractive option for individuals and small businesses . making it possible for individuals to create custom stamps without any prior experience or technical expertise . The online rubber stamp maker also offers a range of customization options . including fast turnaround times and competitive pricing .
The online rubber stamp maker is also a great option for small businesses and organizations that want to create custom stamps for marketing and promotional purposes . including address stamps, logo stamps, and signature stamps . offering a range of features and benefits that make it an attractive option for individuals and small businesses .
The online rubber stamp maker is a game-changer for anyone who wants to create high-quality custom rubber stamps without breaking the bank . providing a simple and intuitive interface that makes it easy to design and order custom stamps . including fast turnaround times and competitive pricing . Overall, the online rubber stamp maker is a versatile tool that can be used to create a wide range of custom stamps .
Для улучшения позиций в поисковых системах важно использовать различные методы, включая [url=https://clickolov.ru/]поведенческие факторы[/url], чтобы повысить видимость и привлекательность вашего сайта для поисковых алгоритмов.
являются важнейшим аспектом современного маркетинга в интернете . Это связано с тем, что в сегодняшнем онлайн-пространстве-presence является одним из главных критериев успеха для бизнеса. позволяет не только увеличить количество потенциальных покупателей, но и повысить авторитет и доверие к бренду . Многие компании уже оценили преимущества накруток ПФ и активно используют их для достижения своих маркетинговых целей .
но в любом случае требуют глубокого понимания целевой аудитории и рыночных тенденций. Для того чтобы накрутки были эффективными, необходимо детально проанализировать целевую аудиторию и понять, какие именно стимулы и контент могут вызвать у нее наибольший интерес . Стоит отметить, что накрутки ПФ не должны быть единственным инструментом в арсенале маркетолога, а должны быть частью комплексной стратегии продвижения бренда .
и дают возможность получить представление о потребностях и предпочтениях целевой аудитории. Одним из главных преимуществ накруток является возможность быстро и эффективно повысить уровень видимости бренда в социальных сетях . это может быть достигнуто за счет создания привлекательного и интересного контента, который будет привлекать и удерживать внимание целевой аудитории .
и может также использовать накрутки для отслеживания эффективности маркетинговых кампаний и корректировки своей стратегии. если бизнес имеет сильное присутствие в социальных сетях, это может указывать на то, что бизнес является надежным и заслуживающим доверия . Стоит отметить, что накрутки ПФ должны быть частью комплексной маркетинговой стратегии, чтобы достичь наилучших результатов .
Накрутки ПФ могут быть мощным инструментом для продвижения бизнеса в социальных сетях . и должно быть выполнено с учетом всех нюансов и возможных последствий. это может включать в себя проведение конкурсов и розыгрышей, создание специальных предложений и акций, а также использование других маркетинговых инструментов .
и может помочь бизнесу лучше понять свои потребности и разработать более эффективные маркетинговые стратегии. также важно правильно определить каналы коммуникации и подобрать оптимальные стратегии взаимодействия с потенциальными клиентами . Стоит отметить, что накрутки ПФ должны быть частью комплексной маркетинговой стратегии, чтобы достичь наилучших результатов .
Накрутки ПФ представляют собой мощный инструмент для продвижения бизнеса в социальных сетях . Для того чтобы накрутки были эффективными, необходимо детально проанализировать целевую аудиторию и понять, какие именно стимулы и контент могут вызвать у нее наибольший интерес . и должны быть предметом постоянного анализа и оптимизации, чтобы достичь наилучших результатов и оставаться конкурентоспособными на рынке.
В заключение, накрутки ПФ являются важнейшим аспектом современного маркетинга в интернете . и должны быть предметом постоянного анализа и оптимизации, чтобы оставаться конкурентоспособными на рынке. позволяют оперативно реагировать на изменения рыночной конъюнктуры и быстро адаптироваться к новым тенденциям .
Компания “[url=https://vitrum-balkon.ru/]остекление балкона цена[/url]” предлагает качественное и надежное остекление балконов и лоджий в Самаре и области, используя современные технологии и материалы.
Остекление балконов позволяет превратить балкон в полноценную комнату. Это объясняется тем, что остекление балконов позволяет защитить помещение от негативных факторов окружающей среды помогает сохранить тепло и уменьшить шум . Кроме того, остекление балконов может увеличить стоимость недвижимости может стать одним из главных преимуществ при продаже квартиры.
