Hello there! Your guy Zokomon is back, and today we’re diving into the world of Blockchain: How to Find Bugs in Web3? Blockchain is no longer just about Bitcoin and crypto trading—it’s becoming a crucial player in securing the digital world.
But how exactly does blockchain change the game for cybersecurity? Let’s explore!
What Makes Blockchain Secure?
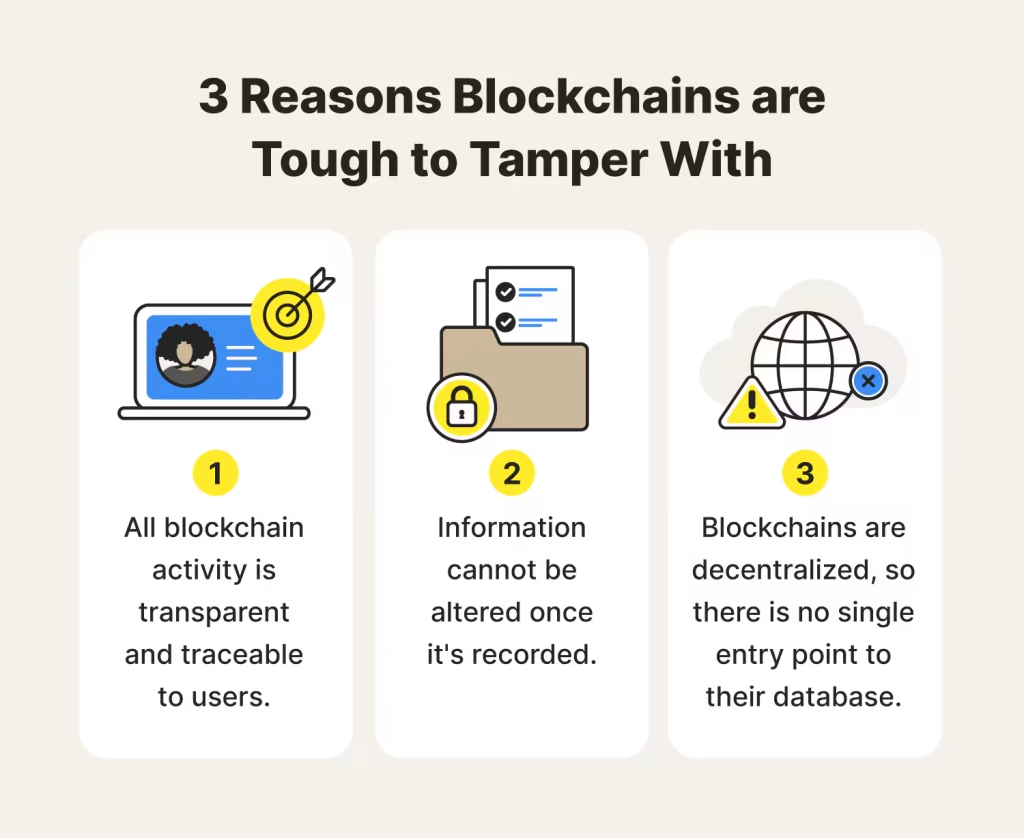
At its core, blockchain is like a digital ledger that stores information in a way that’s nearly impossible to tamper with. Here’s why:
1) Decentralization:
. Blockchain data isn’t stored in a single location. Instead, it’s distributed across multiple nodes, making it resistant to attacks.
. There’s no central server for hackers to target.
2) Immutability:
. Once a transaction or record is added to the blockchain, it can’t be altered.
. This ensures data integrity and makes unauthorized changes virtually impossible.
3) Transparency:
. Blockchain allows everyone in the network to verify transactions.
. While the data is encrypted, its visibility builds trust and reduces fraud.
Challenges Blockchain Faces in Cybersecurity
Of course, no technology is perfect, and blockchain has its own challenges:
1) Scalability Issues:
. Blockchain networks can be slow when processing a large number of transactions.
. This limits its use for systems that require high-speed operations.
2) High Energy Consumption:
. Some blockchain models, like proof-of-work (PoW), consume significant amounts of energy.
