Finding your first bug in bug bounty hunting can be challenging, but don’t worry you’re not alone! You know why it’s tricky?
Because you might have already stumbled upon a bug without even realizing it! Sometimes, it’s easy to miss the signs or feel stuck after trying all the methods you know. Don’t let those missed opportunities discourage you, though. With the right approach, you can land your first bug and start your journey as a successful ethical hacker.
Here’s a step-by-step guide by your Friend ZOKOMON to help you find your first bug and get good at bug bounties in 2025.

Step 1: Research the Target’s Technology
Before diving into bug bounty hunting, take time to understand the technology stack behind your target website. Is it running on an Apache server? Is it using specific frameworks or content management systems?
This information will guide your approach. For example, knowing the server type could hint at potential vulnerabilities or help you craft specific payloads.
Step 2: Fire Up Burp Suite
Always launch Burp Suite before starting! Think of it like brushing your teeth in the morning—it’s a must.
Pro Tip: The free community version of Burp Suite is enough to help you find your first bug. Don’t let the tools intimidate you; it’s simpler than it seems. Just start intercepting traffic and get familiar with how requests flow.
Keyword Note: Tools like Burp Suite are essential for any beginner in bug bounty hunting.
Step 3: Understand the Requests
When you analyze traffic in Burp Suite, you’ll come across different types of HTTP requests. Always check the Host Name in the request to ensure you’re testing the correct domain and not going off track.
If you’re confused by a request, don’t hesitate—copy the whole request and ask ChatGPT to explain it to you. Just paste it in and add, “Explain below.” ChatGPT is your best friend here. Use it as a learning tool!
Keyword Note: Learning how to analyze HTTP requests is one of the top bug bounty tips for beginners.
Step 4: Target Queries and Stay Focused
Query-based targets are a great starting point. For example:
https://example.com?page=query
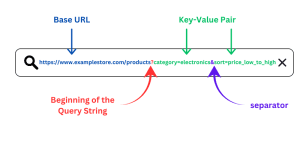
When you see query-based URLs, think of vulnerabilities like:
- XSS (Cross-Site Scripting)
- SQL Injection
- CRLF Injection
- Path Traversal
Instead of testing every possible vulnerability, focus on a few selective attacks and analyze their responses.
Avoid Automated Tools for Now:
While automated tools might seem tempting, they often lead to IP blocks or wasted time, especially if you don’t fully understand the responses. Use manual testing to build your knowledge first. Once you’re familiar with concepts like WAF (Web Application Firewall), User-Agent headers, and cookies, you’ll be better equipped to use tools effectively.
Keyword Note: For ethical hacking beginners, focusing on manual testing can help you avoid common mistakes in bug bounty hunting.
Step 5: Start Small and Build Confidence
Begin with selective attacks. Master a few techniques and fully understand what’s happening under the hood. It’s best to practice on targets that don’t offer bounties initially—this reduces pressure and lets you learn at your own pace.
When you feel comfortable, move on to paid bug bounty programs. Paid programs can be tougher, but they’re not impossible. With persistence, a bit of luck, and a keen eye, you could be the one to find a bug others missed.
Keyword Note: Start with beginner-friendly bug bounty platforms before diving into advanced programs.
A Word of Encouragement
Getting started is the hardest part, but don’t give up! Your first bug will come when you least expect it. Just stay consistent, keep learning, and don’t be afraid to make mistakes—they’re part of the process.

I have more to share, but I’ll save that for the next blog , “How I found my first bug” and more tips to help you succeed in bug bounty hunting.