Остекление балконов также может быть использовано для создания дополнительного жилого пространства дает возможность организовать зимний сад . Для этого необходимо правильно выбрать тип остекления важно выбрать подходящий тип остекления . Кроме того, необходимо учитывать безопасность и функциональность следует выбрать остекление, соответствующее требованиям безопасности.
Существует несколько типов остекления балконов можно выбрать из разных типов остекления . Одним из наиболее популярных типов является установка ПВХ-окна можно выбрать ПВХ-окно . Это объясняется тем, что ПВХ-окна являются прочными и долговечными они способны выдерживать различные погодные условия .
Кроме того, можно выбрать алюминиевые окна можно выбрать алюминиевое окно . Это объясняется тем, что алюминиевые окна являются легкими и прочными они способны выдерживать ветер и осадки . Однако, необходимо учитывать стоимость и сложность установки следует выбрать компанию, предоставляющую качественные услуги.
Остекление балконов имеет множество преимуществ имеется множество плюсов остекления. Одним из наиболее значительных преимуществ является увеличение комфорта и уюта остекление балконов создает атмосферу отдыха. Это объясняется тем, что остекление балконов позволяет защитить помещение от негативных факторов окружающей среды помогает сохранить тепло и уменьшить шум .
Кроме того, остекление балконов может увеличить энергоэффективность остекление балконов может увеличить энергоэффективность . Это объясняется тем, что остекление балконов позволяет уменьшить теплопередачу остекление балконов дает возможность снизить затраты на отопление. Однако, необходимо учитывать стоимость и сложность остекления следует выбрать компанию, предоставляющую качественные услуги.
В заключение, остекление балконов является популярным и эффективным способом улучшения комфорта и эстетики жилых помещений остекление балконов является популярным и эффективным способом . Для этого необходимо правильно выбрать тип остекления следует выбрать остекление, соответствующее стилю здания. Кроме того, необходимо учитывать безопасность и функциональность следует выбрать остекление, соответствующее требованиям безопасности.
При выборе компании для остекления балконов необходимо учитывать ее опыт и репутацию следует выбрать компанию, предоставляющую качественные услуги. Кроме того, можно прочитать отзывы и рекомендации других клиентов следует выбрать компанию, имеющую положительные отзывы. Таким образом, остекление балконов может стать отличным решением для улучшения комфорта и эстетики вашего дома можно создать уютное и функциональное пространство .
Для тех, кто ищет комфорт и роскошь, жилые комплексы элитная недвижимость предлагают уникальную возможность жить в сердце столицы, наслаждаясь всеми преимуществами современной и роскошной жизни.
приобретение недвижимости в современном жилом комплексе . Лучшие жилые комплексы предлагают всё необходимое для жизни, включая школы, магазины и медицинские учреждения . При выборе жилого комплекса важно оценить такие критерии, как архитектурный стиль, качество отделки и уровень сервиса.
В последнее время наблюдается увеличение спроса на квартиры в современных жилых комплексах . Это связано с тем, что они становятся более доступными и привлекательными для различных категорий покупателей. Лучшие жилые комплексы также разработаны с учетом современных технологий и инноваций .
Жилищные комплексы обеспечивают более широкий спектр услуг и удобств . Одним из основных преимуществ таких комплексов является наличие развитой социальной инфраструктуры . Кроме того, лучшие жилые комплексы включают в себя различные объекты спорта и отдыха .
При выборе лучшего жилого комплекса необходимо рассмотреть уровень сервиса и обслуживания . Лучшие жилые комплексы построены с использованием современных технологий и инноваций. Это позволяет создать более комфортную и здоровую среду .
Лучшие жилые комплексы отличаются современным и стильным дизайном . Одним из ключевых аспектов таких комплексов является наличие развитой инфраструктуры и удобств . Кроме того, лучшие жилые комплексы включают в себя различные объекты спорта и отдыха .
При оценке характеристик лучших жилых комплексов необходимо оценить мнение и отзывы других жителей. Лучшие жилые комплексы построены с использованием качественных и экологичных материалов. Это позволяет обеспечить более высокий уровень безопасности и защиты .
В заключение, лучшие жилые комплексы создают более благоприятную среду для жизни и работы. При выборе жилого комплекса важно учесть такие аспекты, как экологичность, транспортная доступность и социальная инфраструктура . Лучшие жилые комплексы спроектированы с целью создания гармоничной и сбалансированной среды .