. This raises questions about sustainability.
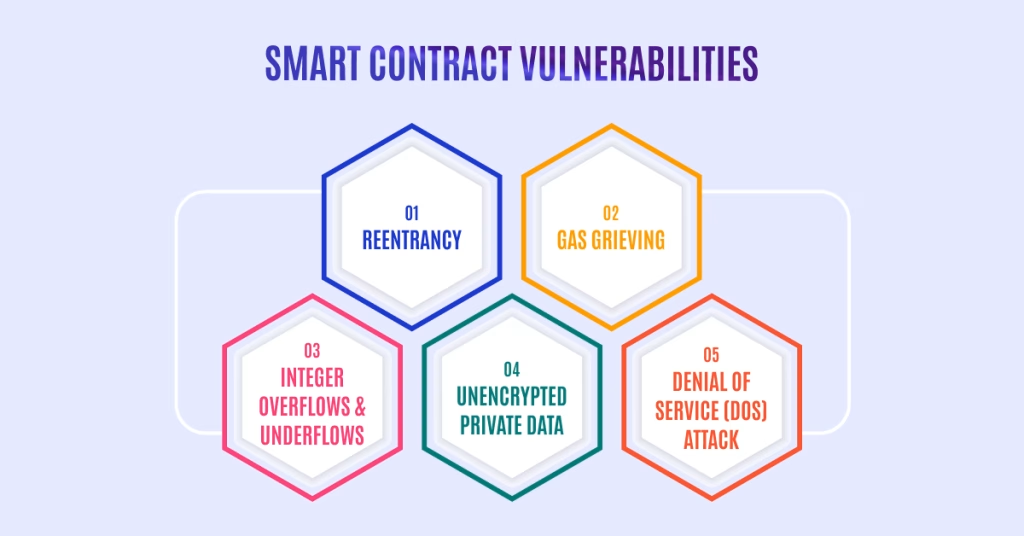
3) Smart Contract Vulnerabilities:
. While smart contracts automate processes, they can have bugs that hackers exploit.
. Ethical hackers have a crucial role in securing these contracts.
Where Ethical Hackers Fit In
Blockchain might seem foolproof, but like any technology, it’s not invincible. This is where ethical hackers step in:

1)Auditing Smart Contracts:
. Smart contracts are a prime target for hackers. Ethical hackers can analyze and test them to ensure they’re secure.
. Tools like Mythril and Slither are great for this.
2)Testing Blockchain Networks:
. Penetration testing on blockchain networks can help identify weaknesses in consensus mechanisms or node communication.
3)Educating Organizations:
. Many companies are still new to blockchain. Ethical hackers can guide them on best practices for securing their systems.
Future Trends: Blockchain and Cybersecurity
As blockchain adoption grows, its impact on cybersecurity will continue to expand. Here’s what we can expect in the near future:
1)Blockchain-Backed Authentication:
. Passwordless authentication systems using blockchain are already in development, offering more secure access controls.
2)Decentralized Threat Intelligence:
. Blockchain can be used to create shared threat intelligence platforms where organizations exchange real-time data about cyber threats.
3)Integration with AI:
. Combining blockchain with AI will enhance cybersecurity by providing smarter threat detection and more secure data storage.
4)Blockchain for Supply Chain Security:
. Blockchain’s transparency ensures that every step in a supply chain is traceable, reducing the risk of tampering or counterfeit goods.Final Thoughts
Blockchain is revolutionizing cybersecurity, offering solutions to some of the most persistent challenges in the digital world. While it’s not without its flaws, its potential is undeniable. As ethical hackers, we have an exciting opportunity to contribute to this transformation by securing blockchain systems and ensuring their reliability.
That’s all for today! Let me know your thoughts on blockchain—do you see it as the future of cybersecurity? In the next blog, we’ll explore Most Important tools in Bug Bounty as per DevSecOps.
Till that you can explore my previous Blog on Developers Shocked: AI Now Writes, Fixes, and Explains Code Instantly!
Stay tuned! ❤️



Thanks for sharing. I read many of your blog posts, cool, your blog is very good.