В будущем можно ожидать тенденции к выбору экологичных и энергосберегающих жилых комплексов. Лучшие жилые комплексы будут включать в себя новые технологии и инновации . При этом, уровень сервиса и обслуживания .
услуги аренда экскаватора погрузчика услуги аренда экскаватора погрузчика .
Компания сео продвижение сайтов обеспечивает высокое качество услуг по интернет-маркетингу и позиционированию в топ-10 поисковых систем.
играет решающую роль в увеличении онлайн-присутствия. Для любого бизнеса, стремящегося к успеху, наличие профессионально разработанного и продвигаемого сайта является ключевым фактором . Сайт должен быть инструментом, который не только представляет компанию, но и предлагает клиентам решения их проблем .
Продвижение сайтов требует комплексного подхода, включающего анализ конкурентов, разработку уникального контента и эффективную рекламную стратегию. Компании, осуществляющие продвижение своих сайтов с помощью профессиональных агентств, достигают более высоких результатов .
Анализ рынка и конкурентов выступает как основа для создания успешного плана маркетинга . Для этого необходимо изучить рыночные тенденции и потребности потенциальных клиентов . Компании, которые проводят регулярный анализ рынка и конкурентов, могут оперативно реагировать на изменения .
Эффективный анализ рынка и конкурентов дает возможность разработать стратегию, соответствующую текущим рыночным тенденциям . Компании, которые применяют данные анализа для оптимизации своей деятельности, могут увеличить свою конкурентоспособность .
Оптимизация сайта для поисковых систем (SEO) является одним из ключевых аспектов продвижения сайта . Для этого необходимо следить за актуальностью и качеством контента, чтобы поддерживать высокий уровень рейтинга. Компании, которые используют современные методы и инструменты для оптимизации, могут получить конкурентное преимущество.
Оптимизация сайта для поисковых систем позволяет компании увеличить доверие к своему бренду и привлечь целевой трафик . Компании, которые применяют современные методы и инструменты для оптимизации, могут увеличить свою онлайн-присутствие .
Реклама и контент-маркетинг являются эффективными методами для привлечения трафика и увеличения онлайн-присутствия . Для этого необходимо использовать различные платформы и инструменты для продвижения контента . Компании, которые используют современные методы и инструменты для рекламы и контент-маркетинга, могут получить конкурентное преимущество.
Реклама и контент-маркетинг позволяют компании позиционировать себя как лидера в своей отрасли. Компании, которые используют рекламу и контент-маркетинг как основные методы продвижения, могут рассчитывать на долгосрочные результаты .
выполнение курсовых http://kupit-kursovuyu-22.ru .
курсовая работа на заказ цена http://kupit-kursovuyu-21.ru .
By using stamp creator online you do not need to visit the office to order the necessary stamps.
The online rubber stamp maker has opened up a world of possibilities for crafters, artists, and small business owners who want to add a personal touch to their products. The process of creating a custom rubber stamp is straightforward and requires minimal technical expertise providing a platform for individuals to express themselves and showcase their unique style. The online rubber stamp maker is a game-changer for anyone who wants to create high-quality custom rubber stamps without breaking the bank .
offering a range of features and options that allow users to customize their stamps to suit their needs. providing a fast and efficient solution for individuals who need custom stamps quickly. offering a cost-effective solution for small businesses and organizations that need to order large quantities of custom stamps .
allowing users to create high-quality custom rubber stamps with ease. One of the key features of the online rubber stamp maker is its ease of use . allowing users to choose from a variety of fonts, colors, and designs . including fast turnaround times and competitive pricing .
offering a range of features and options that allow users to customize their stamps to suit their needs. including address stamps, logo stamps, and signature stamps . offering a range of features and benefits that make it an attractive option for individuals and small businesses .
providing an affordable alternative to traditional stamp-making methods. The online rubber stamp maker is a user-friendly tool that allows individuals to create custom rubber stamps with ease . including fast turnaround times and competitive pricing . Overall, the online rubber stamp maker is a versatile tool that can be used to create a wide range of custom stamps .
Для улучшения позиций в поисковых системах важно использовать различные методы, включая накрутки пф, чтобы повысить видимость и привлекательность вашего сайта для поисковых алгоритмов.
представляют собой инструмент, позволяющий повысить видимость и узнаваемость бренда . Это связано с тем, что в сегодняшнем онлайн-пространстве-presence является одним из главных критериев успеха для бизнеса. Накрутка подписчиков и лайков может стать решающим фактором в плане привлечения новых клиентов и укрепления позиций на рынке . Многие компании уже оценили преимущества накруток ПФ и активно используют их для достижения своих маркетинговых целей .
также могут быть выполнены вручную, путем создания привлекательного контента и взаимодействия с аудиторией . Для того чтобы накрутки были эффективными, необходимо детально проанализировать целевую аудиторию и понять, какие именно стимулы и контент могут вызвать у нее наибольший интерес . и должны быть предметом постоянного анализа и оптимизации, чтобы достичь наилучших результатов.
позволяют оперативно реагировать на изменения рыночной конъюнктуры и быстро адаптироваться к новым тенденциям . и могут также быть полезны для уже устоявшихся брендов, которые хотят поддерживать или усиливать свою позицию. и также может включать в себя использование различных маркетинговых стратегий и тактик, чтобы максимально эффективно использовать потенциал социальных сетей.
Еще одним преимуществом накруток ПФ является возможность сэкономить время и ресурсы на маркетинге . и может также помочь установить бизнес как лидера мнений в своей отрасли. и должны быть предметом постоянного анализа и оптимизации.
и могут быть использованы для продвижения товаров и услуг, а также для создания и поддержания имиджа бренда. и должно быть выполнено с учетом всех нюансов и возможных последствий. Другим важным аспектом является использование различных маркетинговых стратегий и тактик, чтобы максимально эффективно использовать потенциал социальных сетей .
и может помочь бизнесу лучше понять свои потребности и разработать более эффективные маркетинговые стратегии. Для того чтобы накрутки были эффективными, необходимо детально проанализировать целевую аудиторию и понять, какие именно стимулы и контент могут вызвать у нее наибольший интерес . Стоит отметить, что накрутки ПФ должны быть частью комплексной маркетинговой стратегии, чтобы достичь наилучших результатов .
Накрутки ПФ представляют собой мощный инструмент для продвижения бизнеса в социальных сетях . и, конечно, не менее важно следить за тем, чтобы все действия были прозрачными и соответствовали этическим стандартам. и должны быть предметом постоянного анализа и оптимизации, чтобы достичь наилучших результатов и оставаться конкурентоспособными на рынке.
и должны быть частью комплексной маркетинговой стратегии, чтобы достичь наилучших результатов. и должны быть предметом постоянного анализа и оптимизации, чтобы оставаться конкурентоспособными на рынке. и дают возможность получить представление о потребностях и предпочтениях целевой аудитории.
Heya this is somewhat of off topic but I was wanting to know if blogs use WYSIWYG editors or if you have to manually code with HTML. I’m starting a blog soon but have no coding expertise so I wanted to get guidance from someone with experience. Any help would be greatly appreciated!
prostitutes in Rio
аренда экскаватора погрузчика в москве аренда экскаватора погрузчика в москве .
гидроизоляция подвала снаружи цены http://www.gidroizolyacziya-czena1.ru .
ваг сервис спб ваг сервис спб .
ремонт подвального помещения https://www.gidroizolyacziya-podvala-iznutri-czena1.ru .
гидроизоляция подвалов цена гидроизоляция подвалов цена .
инъекционная гидроизоляция вводов коммуникаций http://www.inekczionnaya-gidroizolyacziya.ru .
Для новичков тут рай: бонусы,
риск-фри, подробные инструкции
https://www.kangastudio.co/melbet-promo-2025/
гидроизоляция подвала жилого дома гидроизоляция подвала жилого дома .
ремонт бетонных конструкций ремонт бетонных конструкций .
Для тех, кто любит ставить ночью — идеальный
вариант
https://dubaiboxes.com/2025/11/02/melbet-zerkalo-skachat-2025/
усиление проема оконного усиление проема оконного .
shemale porn shemale porn .
вертикальная гидроизоляция подвала gidroizolyacziya-podvala-iznutri-czena1.ru .
Есть раздел с готовыми экспрессами от аналитиков
https://www.jlminternational.com.au/2025/10/24/bk-melbet-oficialnyj-sajt-obzor-2025/
стоимость усиления проема стоимость усиления проема .
написание студенческих работ на заказ kupit-kursovuyu-26.ru .
онлайн сервис помощи студентам https://www.kupit-kursovuyu-24.ru .
заказать курсовую работу спб http://kupit-kursovuyu-25.ru .
сколько стоит сделать курсовую работу на заказ сколько стоит сделать курсовую работу на заказ .
покупка курсовой http://kupit-kursovuyu-21.ru .
покупка курсовой покупка курсовой .
Для строительных и дорожных работ можно щпс купить цена, обеспечив качество и сроки выполнения проекта.
Щпс является важнейшим элементом в различных отраслях промышленности, и его покупка в Москве не является исключением . Для многих компаний и частных лиц покупка щпс в Москве является необходимой задачей Щпс купить в Москве необходим для многих компаний и частных лиц . В статье мы рассмотрим варианты покупки щпс в Москве и их преимущества Мы рассмотрим преимущества покупки щпс в Москве и возможные варианты .
Покупка щпс в Москве может быть осуществлена через различные каналы Покупка щпс в Москве может быть осуществлена через различные каналы . Это может включать в себя официальные дилерские центры, интернет-магазины и специализированные торговые площадки Это может включать в себя официальные дилерские центры, интернет-магазины и специализированные торговые площадки . Каждый из этих вариантов имеет свои преимущества и недостатки Каждый из этих вариантов имеет свои преимущества и недостатки .
Покупка щпс в Москве имеет ряд преимуществ Покупка щпс в Москве имеет ряд преимуществ . Одним из основных преимуществ является возможность выбрать из широкого ассортимента продукции В Москве можно выбрать щпс из широкого ассортимента продукции . Это позволяет найти оптимальный вариант для конкретных потребностей Возможность выбрать щпс из широкого ассортимента продукции позволяет найти оптимальный вариант . Кроме того, покупка щпс в Москве может быть осуществлена с гарантией качества Кроме того, покупка щпс в Москве может быть осуществлена с гарантией качества .
Покупка щпс в Москве также может быть выгодной с экономической точки зрения Покупка щпс в Москве также может быть выгодной с экономической точки зрения . Это связано с тем, что в Москве имеется большое количество поставщиков и производителей щпс Щпс купить в Москве можно по более низкой цене из-за наличия большого количества поставщиков и производителей. Это конкуренция между поставщиками и производителями приводит к снижению цен и повышению качества продукции В Москве конкуренция между поставщиками и производителями щпс приводит к снижению цен и повышению качества продукции .
В Москве имеется несколько вариантов покупки щпс Щпс купить в Москве можно через несколько вариантов . Одним из наиболее распространенных вариантов является покупка через официальные дилерские центры Одним из наиболее распространенных вариантов является покупка через официальные дилерские центры . Эти центры предлагают широкий ассортимент продукции и предоставляют гарантию качества Эти центры предлагают широкий ассортимент продукции и предоставляют гарантию качества .
Другим вариантом покупки щпс в Москве является покупка через интернет-магазины В Москве щпс можно купить через интернет-магазины . Этот вариант является удобным и позволяет выбрать щпс из широкого ассортимента продукции Щпс купить в Москве через интернет-магазины можно из широкого ассортимента продукции. Кроме того, интернет-магазины часто предлагают более низкие цены и акции Кроме того, интернет-магазины часто предлагают более низкие цены и акции .
В заключении, покупка щпс в Москве является выгодным и удобным вариантом Щпс купить в Москве очень выгодно и удобно . В Москве имеется широкий ассортимент продукции и возможность выбрать из различных вариантов покупки Щпс купить в Москве можно из широкого ассортимента продукции и через различные варианты покупки. Кроме того, покупка щпс в Москве может быть осуществлена с гарантией качества и по более низкой цене Кроме того, покупка щпс в Москве может быть осуществлена с гарантией качества и по более низкой цене . Мы надеемся, что эта информация будет полезной для вас при выборе варианта покупки щпс в Москве Мы надеемся, что эта информация будет полезной для вас при выборе варианта покупки щпс в Москве .
купить курсовая работа http://kupit-kursovuyu-23.ru/ .
сколько стоит курсовая работа по юриспруденции https://www.kupit-kursovuyu-22.ru .
написание курсовых работ на заказ цена http://www.kupit-kursovuyu-28.ru .
заказ курсовых работ заказ курсовых работ .
Бонус до 150 тысяч рублей на старте выглядит очень вкусно
https://fabi.tenil.dev/melbet-aktualnoe-rabochee-zerkalo-2025/
A cozy Kolasin Montenegro hotels for mountain lovers. Ski slopes, trekking trails, and local cuisine are nearby. Rooms are equipped with amenities, Wi-Fi, parking, and friendly staff are available to help you plan your vacation.
купить задание для студентов http://kupit-kursovuyu-22.ru/ .
Для строительных и дорожных работ можно купить щпс 0 80, обеспечив качество и сроки выполнения проекта.
Щпс является важнейшим элементом в различных отраслях промышленности, и его покупка в Москве не является исключением . Для многих компаний и частных лиц покупка щпс в Москве является необходимой задачей Для многих компаний и частных лиц покупка щпс в Москве является необходимой задачей . В статье мы рассмотрим варианты покупки щпс в Москве и их преимущества В статье мы рассмотрим варианты покупки щпс в Москве и их преимущества .
Покупка щпс в Москве может быть осуществлена через различные каналы Щпс купить в Москве можно через разные каналы. Это может включать в себя официальные дилерские центры, интернет-магазины и специализированные торговые площадки Покупка щпс в Москве может быть осуществлена через официальные дилерские центры, интернет-магазины и специализированные торговые площадки . Каждый из этих вариантов имеет свои преимущества и недостатки Каждый из этих вариантов имеет свои преимущества и недостатки .
Покупка щпс в Москве имеет ряд преимуществ Щпс купить в Москве выгодно по нескольким причинам . Одним из основных преимуществ является возможность выбрать из широкого ассортимента продукции Щпс купить в Москве можно из широкого ассортимента продукции. Это позволяет найти оптимальный вариант для конкретных потребностей Возможность выбрать щпс из широкого ассортимента продукции позволяет найти оптимальный вариант . Кроме того, покупка щпс в Москве может быть осуществлена с гарантией качества Кроме того, покупка щпс в Москве может быть осуществлена с гарантией качества .
Покупка щпс в Москве также может быть выгодной с экономической точки зрения Покупка щпс в Москве также может быть выгодной с экономической точки зрения . Это связано с тем, что в Москве имеется большое количество поставщиков и производителей щпс Щпс купить в Москве можно по более низкой цене из-за наличия большого количества поставщиков и производителей. Это конкуренция между поставщиками и производителями приводит к снижению цен и повышению качества продукции Это конкуренция между поставщиками и производителями приводит к снижению цен и повышению качества продукции .
В Москве имеется несколько вариантов покупки щпс Щпс купить в Москве можно через несколько вариантов . Одним из наиболее распространенных вариантов является покупка через официальные дилерские центры Одним из наиболее распространенных вариантов является покупка через официальные дилерские центры . Эти центры предлагают широкий ассортимент продукции и предоставляют гарантию качества Эти центры предлагают широкий ассортимент продукции и предоставляют гарантию качества .
Другим вариантом покупки щпс в Москве является покупка через интернет-магазины Щпс купить в Москве можно через интернет-магазины. Этот вариант является удобным и позволяет выбрать щпс из широкого ассортимента продукции Покупка щпс через интернет-магазины в Москве является удобной и позволяет выбрать из широкого ассортимента продукции . Кроме того, интернет-магазины часто предлагают более низкие цены и акции Кроме того, интернет-магазины часто предлагают более низкие цены и акции .
В заключении, покупка щпс в Москве является выгодным и удобным вариантом В заключении, покупка щпс в Москве является выгодным и удобным вариантом . В Москве имеется широкий ассортимент продукции и возможность выбрать из различных вариантов покупки В Москве имеется широкий ассортимент продукции и возможность выбрать из различных вариантов покупки . Кроме того, покупка щпс в Москве может быть осуществлена с гарантией качества и по более низкой цене Щпс купить в Москве можно с гарантией качества и по более низкой цене. Мы надеемся, что эта информация будет полезной для вас при выборе варианта покупки щпс в Москве Эта информация должна быть полезной для вас при выборе варианта покупки щпс в Москве .
гидроизоляция подвала гидроизоляция подвала .
Обновили дизайн приложения, стало ещё удобнее
https://respogo.com/melbet-zerkalo-na-segodnya/
усиление проема углеволокном усиление проема углеволокном .
Для успешного бизнеса в современном цифровом мире важно учитывать продвижение сайта в сша, чтобы достичь целевой аудитории и увеличить онлайн-присутствие на американском рынке.
Расширение бизнеса на американском рынке через продвижение сайтов в США является перспективным направлением. Это связано с тем, что американский рынок является одним из самых больших и перспективных рынков в мире американский рынок занимает лидирующие позиции среди мировых рынков . Для успешного продвижения сайтов в США необходимо учитывать многие факторы, включая культурные и языковые особенности культурные и языковые особенности американского рынка требуют тщательного изучения.
Продвижение сайтов в США также требует глубокого понимания местного законодательства и нормативных актов местное законодательство и нормативные акты в США имеют особое значение для продвижения сайтов. Это включает в себя соблюдение требований по защите данных и конфиденциальности для продвижения сайтов в США необходимо обеспечить защиту данных и конфиденциальности пользователей . Кроме того, необходимо учитывать особенности поисковых систем и алгоритмов ранжирования для продвижения сайтов в США необходимо понимать, как работают поисковые системы и алгоритмы ранжирования .
Одной из ключевых стратегий продвижения сайтов в США является создание высококачественного и релевантного контента создание релевантного и качественного контента имеет важное значение для продвижения сайтов в США. Этот контент должен быть адаптирован к местному рынку и соответствовать интересам и потребностям американской аудитории контент должен быть адаптирован к местному рынку и соответствовать интересам и потребностям американской аудитории . Кроме того, для продвижения сайтов в США можно использовать различные маркетинговые инструменты и платформы для продвижения сайтов в США можно использовать различные маркетинговые инструменты и платформы .
Использование социальных сетей также является эффективной стратегией продвижения сайтов в США использование социальных сетей является эффективной стратегией продвижения сайтов в США . Социальные сети позволяют достигать целевой аудитории и повышать узнаваемость бренда социальные сети позволяют достигать целевой аудитории и повышать узнаваемость бренда . Кроме того, для продвижения сайтов в США необходимо постоянно отслеживать и анализировать результаты продвижения постоянный анализ и отслеживание результатов продвижения имеют важное значение для продвижения сайтов в США .
Оптимизация сайтов для американского рынка включает в себя несколько ключевых аспектов оптимизация сайтов для американского рынка включает в себя несколько ключевых аспектов . Одним из важных аспектов является создание удобного и интуитивного интерфейса создание удобного интерфейса имеет важное значение для продвижения сайтов в США. Это включает в себя организацию контента, навигации и других элементов сайта в соответствии с предпочтениями американской аудитории создание интерфейса, адаптированного к американской аудитории, требует глубокого понимания местной культуры и поведения.
Кроме того, для оптимизации сайтов для американского рынка необходимо обеспечить высокую скорость загрузки и стабильность сайта для оптимизации сайтов для американского рынка необходимо обеспечить высокую скорость загрузки и стабильность сайта . Это включает в себя выбор подходящего хостинга, настройку кэширования и оптимизацию графики и других медиа-элементов обеспечение высокой скорости загрузки и стабильности сайта является важным фактором для продвижения сайтов в США. Кроме того, необходимо обеспечить безопасность сайта и защиту данных пользователей для продвижения сайтов в США необходимо обеспечить безопасность сайта и защиту данных пользователей .
Анализ и оценка эффективности продвижения сайтов в США является важным аспектом маркетинговой стратегии анализ и оценка эффективности продвижения сайтов в США является важным аспектом маркетинговой стратегии . Это включает в себя использование различных инструментов и метрик для оценки эффективности продвижения для продвижения сайтов в США необходимо использовать различные инструменты и метрики для оценки эффективности продвижения .
Одним из ключевых инструментов для анализа эффективности продвижения является Google Analytics Google Analytics предоставляет??ную информацию о поведении пользователей и эффективности продвижения. Это позволяет оценить трафик на сайт, поведение пользователей и конверсию анализ трафика на сайт, поведения пользователей и конверсии позволяет понять эффективность продвижения и принять обоснованные решения. Кроме того, необходимо постоянно корректировать и улучшать маркетинговые стратегии на основе результатов анализа необходимо постоянно корректировать и улучшать маркетинговые стратегии на основе результатов анализа .